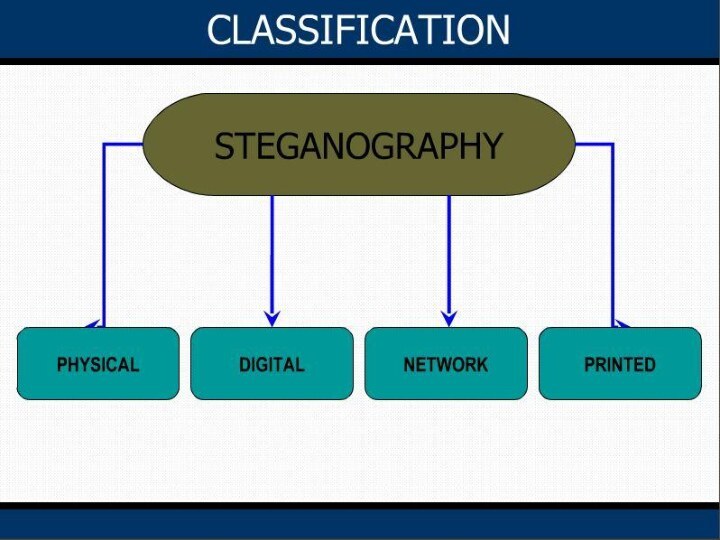
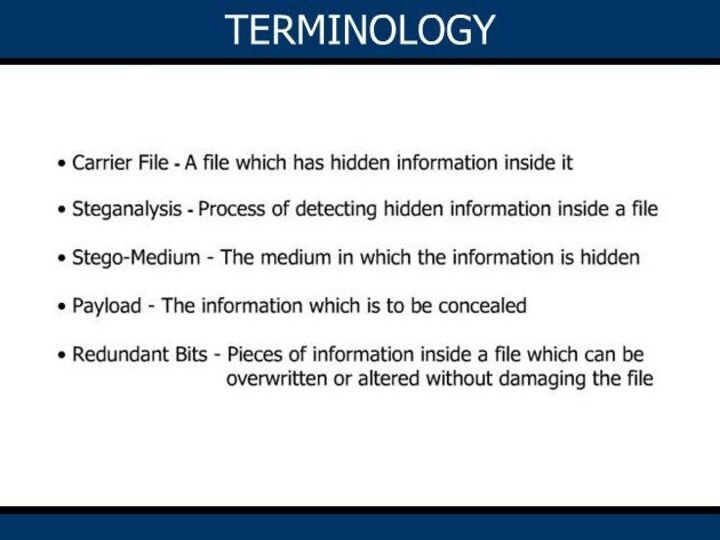
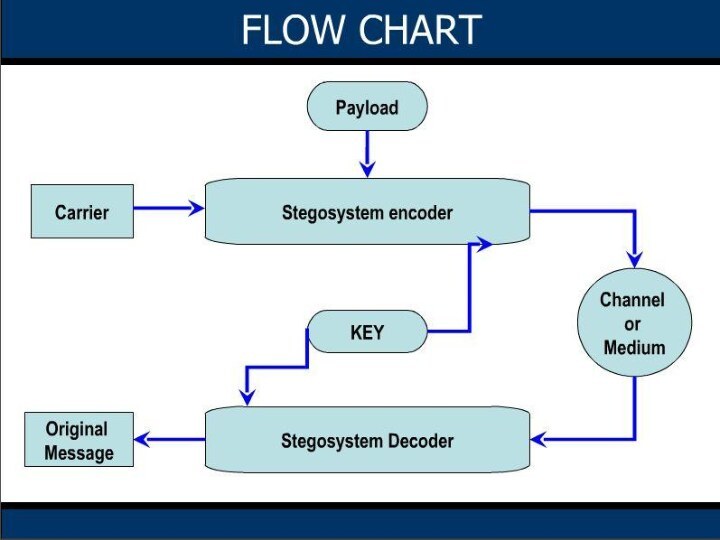
process
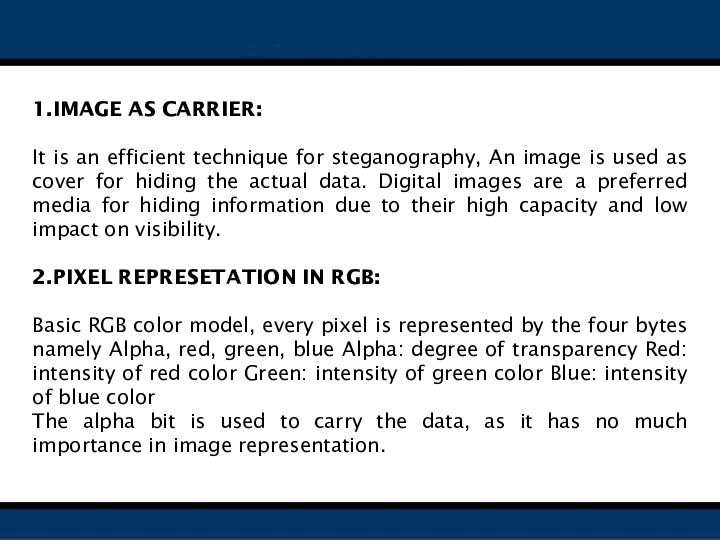
Image as a carrier
Pixel representation in RGB
Bandwidth reduced file
transferUsage and Future application
Modern printers
Water marking
Future application
Conclusion
Table of Contents