to provide an understanding of the variety and complexity
of threats in the current enterprise IT environment.After completing this module, you should be able to understand:
A high-level overview of recent major incidents and the worldwide modern threat landscape, based on data and figures from IBM’s X-Force Threat Research.
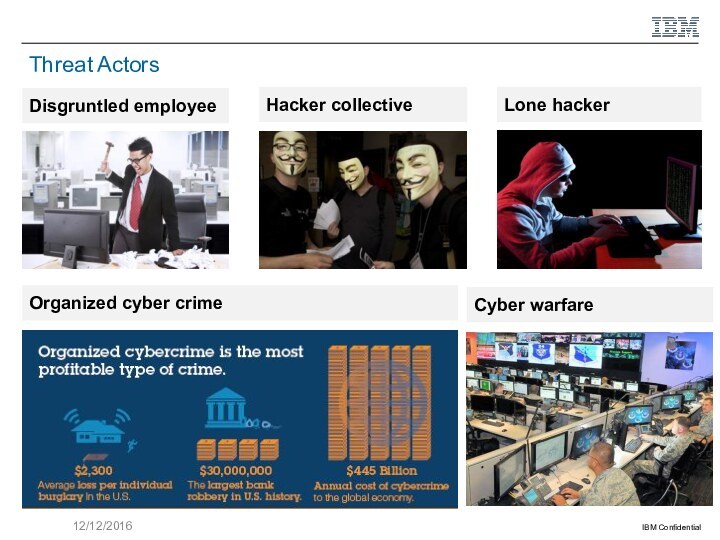
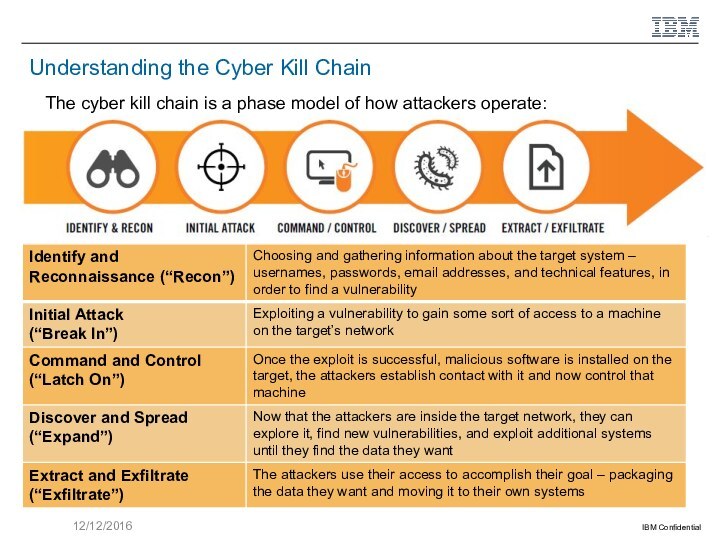
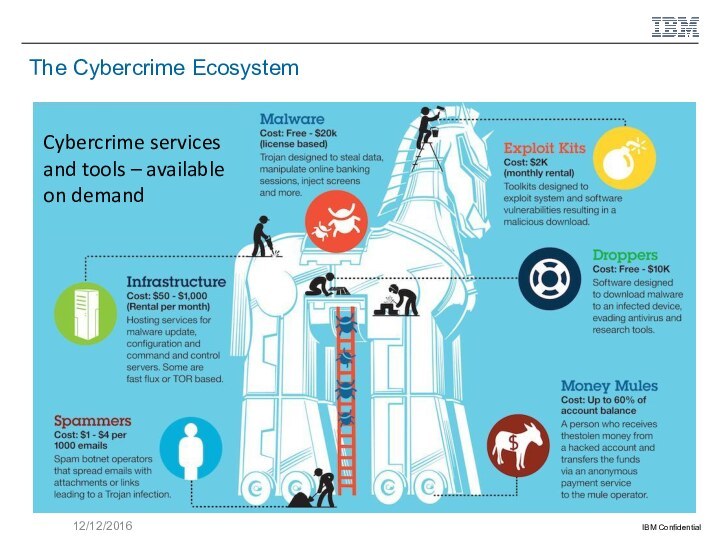
Additional use cases of related concepts such as organized cyber crime, cyber crime on demand, Advanced Persistent Threat attacks, and the Cyber Kill Chain approach.
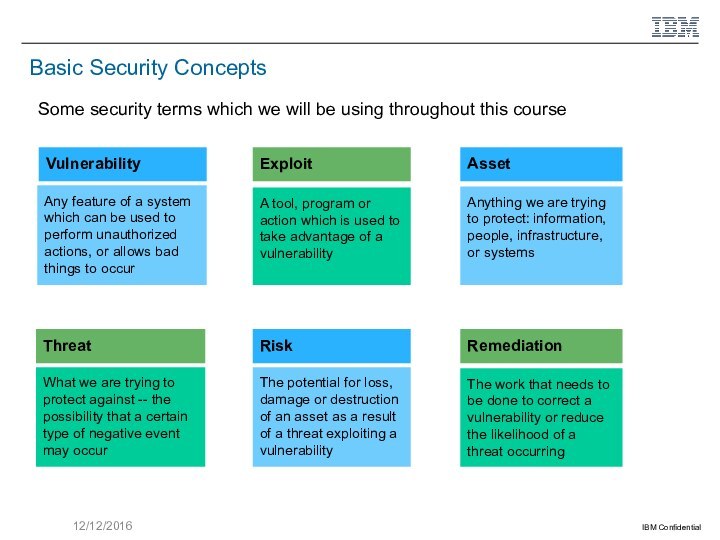
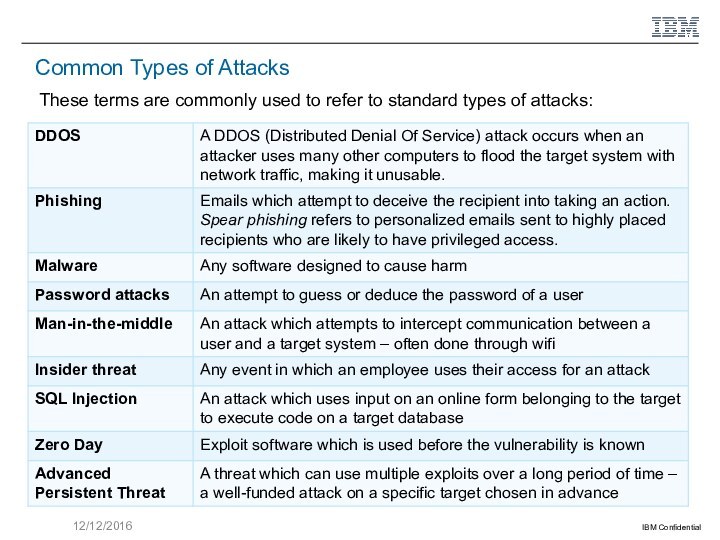
The tools and techniques used by attacks, reviewing such concepts as Vulnerability, Exploit, and Remediation; DDOS, SQL Injection, Watering Hole attacks, Insider threat, and Zero Day attack.