Слайд 2
At a Glance
Company Profil
We are an
international Company headquartered in London with a 16 year
international track-record within the IT-Infrastructure and Software Development Business. Germany is appointed as the European Business Hub
Our Product
With our new NOTARY-SERVER Technology we ensure a new level of data-/ transmission security
Facts and Figures
Founded in: 1998
Employees: ca. 190 employees
CEO: Eduard Rubin
CEO Germany: Nino Messaoud
At a Glance
Слайд 3
Threats for Data and Transaction security
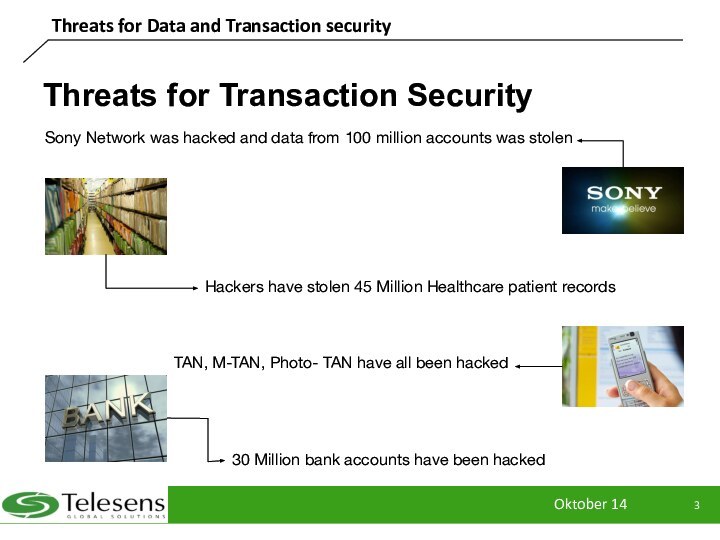
Hackers have stolen
45 Million Healthcare patient records
Sony Network was hacked and
data from 100 million accounts was stolen
30 Million bank accounts have been hacked
TAN, M-TAN, Photo- TAN have all been hacked
Threats for Transaction Security
Слайд 5
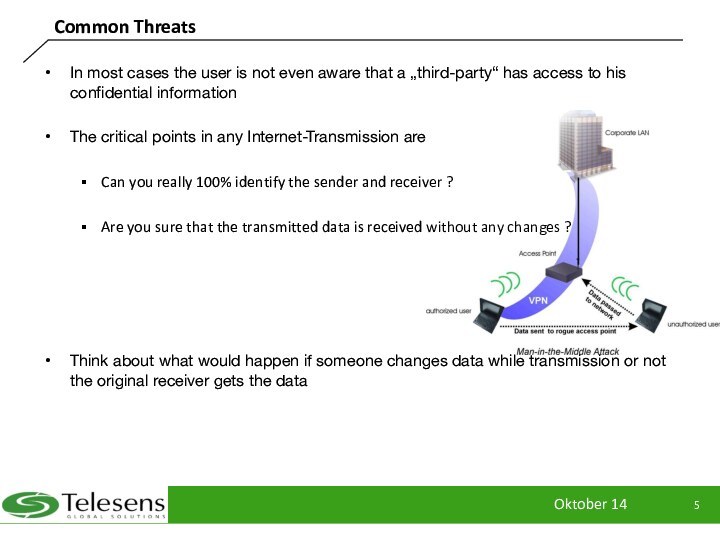
In most cases the user is not even
aware that a „third-party“ has access to his confidential
information
The critical points in any Internet-Transmission are
Can you really 100% identify the sender and receiver ?
Are you sure that the transmitted data is received without any changes ?
Think about what would happen if someone changes data while transmission or not the original receiver gets the data
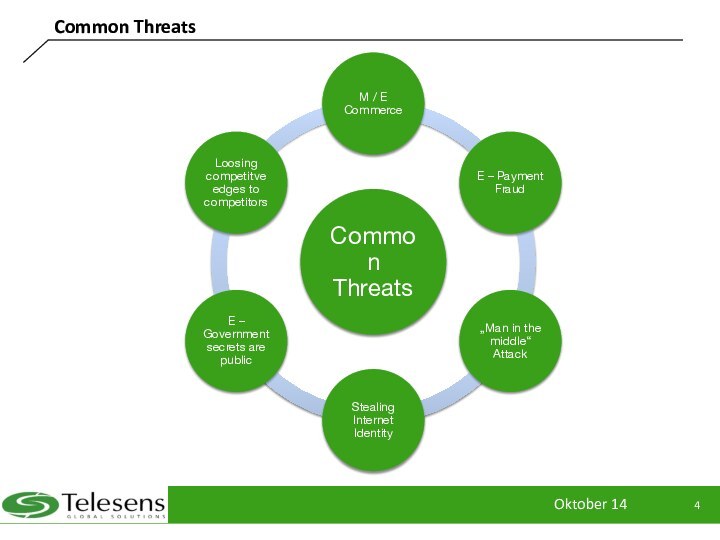
Common Threats
Слайд 6
European Banks and Insurance Companies are losing hundreds
of
million Euros / Year because of fraudulence
Within some
E-Government Systems, fraud has opened the doors to faked
documents, driving licenses etc.
Within the Healthcare and Telemedicine Industry, genuine data can save lives
Due to industrial espionage, companies are losing funds, competitive edges etc.
Provide yourself and/or your clients an environment with maximum Security
Protect yourself and/or your clients against fraud and against recourse rights
Common Threats
Слайд 7
What can Telesens do for you?
Notary Server Technology
We
have developed a technology, which provides you with the
highest possible security standards to avoid the aforementioned threats
With the usage of our NOTARY-SERVER Technology you can ensure the following:
Слайд 8
How it works
Telesens has developed a new, innovative
security and identification solution that enables all online transactions
and interactions to be conducted securely.
The unique characteristic of this solution is the sole use of INDIVIDUAL KEYS.
There is not one general key but a distinctive key for every transaction.
Transactions can only be conducted by users that have been registered as well as clearly identified with their hardware and as a person.
How it works
Слайд 10
The Requirements
How it works
Desktop Devices
and/or
Слайд 11
The Process
NOTARY-SERVER
The Notary Server only knows the encrypted
identity of the user and corresponding data. Only in
the communication with the Transaction Server, it is able to provide the requested information. Each Server without the other is not able to provide any kind of information.
System of your Company
How it works
Слайд 12
The Telesens Messenger – “Tutus”
Telesens Messenger
Слайд 13
The advantages to existing Products
The NOTARY-SERVER Technology can
be used as a product or as a core
technology
in addition to your existing products.
Due to the combination of different keys & items, the
Sender / Receiver is identified 100%.
No information can be changed during transmission. What you send is
what the participant receives.
No common key & technology for all users and scenarios.
Each customer gets his own NOTARY-SERVER.
Place the NOTARY-SERVER within your own Server-Farm or inside a Computing Center.
What makes us different
Слайд 14
What is different to other solutions?
Instead of using
third party tools like “Key Generating” devices, you can
use YOUR standard device for all purposes.
The handling is very easy. Use your personal QR-Code to start any kind of action depending on your provider.
You do not need to link your hardware device to e.g. your credit card, etc.
It works with any known hardware on the major operating systems like Windows©, Android© and IOS©.
What makes us different
Слайд 15
What is different to other solutions?
No one –
not even the provider or telecommunication provider – can
read your messages and/ or content of transactions.
“Man in the Middle” or “Brute-Force Attacks” can not harm you. These are the common attacks to steal sensitive data.
TAN-Services – even to registered mobile device have been cracked. The Notary Server protects you against those attacks.
Compared to other encryption solutions: How do you know if your recipient is the dedicated person? With the Notary Server, the recipient is 100% identified.
What makes us different
Слайд 16
ProFix – Our latest customer
ProFix provides it
services to a wide client base
250+ Banks in
14 countries which now use the NOTARY SERVER technology to secure their transactions
Profix provides services like
International Money Transfer
SWIFT
EastNets Products
A customized version of the Telesens Messenger „Tutus“ will be used as „Payment Instrument“ to transfer money
Latest News
Слайд 17
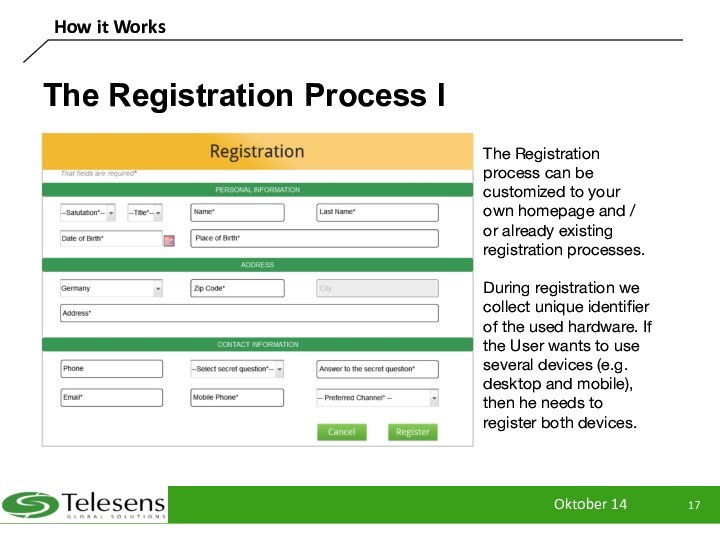
The Registration Process I
The Registration process can be
customized to your own homepage and / or already
existing registration processes.
During registration we collect unique identifier of the used hardware. If the User wants to use several devices (e.g. desktop and mobile), then he needs to register both devices.
How it Works
Слайд 18
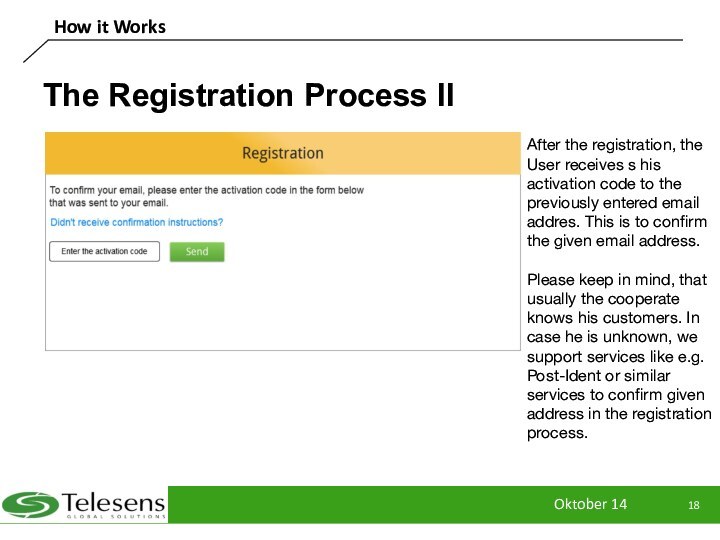
The Registration Process II
How it Works
After the registration,
the User receives s his activation code to the
previously entered email addres. This is to confirm the given email address.
Please keep in mind, that usually the cooperate knows his customers. In case he is unknown, we support services like e.g. Post-Ident or similar services to confirm given address in the registration process.
Слайд 19
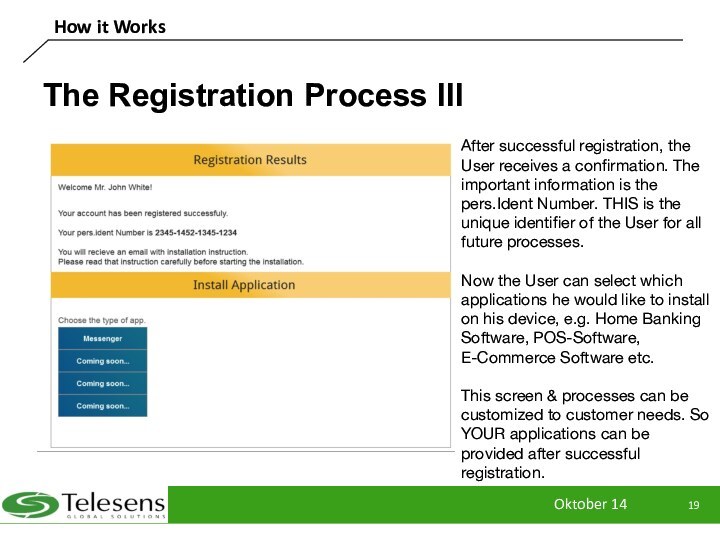
The Registration Process III
How it Works
After successful registration,
the User receives a confirmation. The important information is
the pers.Ident Number. THIS is the unique identifier of the User for all future processes.
Now the User can select which applications he would like to install on his device, e.g. Home Banking Software, POS-Software, E-Commerce Software etc.
This screen & processes can be customized to customer needs. So YOUR applications can be provided after successful registration.
Слайд 20
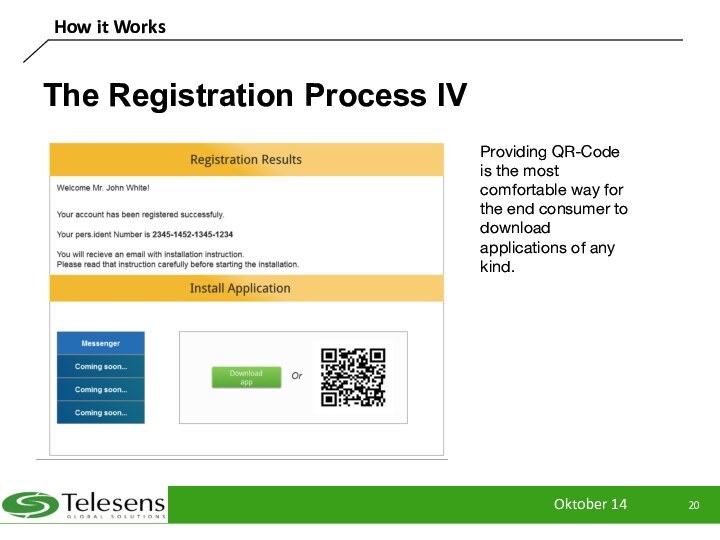
The Registration Process IV
How it Works
Providing QR-Code is
the most comfortable way for the end consumer to
download applications of any kind.
Слайд 21
The Mobile Device Registration (I)
How it Works
Now the
User is able to launch the – on the
Notary Server High-Security Technology based – Messenger. This Messenger can be customized to your individual needs and CI.
In the first Step – first launch of the Messenger – the User has to select the language. Due to our architecture, we are able to support any desired language.
Слайд 22
The Mobile Device Registration (II)
How it Works
Now
the User has to enter the previously provided pers.Ident
Number and has to select a personal password. The password is needed to launch the application.
Слайд 23
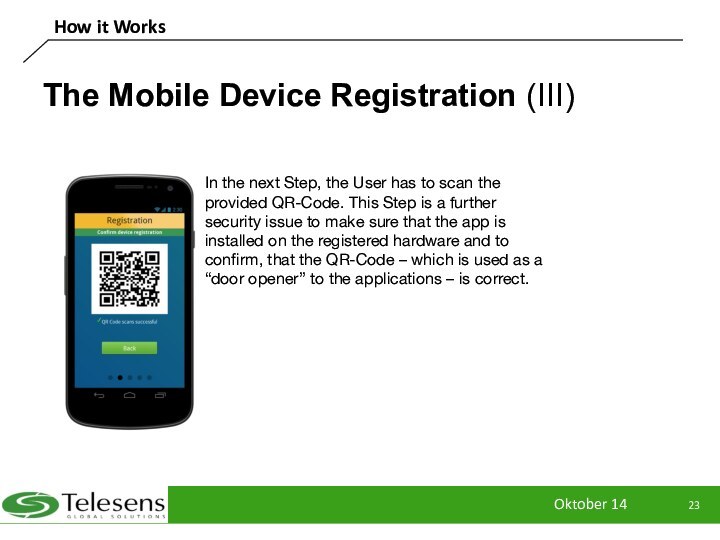
The Mobile Device Registration (III)
How it Works
In the
next Step, the User has to scan the provided
QR-Code. This Step is a further security issue to make sure that the app is installed on the registered hardware and to confirm, that the QR-Code – which is used as a “door opener” to the applications – is correct.
Слайд 24
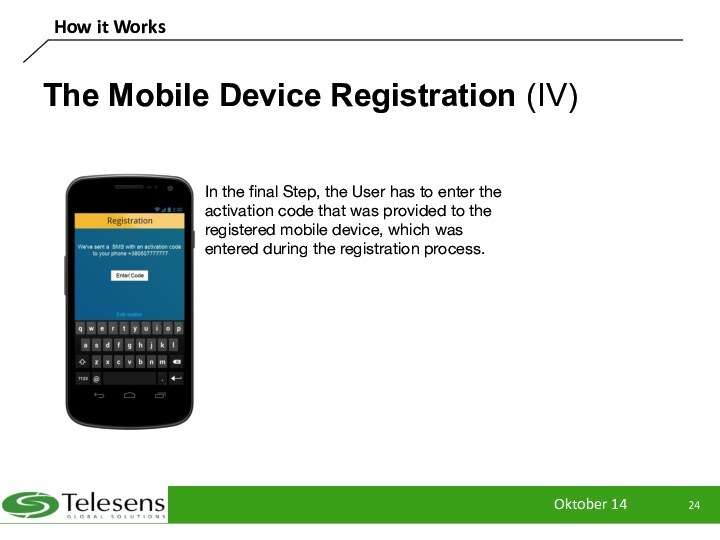
The Mobile Device Registration (IV)
How it Works
In the
final Step, the User has to enter the activation
code that was provided to the registered mobile device, which was entered during the registration process.
Слайд 25
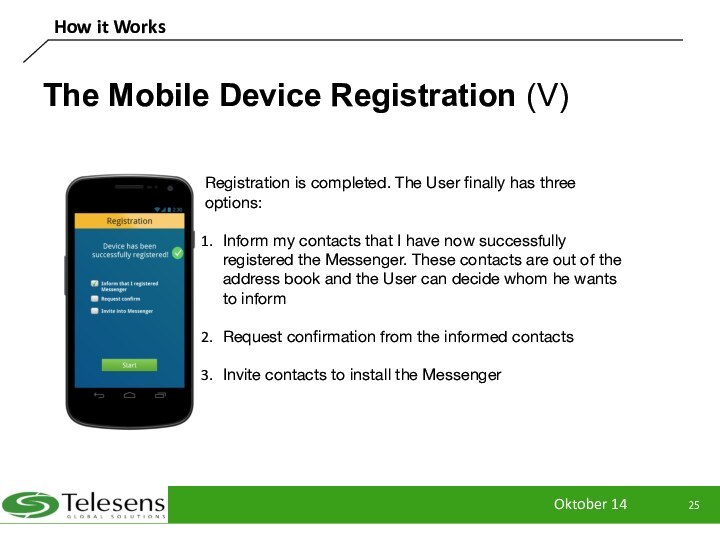
The Mobile Device Registration (V)
How it Works
Registration is
completed. The User finally has three options:
Inform my contacts
that I have now successfully registered the Messenger. These contacts are out of the address book and the User can decide whom he wants to inform
Request confirmation from the informed contacts
Invite contacts to install the Messenger
Слайд 26
The Application (I)
How it Works
In the address book,
the User can decide whom to invite, whom to
block, to receive information who is already registered etc.
Слайд 27
The Application (II)
How it Works
Furthermore, he can query
his contacts by Messenger Contacts, contacts where he as
sent invitation to, contacts where he is waiting for confirmation etc.
Слайд 28
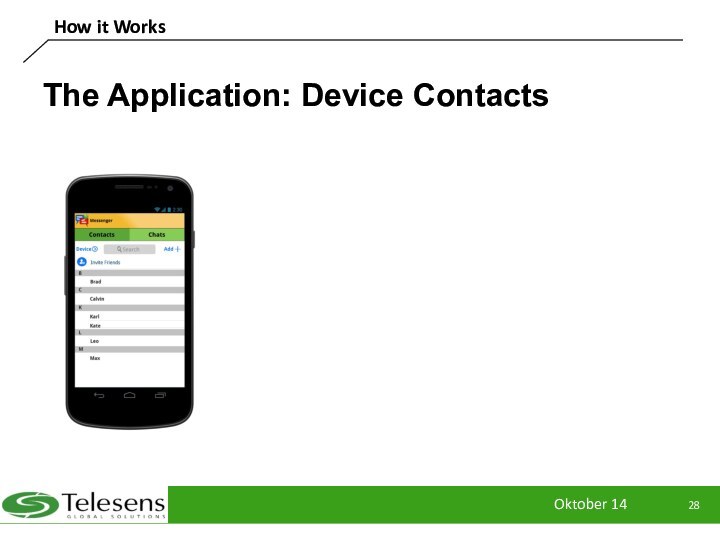
The Application: Device Contacts
How it Works
Слайд 29
The Application: Messenger Contacts
How it Works
Слайд 30
The Application: Contact Invitation
How it Works
Слайд 31
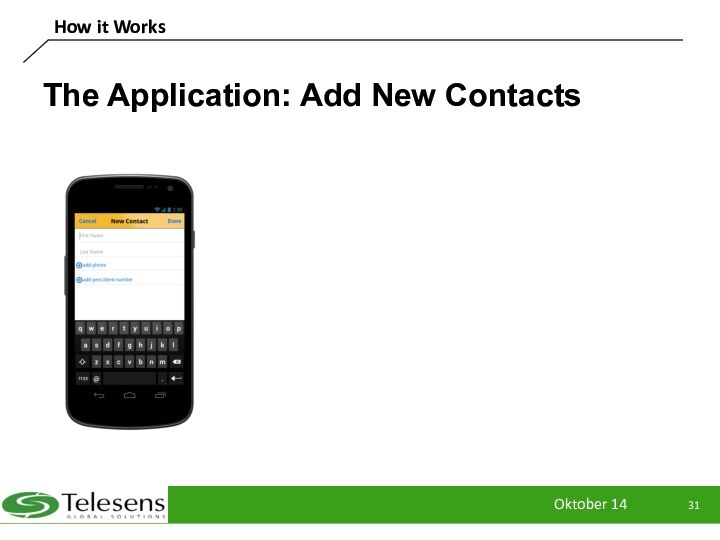
The Application: Add New Contacts
How it Works
Слайд 32
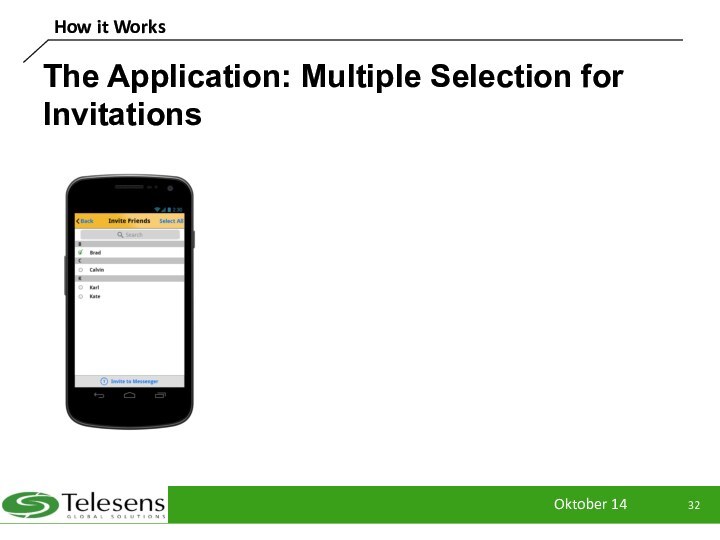
The Application: Multiple Selection for Invitations
How it Works
Слайд 33
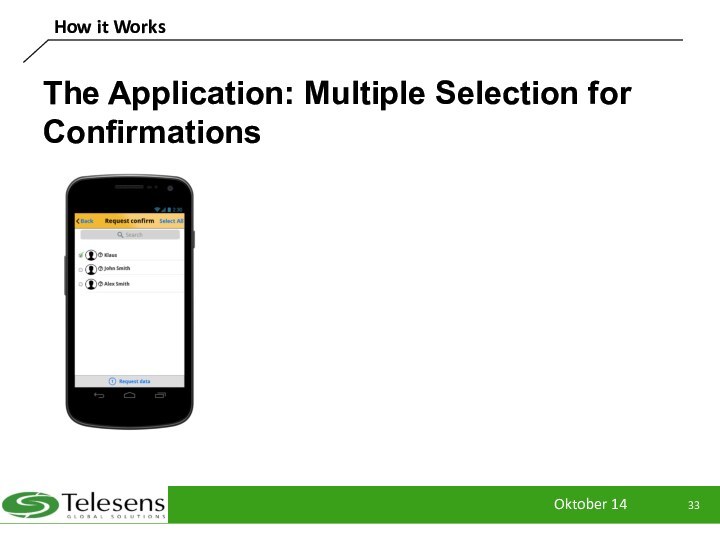
The Application: Multiple Selection for Confirmations
How it Works
Слайд 35
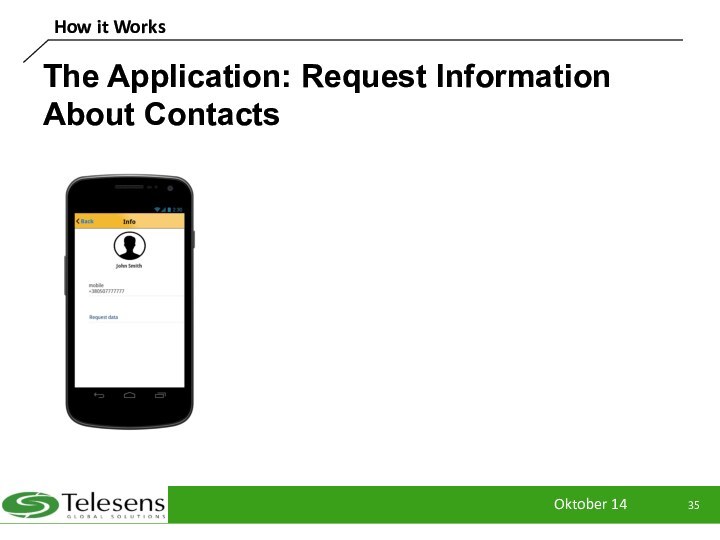
The Application: Request Information About Contacts
How it Works
Слайд 36
The Application: Start New Chat, File Transfer, etc.
How
it Works
To initiate any action, the User has to
identify himself by
Scanning the QR-Code from his personal card
OR
Using a SoftTag to identify himself. A SoftTag can usually be placed on his keychain
One of these security steps has to be completed. Otherwise no action e.g. chat, file transfer, start of an application or payment process is possible.
Слайд 37
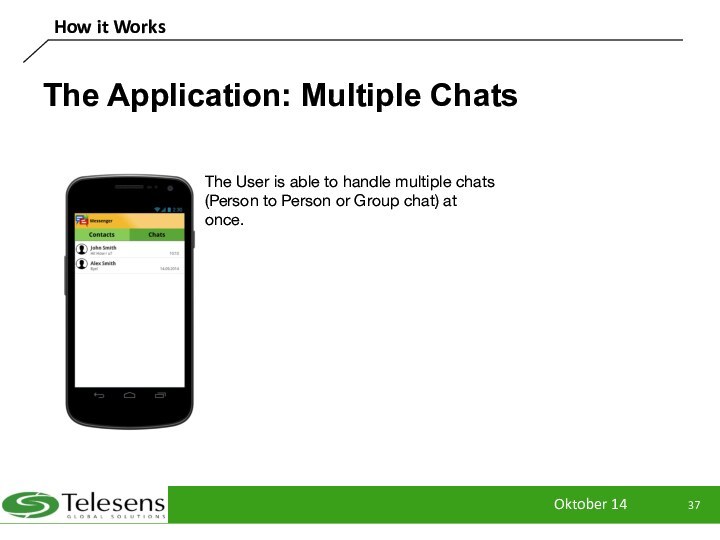
The Application: Multiple Chats
How it Works
The User is
able to handle multiple chats (Person to Person or
Group chat) at once.
Слайд 38
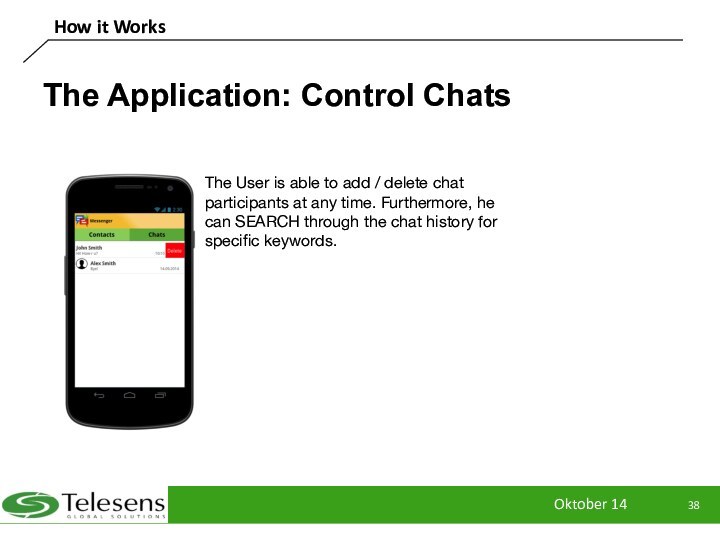
The Application: Control Chats
How it Works
The User is
able to add / delete chat participants at any
time. Furthermore, he can SEARCH through the chat history for specific keywords.
Слайд 39
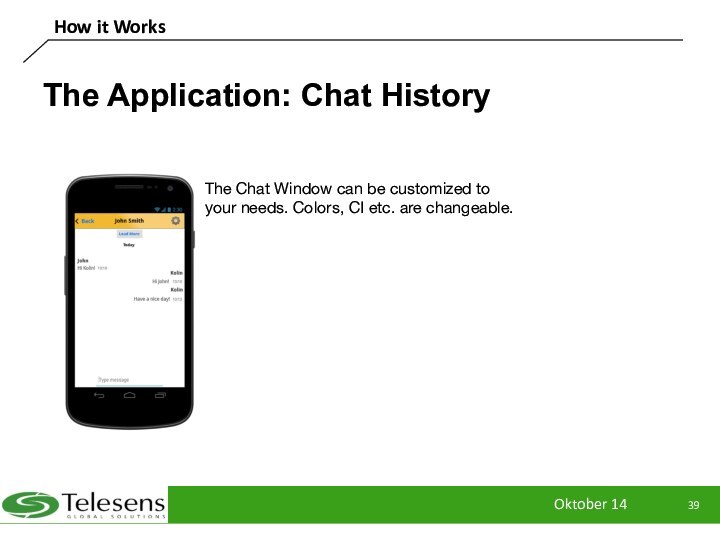
The Application: Chat History
How it Works
The Chat Window
can be customized to your needs. Colors, CI etc.
are changeable.
Слайд 40
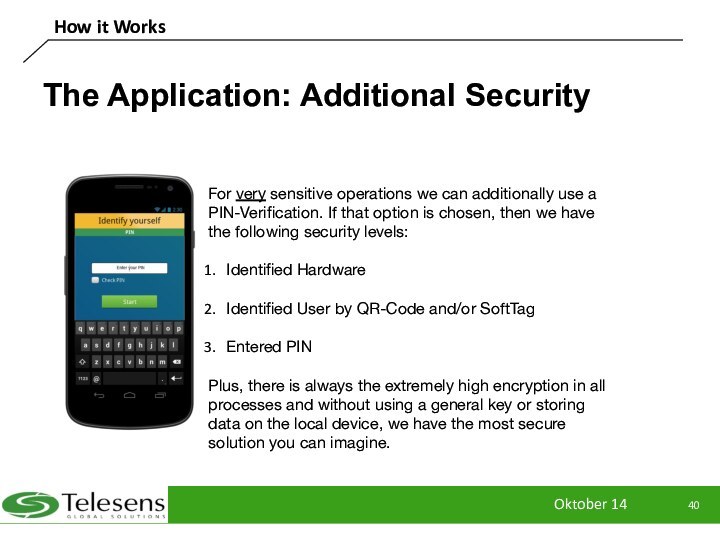
The Application: Additional Security
How it Works
For very sensitive
operations we can additionally use a PIN-Verification. If that
option is chosen, then we have the following security levels:
Identified Hardware
Identified User by QR-Code and/or SoftTag
Entered PIN
Plus, there is always the extremely high encryption in all processes and without using a general key or storing data on the local device, we have the most secure solution you can imagine.
Слайд 41
The Next Messenger Version
How it Works
Voice communication encryption
based on the Notary Server technology
Video communication encryption based
on the Notary Server technology
File Transfers adjusted to your company’s needs (Volume)
Emoticons
Слайд 42
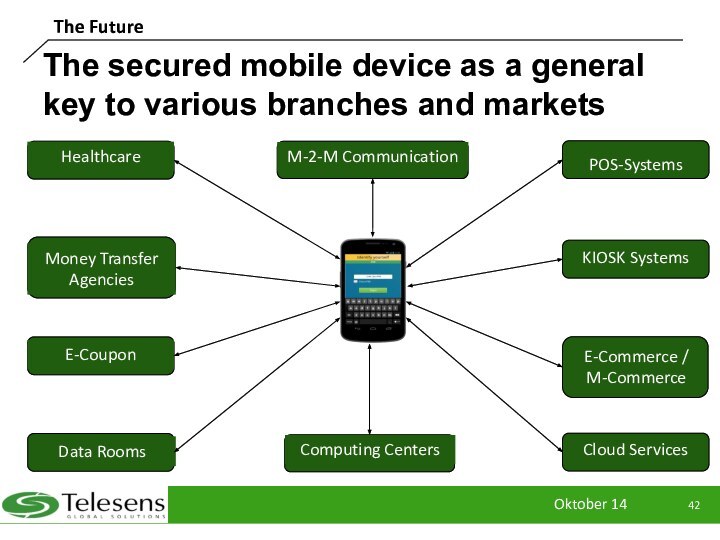
The Future
The secured mobile device as a general
key to various branches and markets
Слайд 43
Who Are We?
Who Are We?
Mr. Eduard Rubin
2012 –
present day: Kharkiv Computer and "Kharkiv Polytechnic Institute“ Director
2010 – present day: "Kharkiv Polytechnic Institute", Computer Aided Management Systems department Associate professor
2009 – present day: Telesens International Ltd.
Founder and CEO
2002 – 2009 : Telesens LLC
Founder and CEO
1998 – 2002 : Telesens AG, Germany
Director od Development Center Ukraine
1995 – 2000 : Intermesse ONLINE
Serving the world’s first online exhibition
Founder and Director
1991 – 1995 : M + R Import / Export GmbH
Export & Import between CIS countries
Founder and Director
1987 – 1991 : Scientific Production Cooperative Sintez
The first private industrial production of computers based on the Z-80
Слайд 44
Who Are We?
Who Are We?
Mr. Eduard Rubin –
Public activities and awards
2011 – present day: Chairman of
Kharkov Branch Board of the European Business Association
2008 – 2010 : Vice Chairman of Kharkov Branch Board of the European Business Association
2007 : Finalist of the competition “Entrepreneur of the Year” elected by Ernest & Young
2006 : Winner of the competition “Entrepreneur of the Year” in the nomination
“Information Technologies” elected by Ernest & Young
2005 : Phd of technical sciences in automated management systems and progressive information technologies. Defended the thesis in Kharkov National Polytechnic University “The Kharkov Polytechnic Institute”
2005 – 2008 : Vice President of the Association “IT”
2002 – present day: Head of Employers Organization “Kharkov Regional Branch of Employers in
Telecommunications”
1998 – present day: Member of the Academy of Computing Sciences in the Ukraine
Слайд 45
Who Are We?
Who Are We?
Mr. Nino Messaoud, Degree
in Commercial Information Techn.
05/2014 – present day: Setup, Preparation
of Director of Telesens Deutschland GmbH i.Gr.
2008 – 2014 : Managing Director of SHD Einzelhandelsgesellschaft mbH & Co. KG
Managing more than 100 employees in one of leading software companies
for ERP Systems (furniture retail)
2007 – 2008 : Al Hamed Enterprises (UAE)
Consulting- and Re-Structuring of the Group of Companies
2006 – 2007 : Conception & Development of the world’s first B-2-B Diamond Trading
System for Antwerp
2003 – 2006 : Various Projects as Head of Consultancy & Development in Kuwait, UAE
1998 – 2002 : Telesens AG, Germany
Head of Business Unit “Post-Billing”
1994 – 1998 : AMS (American Management Systems)
Head of GUI-Development for Mannesmann (today Vodafone) Billing System
1997 – 1997 : Software Developer for various companies (project freelancer), e.g.
GDG Globus Reisen, Deutsche Presse Grosso, AXA Colonia
Слайд 46
Who Are We?
Who Are We?
Telesens Facts & Figures
Internationally
operating Company with Headquarter in London (UK). Germany will
be setup as the European Hub to provide our Customers contracts based on German law in the heart of Europe with two major business units
Products: Telesens Notary Server & Messenger Technologies
Outsourcing projects to Ukraine with German project development (one face to the customer)
15 Years of experience in international product- and project development for telecommunications and other branches with more than 200 successful projects with more than 50 customers worldwide
ISO-Certified processes since 2006
More than 100 highly qualified and top educated analysts, developers, project managers, quality insurance specialists, etc., and a direct link to the University of Kharkov
Silicon Valley - educational, scientific and industrial center founded by Telesens and National Technical University «Kharkov Polytechnic Institute»
Слайд 47
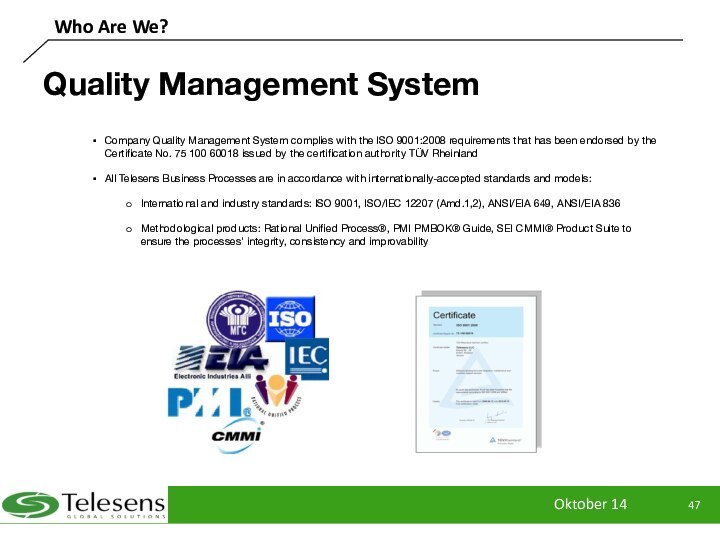
Quality Management System
Who Are We?
Company Quality Management System
complies with the ISO 9001:2008 requirements that has been
endorsed by the Certificate No. 75 100 60018 issued by the certification authority TÜV Rheinland
All Telesens Business Processes are in accordance with internationally-accepted standards and models:
International and industry standards: ISO 9001, ISO/IEC 12207 (Amd.1,2), ANSI/EIA 649, ANSI/EIA 836
Methodological products: Rational Unified Process®, PMI PMBOK® Guide, SEI CMMI® Product Suite to ensure the processes' integrity, consistency and improvability
Слайд 48
Our Technology Skills
Who Are We?
Hardware & Software Platforms
Sun
Sparc (Solaris), HP (Unix), Intel (Windows, Linux)
Software Development Technologies
Java
EE, Microsoft .NET (2.0, 3.5, 4.0), CORBA
DBMS
Oracle, MS SQL Server, Sybase, MySQL, IBM DB2
Programming Languages
Java, C#, C/C++, VB, SQL, PL/SQL, TSQL, PHP
Technologies and Frameworks
ASP.NET (2.0, 3.5, 4.0), ASP.NET MVC
Spring, OSGi, EJB, Hibernate, iBatis, Swing, GWT/Smart-GWT, JSP, JSF, Struts/Tiles
Ajax, HTML, DHTML, XML, XSLT, JavaScript, JQuery, CSS, Iron Speed Designer, MOSS / Sharepoint 2007, 2010
Application Servers
Oracle Weblogic, IBM WebSphere, JBoss, Resin, Apache Tomcat, MS IIS
Tools
Sybase Power Designer, Eclipse, NetBeans, MS Visual Studio, Oracle Data Integrator, Oracle Warehouse Builder, JasperServer, MS SQL Reporting Services, Crystal Reports Subversion, MS VSS, Rational ClearCase, Rational ClearQuest, Atlassian Jira, Apache Maven, Apache Ant, Altova XML Spy, soapUI
Слайд 49
Our Technology Partners
Who Are We?
Слайд 50
Some of our customers
Who Are We?
Слайд 51
Customer Testimonials
„ For Ucell, as fastest growing operator
in Uzbekistan, it‘s very important to have an efficient
tool to manage the interconnect business in order to hold the leading position in tough competition environment. Telesens‘ executives have demonstrated their ability to respond to requests of COSCOM‘s staff in a prompt and flexible way. Ucell is very much looking forward to develop and strengthen our partnership with Telesens.“
Helge Taltanen, CTO FE „COSCOM“ LLC
„Due to their professional competence, the Telesens employees participating in this project were able to get into the new available infrastructure very fast. Both technical and interpersonal communication with them was excellent. The fast synchronization of the development processes was easily achieved. The developed software module is remarkable for ist high quality. The planned functionality was achieved fully within planned timeline and budget. This project can be designated as a 100% success. Therefore we plan to entrust Telesens Ukraine with further projects.“
Chris Steenbergen, Busiess Support Solutions T-Systems Nova GmbH
Customer Testimonials
Слайд 52
Who Are We?
Who Are We?
IT-Services provided by us
Application
Development
Project Solutions
Product Solutions
Software Reengineering
Mobile Applications
Professional Services
Integration and Implementation
Support Services
IT-Resourcing
Dedicated
Project Teams
Dedicated Quality Insurance
IT-Consulting
Management Consultancy
Technical Consultancy
Think-Tank
We operate with some customers “Think Tanks” to invent with them the ideas from tomorrow