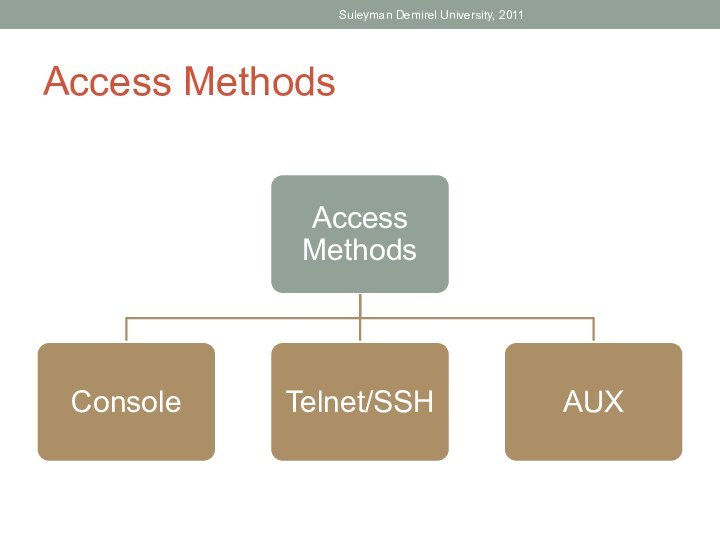
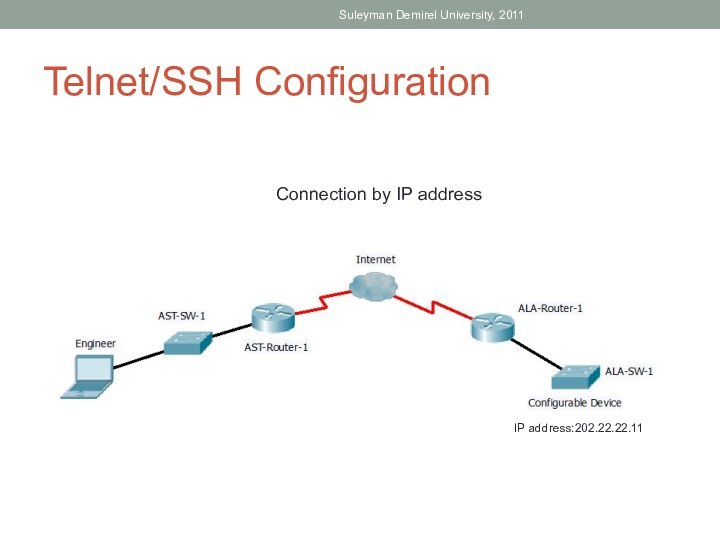
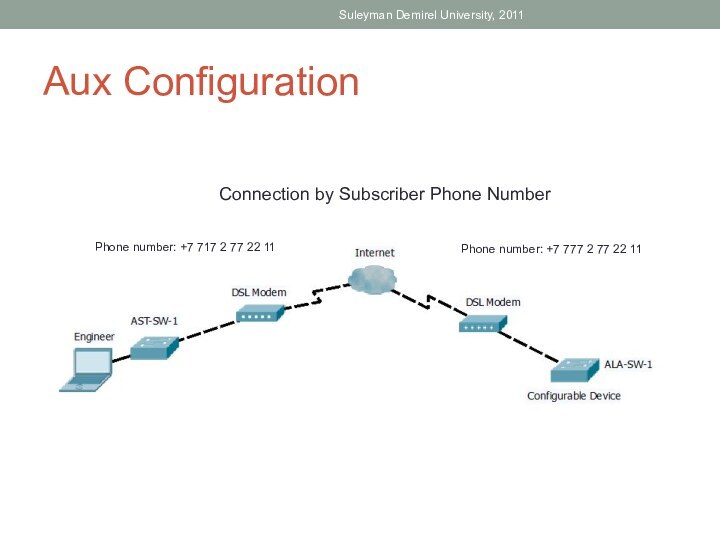
able to:
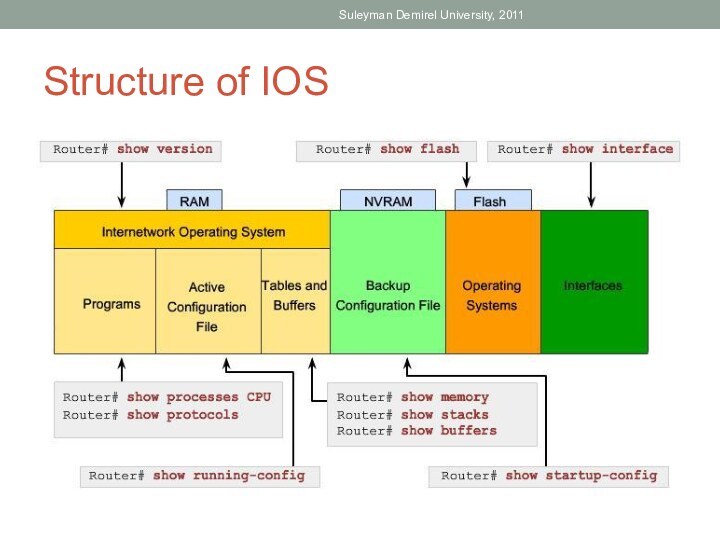
Define the role of the Internetwork Operating System
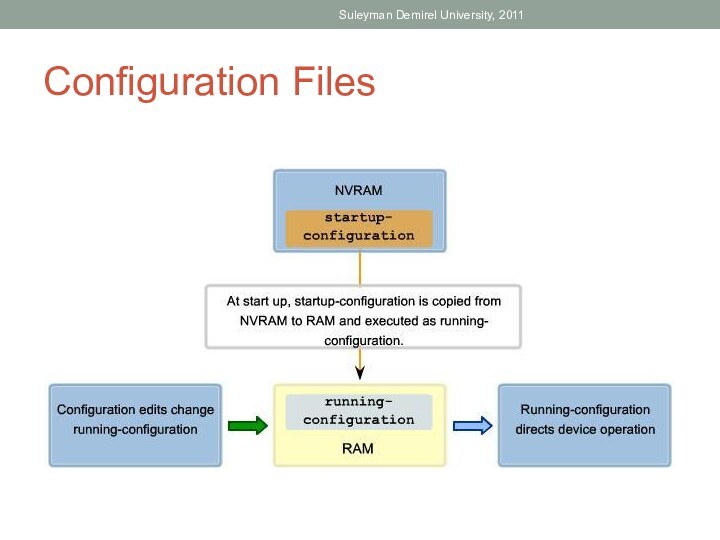
(IOS).Define the purpose of a configuration file.
Identify several classes of devices that have the IOS embedded.
Identify the factors contributing to the set of IOS commands available to a device.
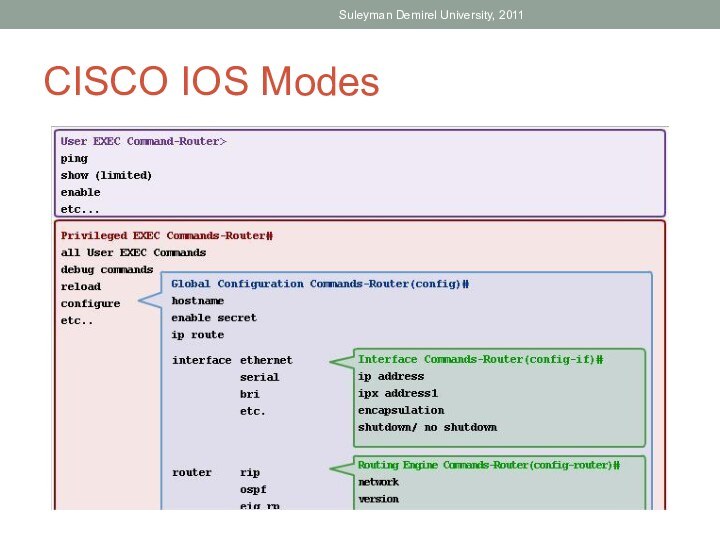
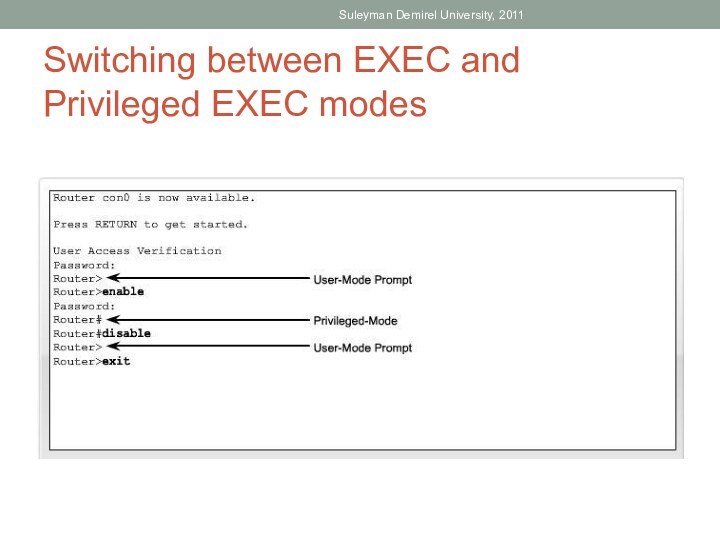
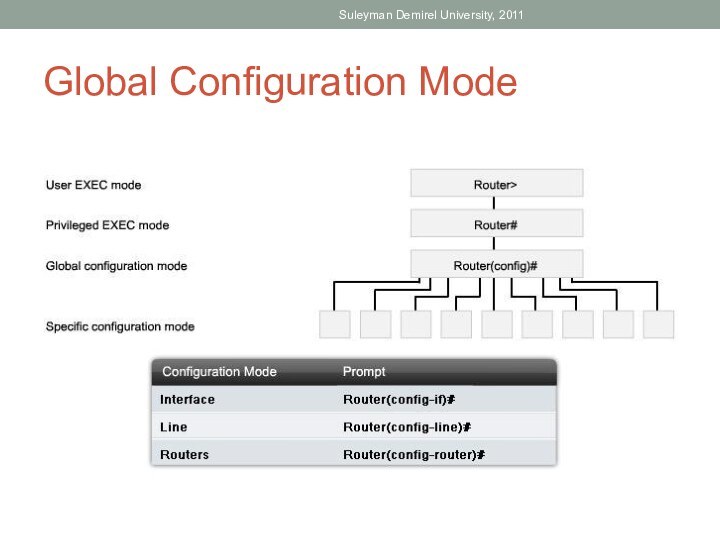
Identify the IOS modes of operation.
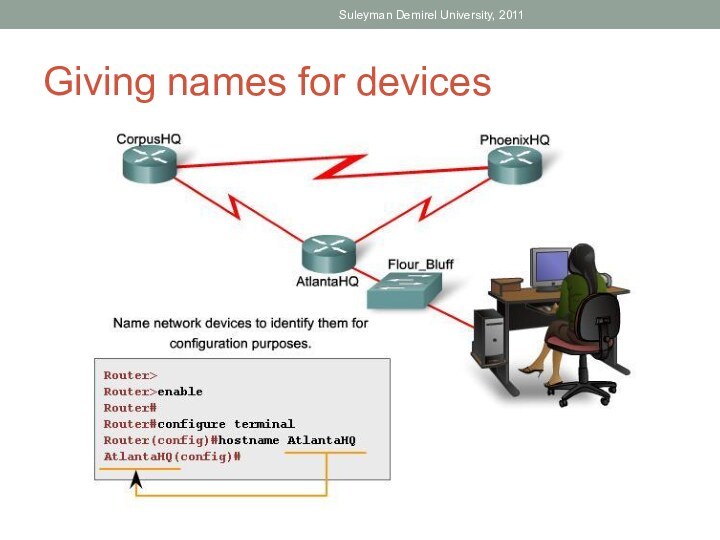
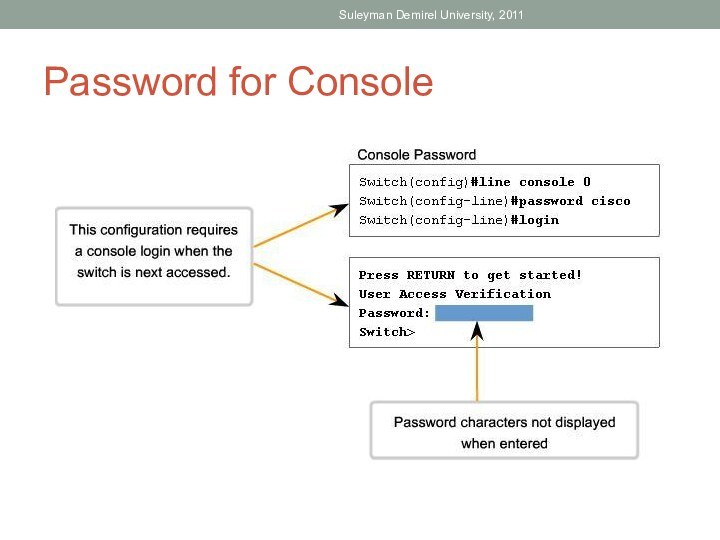
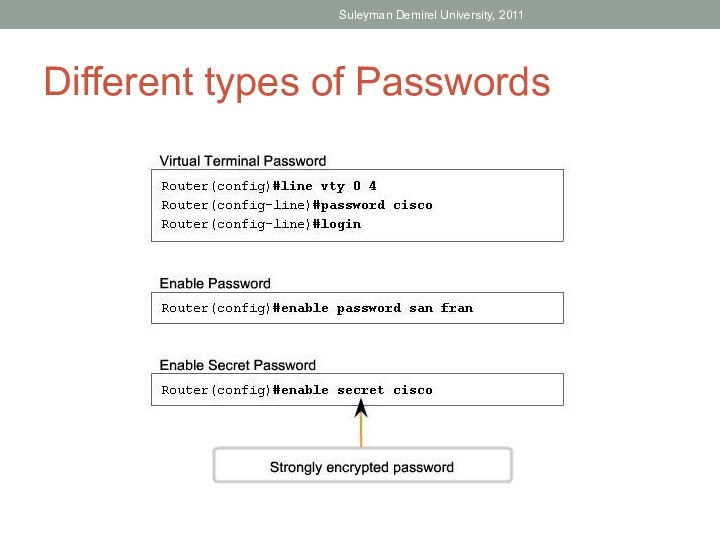
Identify the basic IOS commands.
Compare and contrast the basic show commands.
Suleyman Demirel University, 2011