- Главная
- Разное
- Бизнес и предпринимательство
- Образование
- Развлечения
- Государство
- Спорт
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Религиоведение
- Черчение
- Физкультура
- ИЗО
- Психология
- Социология
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Геометрия
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
Что такое findslide.org?
FindSlide.org - это сайт презентаций, докладов, шаблонов в формате PowerPoint.
Обратная связь
Email: Нажмите что бы посмотреть
Презентация на тему Return to libc attack
Содержание
- 2. What is libc ?Prog.elflibc.sold-linux-x86-64.so55cdfefe30007f11866a70007f1186c82000
- 3. What is libc ?Prog.elf .textProg.elf .dataProg.elf .bssProg.elf .pltlibc.so .textlibc.so .datalibc.so .bsslibc.so .plt55cdfefe30007f11866a7000
- 4. What is libc ?// libc.soprintf … retPuts … retSystem … ret// You programmain call printf retplt: jmp printf
- 5. ret2libcWe know version of libc.soWe know address of libc.soWe know any function address at libc.so
- 6. ret2libcint main (){ char buf [16]; gets(buf);}ret from mainebp before main char buf[16]
- 7. ret2libc.stack ; segment with stackMain:push ebpmov ebp,
- 8. ret2libc.stack ; segment with stackRet from main?eipold
- 9. ret2libc.stack ; segment with stackRet from main?eipold
- 10. ret2libc.stack ; segment with stackRet from main?eipold
- 11. ret2libc.stack ; segment with stackRet from main?eipold
- 12. ret2libc.stack ; segment with stackRet from main?eipold
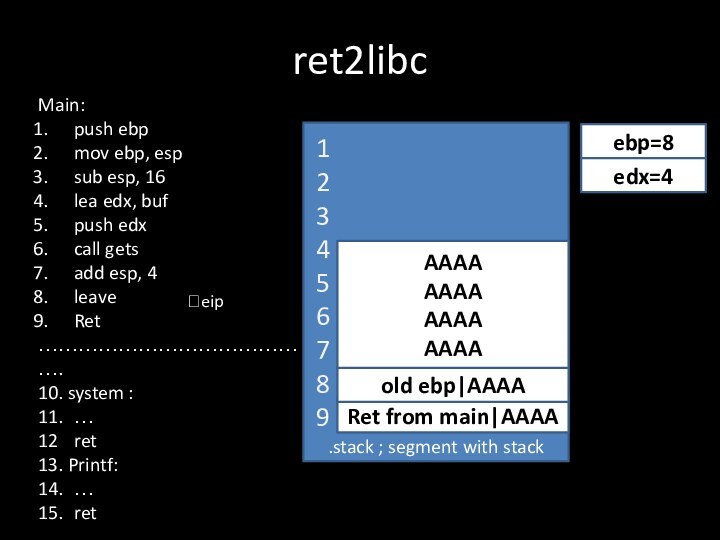
- 13. ret2libc.stack ; segment with stackRet from main|AAAA?eipold
- 14. ret2libc.stack ; segment with stackRet from main|AAAA?eipold
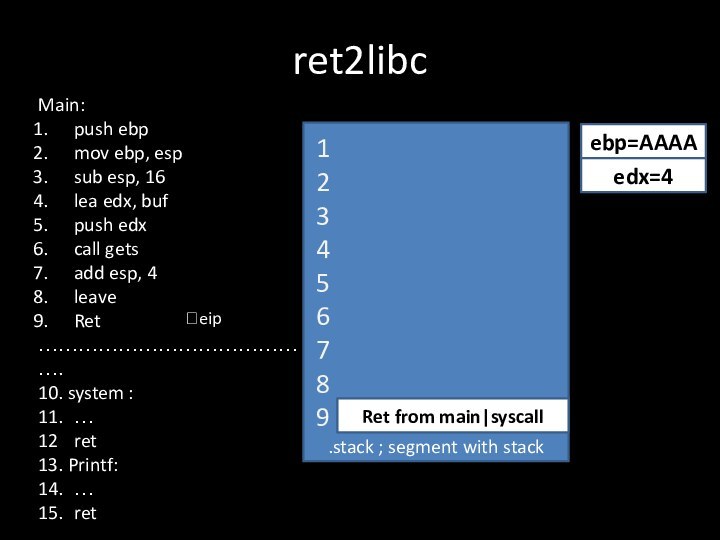
- 15. ret2libc.stack ; segment with stackRet from main|syscall?eipebp=AAAA123456789edx=4Main:push
- 16. system =?
- 17. system =printf-CONST
- 18. system =libc.so:system
- 19. ret2libc.stack ; segment with stackRet from main|syscall?eipebp=AAAA123456789edx=4Main:push
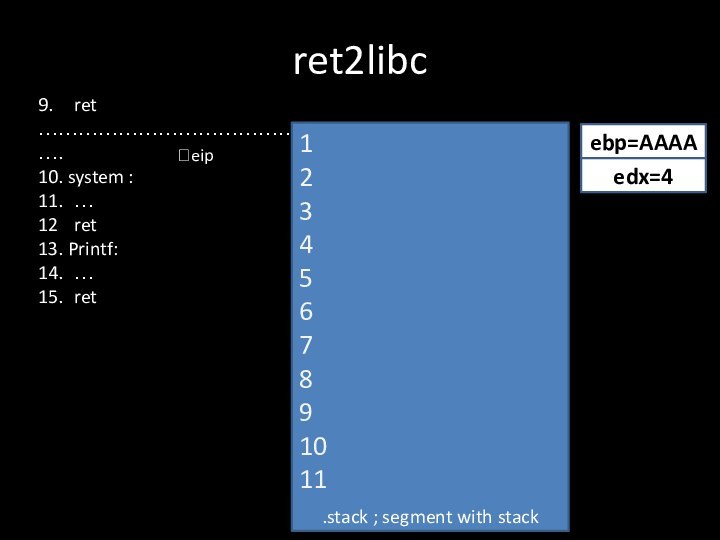
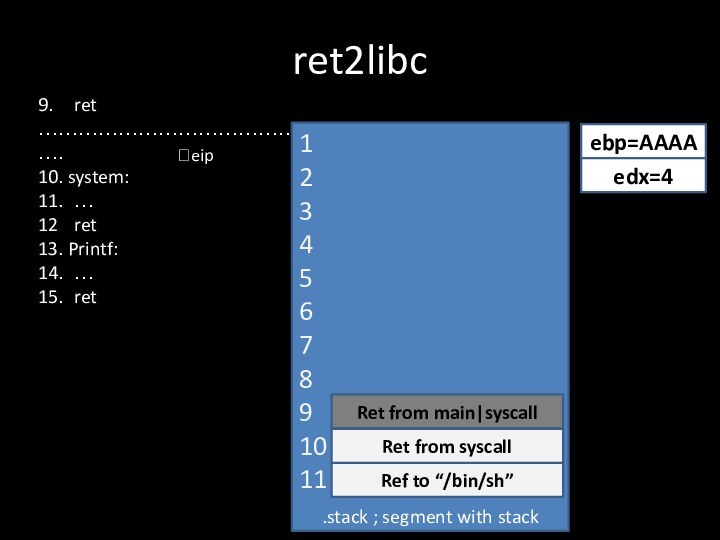
- 20. 9. ret…………………………………….10. system :11. …12 ret13. Printf:14. …15. retret2libc.stack ; segment with stack?eipebp=AAAA1234567891011edx=4
- 21. 9. ret…………………………………….10. system:11. …12 ret13. Printf:14. …15. retret2libc.stack ; segment with stack?eipebp=AAAA1234567891011edx=4Ret from main|syscallRef to “/bin/sh”Ret from syscall
- 22. Where is /bin/sh ?
- 23. Where is /bin/sh ?ropchain
- 24. What about randomization/proc/sys/kernel/randomize_va_space0 – No randomization. Everything
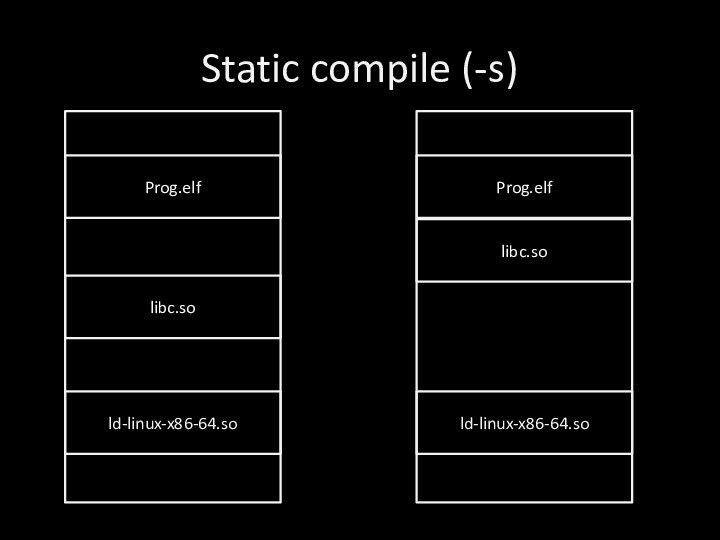
- 25. Static compileProg.elflibc.sold-linux-x86-64.so55cdfefe30007f11866a70007f1186c82000
- 26. Static compile (-s)Prog.elflibc.sold-linux-x86-64.soProg.elflibc.sold-linux-x86-64.so
- 27. Static compile (-s)Works in any linux with
- 28. GDB commandsgdb:maint info sections – show sectionsshell
- 29. Скачать презентацию
- 30. Похожие презентации
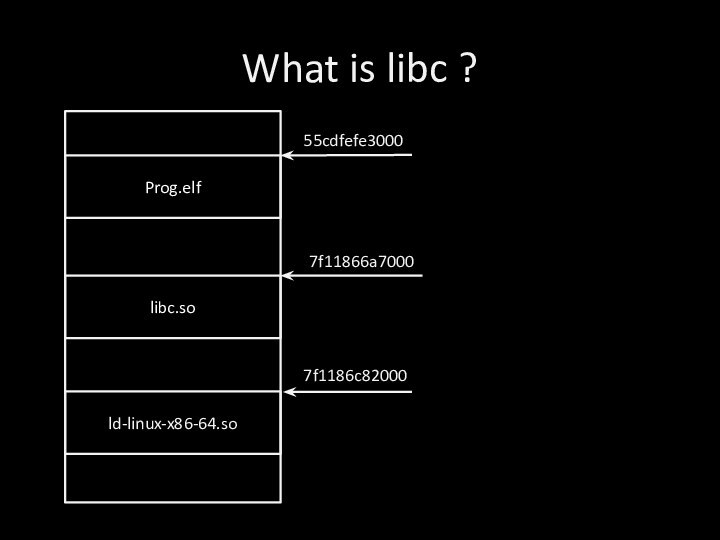
What is libc ?Prog.elflibc.sold-linux-x86-64.so55cdfefe30007f11866a70007f1186c82000




![Return to libc attack ret2libcint main (){ char buf [16]; gets(buf);}ret from mainebp before main char buf[16]](/img/tmb/15/1471565/d61a229818ee8ff13fc9ec892ef0d8b9-720x.jpg)


![Return to libc attack ret2libc.stack ; segment with stackRet from main?eipold ebpebp=8123456789Char buf[16]Main:push ebpmov ebp, espsub](/img/tmb/15/1471565/288b1372c6841fa17205e64055902703-720x.jpg)
![Return to libc attack ret2libc.stack ; segment with stackRet from main?eipold ebpebp=8123456789Char buf[16]edx=4Main:push ebpmov ebp, espsub](/img/tmb/15/1471565/ff47dd20a932c3115bf8ed10f1fa0504-720x.jpg)
![Return to libc attack ret2libc.stack ; segment with stackRet from main?eipold ebpebp=8123456789Char buf[16]edx=44Main:push ebpmov ebp, espsub](/img/tmb/15/1471565/1df7c941fecea7a294aa72172c9842fc-720x.jpg)









![Return to libc attack Now#include int main(){ char buf[16]; gets(buf); puts(buf); return 0;}EXPLOIT this](/img/tmb/15/1471565/8b8505c3646da1008748e7138f4d9710-720x.jpg)
Слайд 4
What is libc ?
// libc.so
printf
…
ret
Puts
…
ret
System
…
ret
// You program
main
call printf
ret
plt:
jmp
printf
Слайд 5
ret2libc
We know version of libc.so
We know address of
libc.so
We know any function address at libc.so
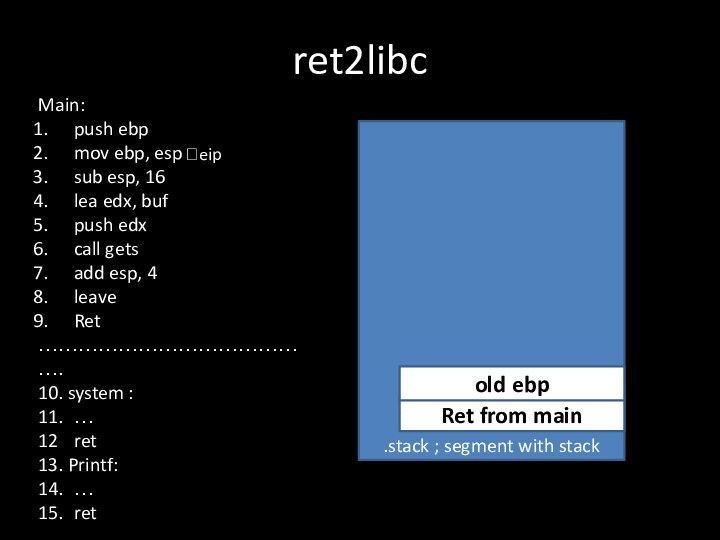
Слайд 7
ret2libc
.stack ; segment with stack
Main:
push ebp
mov ebp, esp
sub
esp, 16
lea edx, buf
push edx
call gets
add esp, 4
leave
Ret
…………………………………….
10. system
:11. …
12 ret
13. Printf:
14. …
15. ret
Ret from main
?eip
Слайд 8
ret2libc
.stack ; segment with stack
Ret from main
?eip
old ebp
Main:
push
ebp
mov ebp, esp
sub esp, 16
lea edx, buf
push edx
call gets
add
esp, 4leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 9
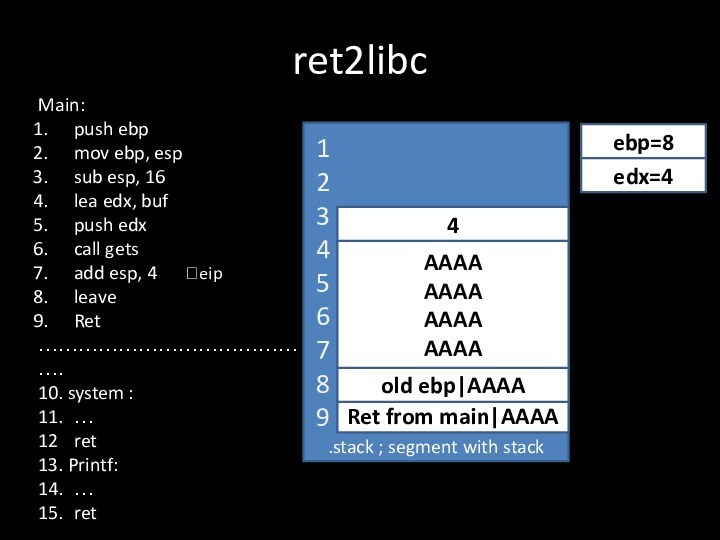
ret2libc
.stack ; segment with stack
Ret from main
?eip
old ebp
ebp=8
1
2
3
4
5
6
7
8
9
Main:
push
ebp
mov ebp, esp
sub esp, 16
lea edx, buf
push edx
call gets
add
esp, 4leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 10
ret2libc
.stack ; segment with stack
Ret from main
?eip
old ebp
ebp=8
1
2
3
4
5
6
7
8
9
Char
buf[16]
Main:
push ebp
mov ebp, esp
sub esp, 16
lea edx, buf
push edx
call
getsadd esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 11
ret2libc
.stack ; segment with stack
Ret from main
?eip
old ebp
ebp=8
1
2
3
4
5
6
7
8
9
Char
buf[16]
edx=4
Main:
push ebp
mov ebp, esp
sub esp, 16
lea edx, buf
push edx
call
getsadd esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 12
ret2libc
.stack ; segment with stack
Ret from main
?eip
old ebp
ebp=8
1
2
3
4
5
6
7
8
9
Char
buf[16]
edx=4
4
Main:
push ebp
mov ebp, esp
sub esp, 16
lea edx, buf
push edx
call
getsadd esp, 4
leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 13
ret2libc
.stack ; segment with stack
Ret from main|AAAA
?eip
old ebp|AAAA
ebp=8
1
2
3
4
5
6
7
8
9
AAAA
AAAA
AAAA
AAAA
edx=4
4
Main:
push
ebp
mov ebp, esp
sub esp, 16
lea edx, buf
push edx
call gets
add
esp, 4leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 14
ret2libc
.stack ; segment with stack
Ret from main|AAAA
?eip
old ebp|AAAA
ebp=8
1
2
3
4
5
6
7
8
9
AAAA
AAAA
AAAA
AAAA
edx=4
Main:
push
ebp
mov ebp, esp
sub esp, 16
lea edx, buf
push edx
call gets
add
esp, 4leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 15
ret2libc
.stack ; segment with stack
Ret from main|syscall
?eip
ebp=AAAA
1
2
3
4
5
6
7
8
9
edx=4
Main:
push ebp
mov
ebp, esp
sub esp, 16
lea edx, buf
push edx
call gets
add esp,
4leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 19
ret2libc
.stack ; segment with stack
Ret from main|syscall
?eip
ebp=AAAA
1
2
3
4
5
6
7
8
9
edx=4
Main:
push ebp
mov
ebp, esp
sub esp, 16
lea edx, buf
push edx
call gets
add esp,
4leave
Ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
Слайд 20
9. ret
…………………………………….
10. system :
11. …
12 ret
13. Printf:
14. …
15. ret
ret2libc
.stack ; segment with
stack
?eip
ebp=AAAA
1
2
3
4
5
6
7
8
9
10
11
edx=4
Слайд 21
9. ret
…………………………………….
10. system:
11. …
12 ret
13. Printf:
14. …
15. ret
ret2libc
.stack ; segment with stack
?eip
ebp=AAAA
1
2
3
4
5
6
7
8
9
10
11
edx=4
Ret
from main|syscall
Ref to “/bin/sh”
Ret from syscall
Слайд 24
What about randomization
/proc/sys/kernel/randomize_va_space
0 – No randomization. Everything is
static.
1 – Conservative randomization. Shared libraries, stack, mmap(), VDSO
and heap are randomized.2 – Full randomization. In addition to elements listed in the previous point, memory managed through brk() is also randomized.
Слайд 27
Static compile (-s)
Works in any linux with any
libc installed
ELF contains entire libraries
Very big binary
You can find
many functions an gadgets - dangerous
Слайд 28
GDB commands
gdb:
maint info sections – show sections
shell ps
aux | grep test – show process pid
cat /proc/[PID]/maps
– show sections of processfind [START ADDRESS], [END ADDRESS], “[STRING]”
shell:
ldd test