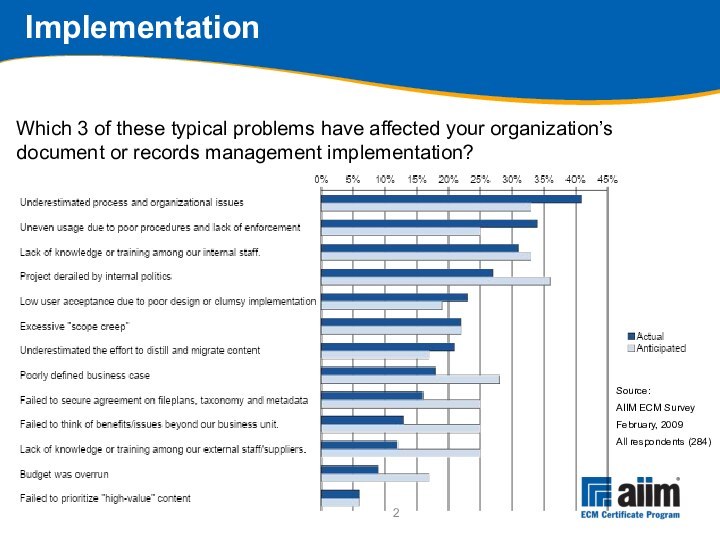
your organization’s document or records management implementation?
Implementation
Source:
AIIM ECM
SurveyFebruary, 2009
All respondents (284)
FindSlide.org - это сайт презентаций, докладов, шаблонов в формате PowerPoint.
Email: Нажмите что бы посмотреть




















© AIIM | All rights reserved
© AIIM | All rights reserved
Scope can be defined across a number of dimensions
Geographic
Organisational
Legacy content
Information types
Information classes
Timescales
Prioritisation is key
© AIIM | All rights reserved
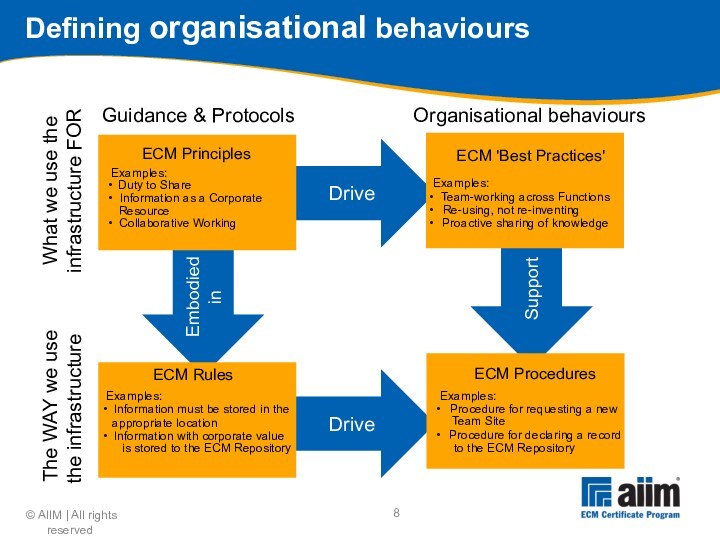
Environment: Develop high-level descriptions of
Organisational behaviours
ECM support organisation structure
ECM processes & instruments
© AIIM | All rights reserved
Assessments
Application portfolio and functionality
Information flow
Information delivery
Information maturity and infrastructure maturity
Economic value of information
Information processes
People skills and organisational structure
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
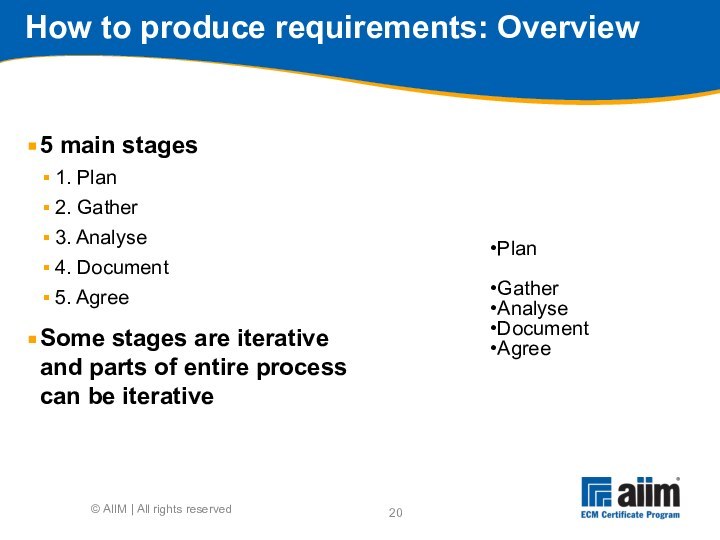
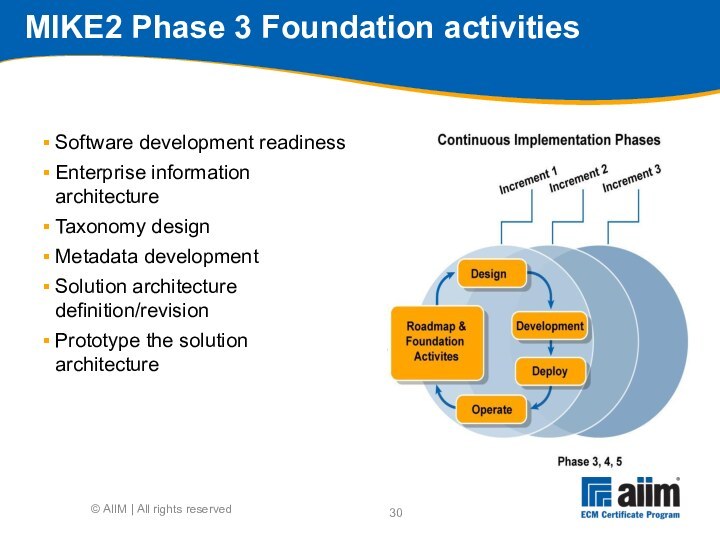
Plan
Gather
Analyse
Document
Agree
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
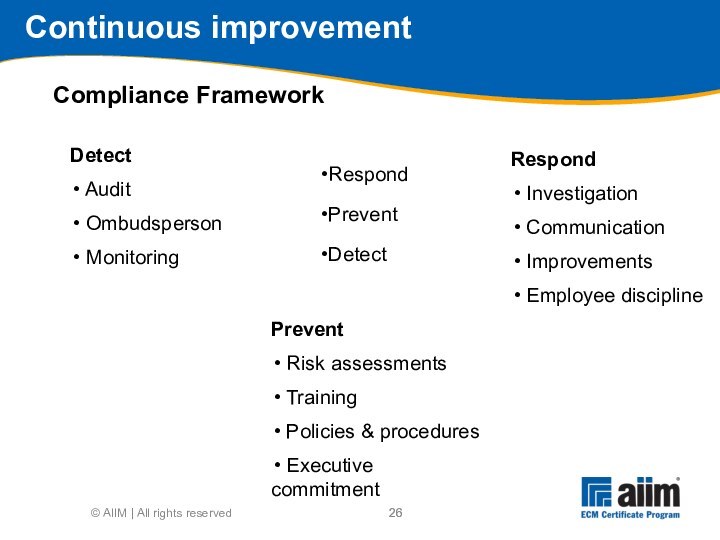
Respond
Investigation
Communication
Improvements
Employee discipline
Compliance Framework
Respond
Prevent
Detect
© AIIM | All rights reserved
© AIIM | All rights reserved
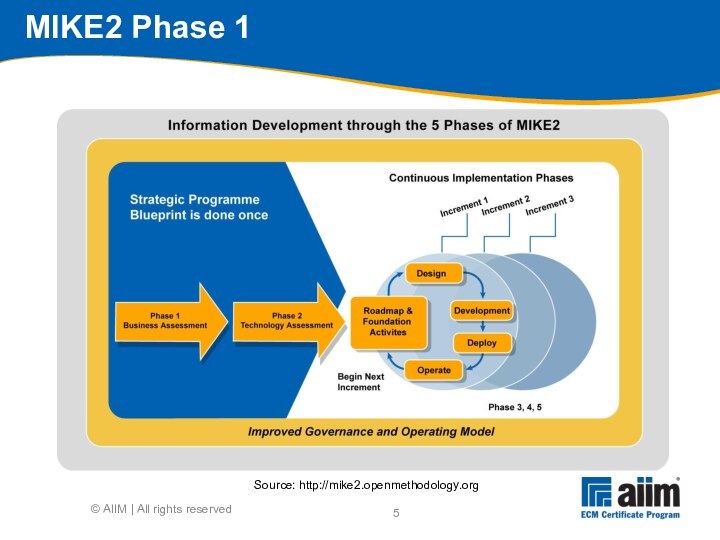
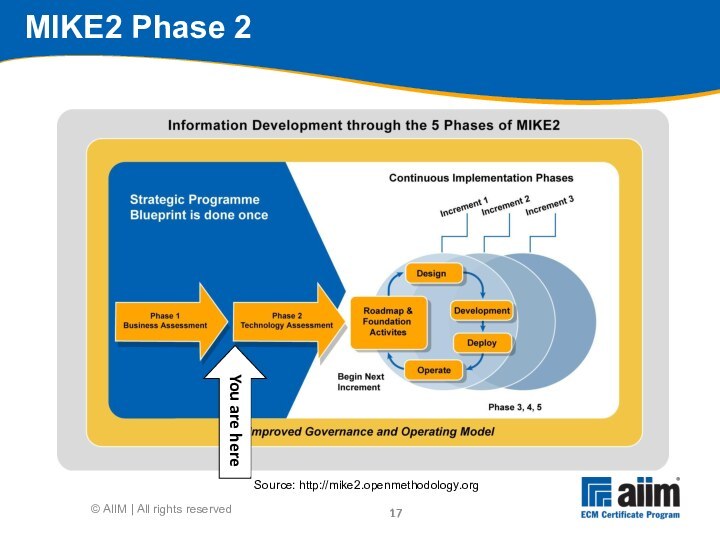
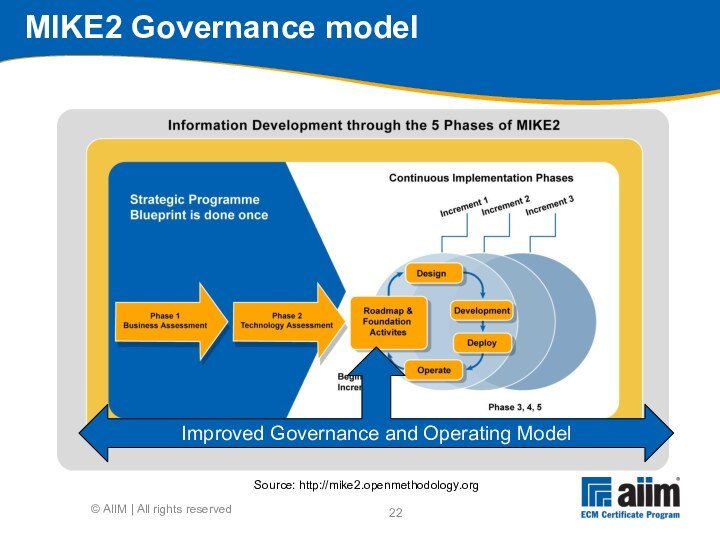
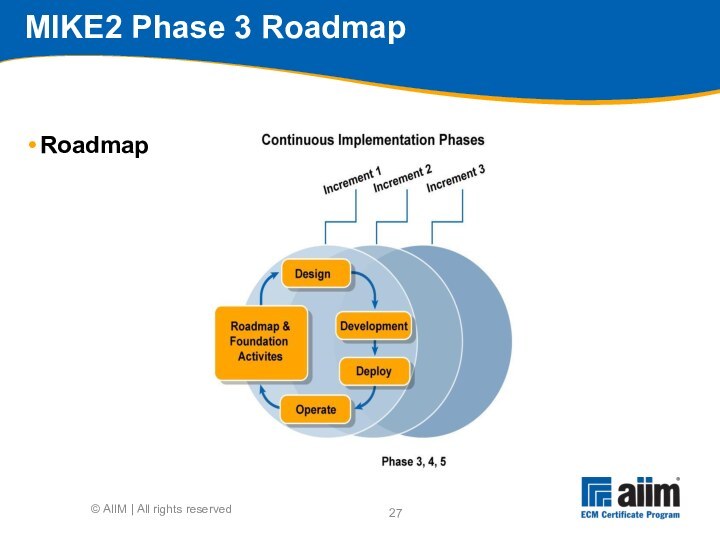
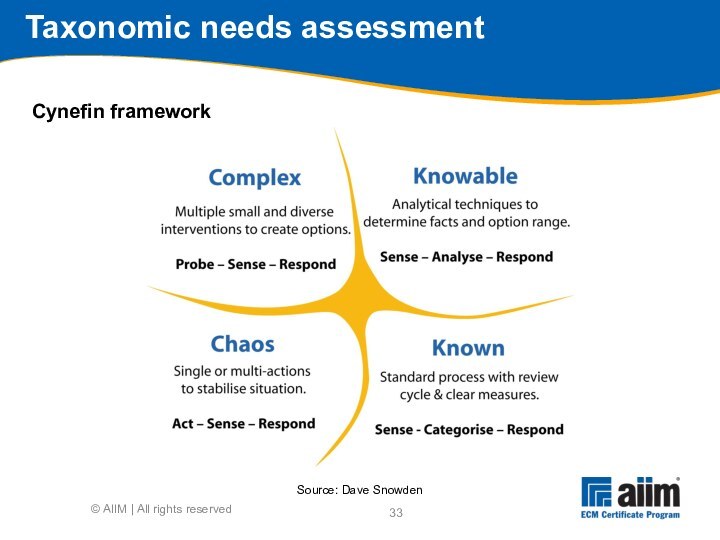
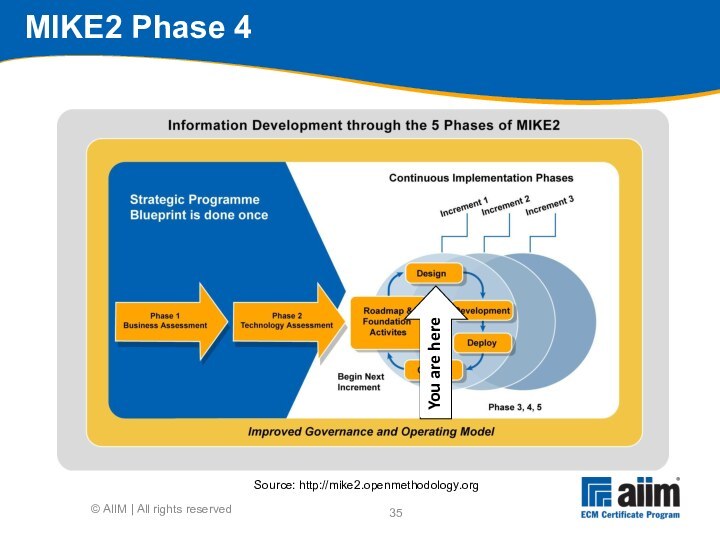
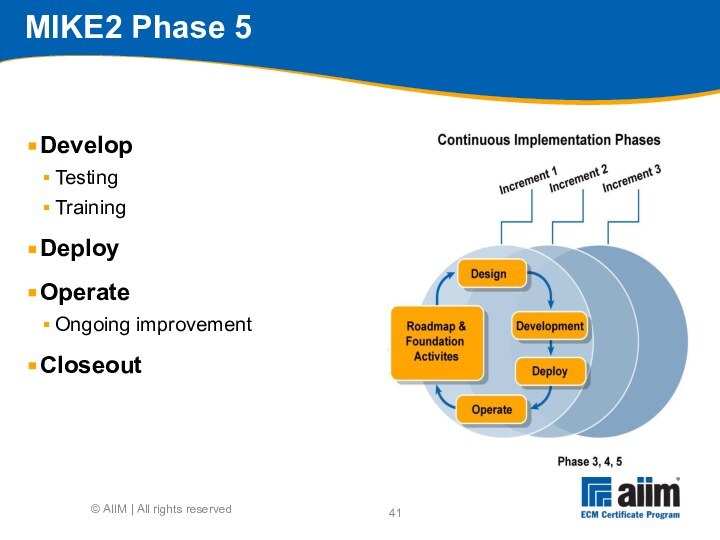
Source: http://mike2.openmethodology.org
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
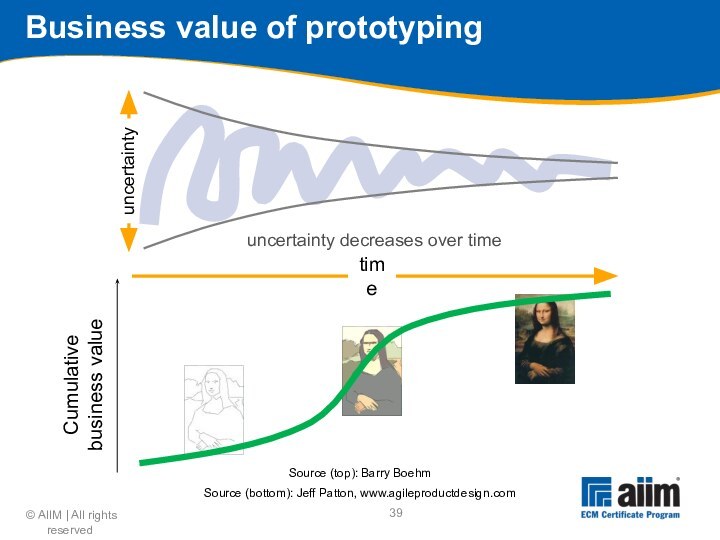
uncertainty
© AIIM | All rights reserved
Job scheduling
Monitoring & logging
Load balancing
Problem management
Change management
Vendor management
Backup/restore procedures for application components
System maintenance
Print services
Failure
Appendix A - User account setup process & access rights
Appendix B - Service level agreements
Appendix C - Contact matrix
Appendix D - Software versions list
© AIIM | All rights reserved
Source: http://mike2.openmethodology.org/wiki/Operations_Procedure_Outline_Deliverable_Template
© AIIM | All rights reserved
© AIIM | All rights reserved
Finalise environment
Ensure all aspects of environment are defined
Establish and ‘freeze’ a configuration for roll-out
Training development
Develop and assess training materials and methods
Train the trainers, help desk staff, floor-walkers
etc.
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved
© AIIM | All rights reserved